

ConnectedGRC
Drive a Connected GRC Program for Improved Agility, Performance, and Resilience
-
BusinessGRC
Power Business Performance and Resilience
Discover ConnectedGRC Solutions for Enterprise and Operational Resilience
Explore What Makes MetricStream the Right Choice for Our Customers
Discover How Our Collaborative Partnerships Drive Innovation and Success
- Want to become a Partner?
Find Everything You Need to Build Your GRC Journey and Thrive on Risk
Learn about our mission, vision, and core values
Strengthen IT Auditing with COBIT
As businesses increasingly adopt cloud, virtualization, and mobile technologies, they are grappling with a growing number of sophisticated IT security threats and risks. It has become imperative to strengthen IT governance and audit processes, to ensure the integrity of information systems. COBIT helps business and their IT managers achieve these, and build a powerful, integrated framework for IT governance, control and audit processes.
Achieving IT Control Objectives with COBIT 5
COBIT, or the Control Objectives for Information and Related Technologies, was drafted to "research, develop, publicize, and promote an authoritative, up-to-date, international set of generally accepted IT control objectives for day-to-day use by business managers and auditors."
COBIT 5, the latest version of the control objectives, aims to achieve the following:
- Help enterprises derive optimal value from IT by maintaining a balance between realizing the desired benefits, and optimizing risk levels and resource use
- Enable information and related technology to be governed and managed in a holistic manner across the enterprise
- Integrate business and functional areas of responsibility with IT-related interests of all stakeholders
The Evolution of COBIT
Since it was first established, COBIT has gone through several revisions. COBIT 5 packs in more punch by integrating the best features of the earlier versions.
The first and second editions, released in 1996 and 1998 respectively, focused on control objectives, and were based on a purely IT control and audit framework. The third version (2000) was an IT management framework which incorporated management guidelines.
IT governance became the guiding force behind COBIT 4.0 (2005) and 4.1 (2007), with the inclusion of governance and compliance processes, and removal of assurance processes.
With COBIT 5, businesses have a framework that:
- Incorporates new Governance of Enterprise IT (GEIT) principles
- Focuses more on enablers
- Draws from a new process reference model
- Factors in a new and modified set of practices, processes, and activities
- Has a pool of goals, metrics, inputs, and outputs
- Includes Responsibility, Accountability, Consultancy or Informational (RACI) Charts
- Provides process capability maturity models and assessments
COBIT 5 comprises five principles and seven enablers which are generic and designed to cater to the requirements of a range of commercial, financial, and not-for-profit enterprises.
The five principles are as follows:
- Meeting stakeholder needs
- Covering the enterprise end-to-end
- Applying a single integrated framework
- Enabling a holistic approach
- Separating governance from management
The seven enablers facilitate the introduction and implementation of COBIT 5 principles. These enablers are as follows:
- Principles, policies, and frameworks which offer guidance for routine management of issues
- Processes which help reach the stated overall goals
- Organizational structures which often decide the main strategy driving the enterprise
- Culture, ethics and behavior which play an important role in any enterprise, and vary across the company and its international operations
- Information which, if harnessed at the right time and in the right way, can result in maximum benefits for all stakeholders
- Services, infrastructure, and applications
- People, skills and competencies which together help ensure a strong competitive advantage and success in the long run
COBIT 5's Navigation Aids
The COBIT 5 conceptual framework can be approached from three vantage points: Information criteria, IT resources, and IT processes.
The information criteria describe the requirements for information effectiveness, efficiency, confidentiality, integrity, availability, compliance, and reliability. The IT resources are defined to help meet business requirements, and include people, applications, technology, facilities, and data. The IT processes in this context are planning and organization, acquisition and implementation, delivery and support, and monitoring.
How can organizations ensure that the output of their IT resources and IT processes match the information security criteria established for meeting key business objectives? This is where COBIT 5's sound internal control framework comes into play. COBIT 5's navigation aids link the processes, resources, and criteria to 34 overall control objectives with 318 detailed control objectives.
The navigation aids function together in the following way:
The control of IT processes - which satisfy the business requirements, and is in turn enabled by control statements, and takes into consideration control practices.
COBIT 5 from an Audit Manager's Perspective
COBIT 5 is not only a cost-efficient approach, but also a conceptually easy framework for auditors to understand and communicate to the management. COBIT 5 moves away from the "maturity models" in COBIT 4.1, to "Process Capability Model".
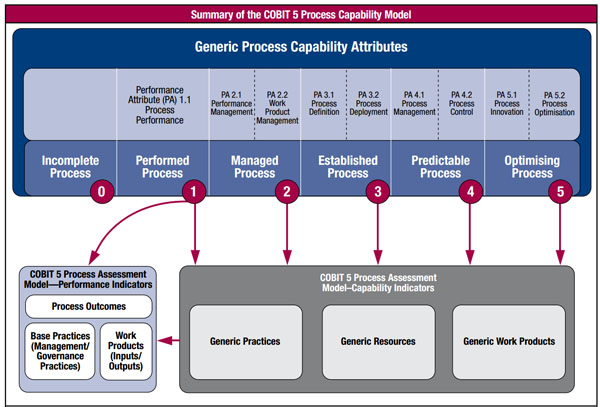
The key is to thoroughly understand "what" the control objectives are. It's very difficult to evaluate the effectiveness of controls unless one is clear about what those controls are meant to achieve. A typical example to illustrate this point is that of "a lock on a door." How does one know if the lock is a good control or not? It depends on whether the objective of the lock is to keep people out or in. Only if this is known, will one be able to determine which side of the door the key should be on.
Similarly, IT controls can be better monitored and audited when the objective behind the control is clear. The advantage of COBIT is that it helps determine these objectives. Therefore, instead of waiting for an audit, businesses can implement controlled self-assessments, where management can themselves evaluate the efficiency of the control structure. COBIT 5 has only one control objective: Enterprise goals should be achieved.
The process capability model as outlined in COBIT 5 has a number of benefits for auditors. This includes enhanced usability, reliability as well as frequency of process capability assessment initiatives. It also provides a strong base for conducting more rigorous assessments, as well as reducing the disagreements between stakeholders on assessment results.
COBIT 5 as an Overarching Corporate Governance Integrator
COBIT 5 aligns with the latest international standards and frameworks, including enterprise frameworks such as COSO, ISO/IEC 9000, ISO/IEC 31000, and IT-related frameworks such as ISO/IEC 38500, ITIL, ISO/IEC 27000, TOGAF, PMBOK/PRINCE 2, and CMMI. This allows enterprises to use COBIT 5 as the overarching governance and management framework integrator.
Information Systems Audit and Control Association (ISACA) is now planning to facilitate COBIT user mapping of practices and activities to third-party references, to enable effective control management without duplication of effort.
How COBIT Fits in with COSO and SOX
Organizations are obligated to achieve SOX compliance in financial reporting and auditing. The COSO control framework offers a roadmap for the same by providing five crucial components, namely: information and communication, which drive the control activities through a thorough risk assessment process, in order to maintain the desired control environment. The whole cycle is monitored to ensure ongoing compliance.
In this context, COBIT provides additional detailed guidance for IT. The five components of COSO can be visualized as the horizontal layers of a three-dimensional cube, with the COBIT objective domains - "plan and organize, acquire and implement, deliver and support, and monitor and evaluate" applying to each.
The cube enables good mapping between COBIT's risk management framework and COSO components. Ultimately COBIT fits the bill perfectly in building upon COSO and SOX.
A Detailed Look at Internal Control Components
The following five internal control components interact with each other and are integrated with the management process. They must be embedded seamlessly into the operational activities of the organization.
1. Control Environment
This forms the basis for the rest of the components. Consider the simplest control in IT, the password. Any user has to fully comprehend the need for a password, to help the password work effectively. Similarly, it's important that everyone in an enterprise recognizes the vital need for a control environment.
The various elements of a control environment include:
- Integrity and ethical values
- Employee competence
- Management's philosophy and operating style
- Assignment of authority and responsibility
- Organization and development of human resources
- Management's direction
2. Risk Assessment
An ever-changing internal and external environment results in risks of varying levels. Risk and innovative initiatives cannot be wholly separated from each other. The trick is not to worry about eliminating risks but to manage them diligently and intelligently.
So what should the game plan be? First, a business must identify and link all consistent goals that drive the entire organization and its business units. Then, it must zero in on the risks that can have an impact on these goals. Finally, it has to develop a clear roadmap to manage these risks, and limit them to acceptable levels.
3. Control Activities
Enterprises need to put in place policies, procedures, and concrete measures to ensure that risks do not sabotage the organization's objectives. These measures include authorizations, verifications, reconciliations, segregation of duties, and operational profitability reviews.
4. Information and Communication
The information required to run a secure control environment can be broadly classified as:
- Financial or operational
- Gathered from internal or external sources
The relevant information must be accurately identified, captured, and communicated to all stakeholders. Appropriate communication channels should be employed to target various stakeholders, and employees should be adequately educated about their individual roles in the internal exercise.
5. Monitoring
Does the internal control system function as intended over a period of time? Does it evolve continuously in sync with the changing business environment? This kind of a systematic review forms the backbone of any dynamic system. The frequency of these regular reviews is decided according to the criticality of the risks involved.
Enterprises should also resort to a gap analysis to assess their security standards. They can mark themselves against different COBIT levels to understand where they stand, and what higher levels they are aspiring for.
Technology as an Enabler
A single, centralized technology system can support COBIT 5 compliance by harmonizing COBIT controls across IT governance and regulatory compliance requirements such as HIPAA and PCI DSS. It can also help build a centralized COBIT library that can be leveraged for processes such as risk and control assessments, and policy mapping.
More importantly, a centralized system can help streamline the entire IT audit workflow - right from audit scoping, planning and scheduling, to reporting, and issue management. Automated capabilities, if present, can help accelerate and improve the efficiency of processes such as notifying auditors of task assignments, or generating reports.
The key is to try and enable a systematic and organized process for each aspect of auditing. For instance, with audit scoping, it is useful to have a system that can help enterprise-wide auditable entities to be defined and managed in a hierarchical, tree-like structure with a clear understanding of roles and responsibilities.
As organizations embrace risk-based auditing, they are rapidly adopting systems that can simplify risk assessments and computations based on specific methodologies and algorithms. This allows auditors to clearly determine areas of high risk, and accordingly prioritize audits instead of trying to audit all areas at once.
When it comes to audit planning and scheduling, the auditing system should help audit managers view enterprise-wide IT auditing requirements, as well as auditor profiles and qualifications, and accordingly allocate task assignments and resources. Centralized dashboards can help in tracking and managing these plans and schedules efficiently.
In the project management stage, portable technical devices can be leveraged to enter field data, and sync it with the central audit management system for optimal efficiency.
A robust audit work-paper management system can enable an integrated and collaborative approach to preparing, organizing, referencing, reviewing, and retaining work-papers created during audits. Such a system can also help in sharing audit information, and synchronizing audit activities across the enterprise.
Reporting technology should also be leveraged wherever possible to improve the efficiency and effectiveness of audit reporting. An advanced reporting system can provide real-time and enterprise-wide views of audit processes and results through advanced dashboards. This information is extremely valuable for stakeholders and the leadership to make informed and actionable decisions.
Conclusion
Ingraining COBIT 5-based auditing into the organizational DNA is critical to building a secure IT environment that is closely aligned to changing business realities. Organizations that establish a COBIT-oriented auditing approach are better positioned to comply with IT regulatory requirements in a sustainable manner, and drive better value for their enterprise.

Subscribe for Latest Updates
Subscribe Now





