ConnectedGRC
Drive a Connected GRC Program for Improved Agility, Performance, and Resilience
-
BusinessGRC
Power Business Performance and Resilience
Discover ConnectedGRC Solutions for Enterprise and Operational Resilience
Explore What Makes MetricStream the Right Choice for Our Customers
Discover How Our Collaborative Partnerships Drive Innovation and Success
- Want to become a Partner?
Find Everything You Need to Build Your GRC Journey and Thrive on Risk
Learn about our mission, vision, and core values
A Leading Financial Services Organization Enables a Fully Unified, Streamlined, and Consistent Process for Threat and Vulnerability Management
The Client: A Leading Financial Services Organization
Overview
As business operations scale up and become increasingly dependent on Information Technology (IT), IT environments will continue to become more complex, exposing organizations to a wide array of risks, threats, and vulnerabilities that have a direct impact on the performance of the enterprise.
Information security is becoming an increasingly big concern, as recent high-profile breaches at leading organizations have demonstrated. Adding to the challenge, several government regulations focusing on information privacy and security have emerged in recent years to safeguard consumer information, and ensure corporate accountability.
Many companies see the value of using technology to build and sustain robust information security and IT risk management programs that will protect them from emerging cyber threats, and help them comply with the full range of IT regulations. One such company was the client who opted to leverage MetricStream IT GRC Solution to strengthen its overall information security, risk, and compliance management program.
Solution
After an extensive evaluation of various solutions in the market, the client selected MetricStream IT GRC Solution to streamline, integrate, and enhance its information security risk management processes, including threat and vulnerability management, asset management, risk management, issue management, regulatory compliance, and reporting.
The client chose MetricStream for its robust platform architecture coupled with its comprehensive functional applications, all of which would enable the organization to manage its IT regulatory compliance requirements in an integrated manner, while driving forward a culture of proactive IT risk management. The solution would be used by information security teams across the organization’s worldwide operations.
Below in greater detail are the key processes enabled and supported by the MetricStream solution:
Defining, classifying, and grouping assets
The MetricStream solution helps capture all IT asset information either manually or through integration with third-party systems. This information is consolidated in a centralized repository in a many-to-many manner for easy reference.
The solution also offers the flexibility to categorize and classify IT assets based on multiple factors such as Confidentiality, Integrity, and Availability, as well as business impact, operational or financial asset groups, functional and technical capabilities (e.g. ecommerce servers categorized together for PCI compliance), mission critical requirements, industry standard classifications, or any other user specific requirements.
Using the solution, users can define assets/asset groups, and conduct IT risk assessments and computations based on configurable asset scoring methodologies and flexible what-if analysis functionalities.
Users can also utilize a library of assessment questions for surveys based on control statements and procedures. These questions are mapped to various regulations, standards, and frameworks to drive powerful risk and compliance reporting. Based on the information gathered, the asset criticality can be determined.
MetricStream also integrates with MITRE CPE, enabling assets to be mapped to these industry standard classifications.
| Asset Exposure | ||||
| Asset Classification: | Standalone asset with limited or no network connectivity | Asset with network visibility that is limited to internal networks | Asset with network visibility that is available to a broader audience but is not Internet facing | Asset with network visibility that is available over the Internet |
| HIGH: Confidentiality: System contains non-public sensitive data Availability: System requires high availabilityIntegrity: System transmits, processes, or stores sensitive data that either may be used to make significant business decisions, or is important to the business function of the client | Medium | High | Critical | Critical |
| MODERATE: Confidentiality: System contains data with an unknownclassification Availability: System can experience some downtime or limited availability outside of normal businesshours Integrity: System contains data that is important to the business function of the client | Low | Medium | High | Critical |
| LOW: Confidentiality: System does not contain sensitive data Availability:System can experience extended downtime or no availability outside of normal business hours Integrity:System does not transmit, process, or store data that is sensitive or important to the business function of the client | Low | Medium | High | High |
Sample Asset Criticality Assessment Criteria
Identifying threats to assets, and establishing security baselines
The MetricStream solution provides a comprehensive repository of threats consolidated automatically from real-time authoritative sources such as the National Vulnerability Database, commercial threat feeds, email advisories, and multiple zero-day and early warning services. This threat intelligence can be used to efficiently define and classify threats based on their impact on and context to the organization. Threats can also be defined based on vulnerability types, malicious code, geopolitical threats, patch levels, exploitation availability, and access type or complexity.
In addition to these parameters, the client uses Center for Internet Security (CIS) benchmarks for establishing asset security configuration baselines which are compared against assessment findings from configuration assessment tools.
Integrating information on asset vulnerabilities, and mapping them to the relevant assets
The MetricStream solution has a built-in central repository/database and a data integration engine which can be configured to integrate with any third-party threat and vulnerability management systems. The solution extracts relevant threat and vulnerability data from these systems, and stores it in a central database with easy access and search capabilities. Each of the vulnerabilities are automatically mapped to assets based on pre-defined criteria such as IP address.
Using the MetricStream solution, the client enables a consistent and repeatable threat and vulnerability management process. The solution also provides an easy way to harness massive amounts of security data, correlate it with other risk and compliance metrics, and transform it into meaningful dashboard reports to make informed decisions when vulnerabilities occur.
Configurable automatic notifications are sent to users, containing the complete details of each vulnerability, including its severity, CVE ID, source, affected technologies, available controls, and possible remediation instructions.
Calculating IT risk
The MetricStream solution enables the client to calculate IT risks using inputs from risk self-assessments, asset and vulnerability risk scores, and asset mapping. Built-in risk scoring methodologies from ISO, CVSS, NIST, ISF, and Octave help provide a clear overall risk score.
The solution also helps define a personalized risk scoring methodology to determine the overall risk, urgency, and priority of response.
Sample Risk Assessment Factors
- Number of potentially impacted systems (servers/clients)
- Access gained (DoS, local, remote)
- Deployment size of affected technology
- Value of target (network, critical service, OS, App, BU, etc.)
- Level of access gained by exploit
- Remotely exploitable
Sample Threat Scoring Implementation Methodologies
- Compare DREAD classification to threat types
- Associate STRIDE classifications based on exploit type
- Import CVSS v2 base and temporal scores + Add customer specific environmental score
Testing IT controls
MetricStream IT-GRC Solution includes the Unified Compliance Framework (UCF) -- an IT controls library comprising over 5,000 control statements. UCF leverages commonalties running across various regulations and frameworks (e.g. PCI, ISO/ IEC 27000:2005, COBIT, SOX, NIST) to provide a “harmonized” set of common controls statements. This enables the client to reduce compliance testing efforts by testing one “harmonized” control (instead of many controls), and mapping the results back to multiple regulations.
Correlating and visualizing threats
The MetricStream solution provides a structured overview of the security environment, including all system vulnerabilities, their interrelationships, and their interaction with security or non-security components. Administrators can visualize attacks against a system/ asset group, in the form of a simple tree structure, and thereby minimize exposure to threats and vulnerabilities.
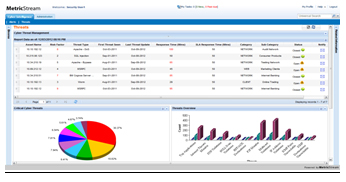
Visualization of threats by asset
Conducting threat impact analyses
The MetricStream solution allows users to conduct a threat impact analysis based on various scenarios such a successful exploitation of a vulnerability or a system failure. The solution supports both qualitative and quantitative methodologies for rating the impact of a threat. It also provides automatic notifications with the complete details of each threat, including the severity of the threat, CVE ID, source of the threat, affected technologies, available controls, and possible remediation instructions.
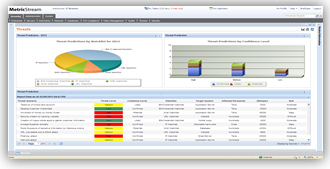
Threat analysis report
Remediation management
The solution automates the entire lifecycle of vulnerability remediation. All validated vulnerabilities are remediated based on the vulnerability severity or Common Vulnerability Scoring System (CVSS) and asset risk rating from the prioritization matrix.
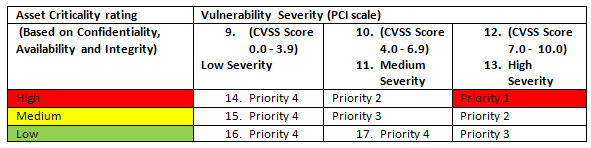
Vulnerability Prioritization Matrix
Reporting
Powerful dashboards deliver real-time threat intelligence from across the organization. In addition, aggregated vulnerability scanning and resolution reports provide insights into valuable data such as the total number of assets scanned per month/quarter, number of assets per risk category (critical, high, medium, low), and resolved and non-resolved vulnerabilities within the defined time frame.
Ensuring compliance with ISO 27005
The MetricStream solution enables the client to conform to ISO/ IEC 27005 through a structured, systematic, and rigorous process for end-to-end IT risk management - right from risk scoping, to risk identification (assets, threats, controls, vulnerabilities, consequences), to risk estimation/ assessment (qualitative and quantitative), to risk evaluation and scoring, to risk treatment, acceptance, risk communication, and risk monitoring, and review. Real-time visibility is provided into every stage of this process through powerful reports and dashboards with drill-down capabilities.
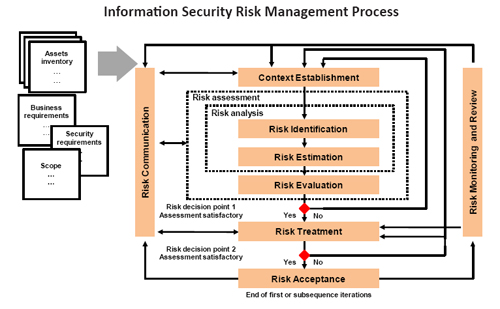
MetricStream enables the adoption of ISO 27005 Methodology
Challenges
Before implementing the MetricStream solution, the client confronted several business challenges such as:
- An expanding IT infrastructure network and a rapidly growing customer and third-party vendor eco-system which increased organizational exposure to cyber-threats
- Resource-intensive manual processes with numerous cumbersome spreadsheets
- Complexity of consolidating vulnerability data from multiple disparate sources into a centralized console without duplicating the data
- Increasing difficulties in consistently complying with IT regulations and standards such as PCI-DSS and ISO 27001
- Limited efficiency in tracking, prioritizing, and reporting the remediation of vulnerabilities
- Difficulty in quickly analyzing the impact of and responding to emerging threats and vulnerabilities
Why MetricStream?
Integrated approach to IT risk and compliance: The MetricStream solution consolidates all IT risk management, compliance management, threat and vulnerability management, and asset management processes in a single, centralized framework for greater efficiency and transparency
Market leadership: MetricStream IT-GRC Solution is widely deployed by leading organizations worldwide to better manage their IT risks, strengthen their security controls, and protect the organization’s overall IT infrastructure from constant threats and vulnerabilities
Scalability: The MetricStream solution effortlessly scales across the global enterprise, and provides the flexibility to adapt to further organizational growth changes.
Platform extensibility: The underlying platform of the MetricStream solution provides the capability to seamlessly add on additional applications such as audit management applications or policy management applications to further enhance the client’s IT-GRC program.
Benefits
- Establish a consistent and repeatable process for threat and vulnerability management
- Efficiently harness massive amounts of security, threat, and vulnerability data from multiple existing systems, and store it in a centralized framework for complete top-level visibility
- Correlate and map security data to the full range of assets, risks, and compliance metrics, and transform this data into actionable risk intelligence
- Enhance IT risk assessments and computations for optimal risk/reward outcomes as well as calculated risk taking/ risk acceptance.
- Automate various threat and vulnerability management processes, eliminating the need for bulky spreadsheets
- Gain real-time visibility into the end-to-end risk management process, and quickly identify areas of concern that need to be proactively addressed
- Strengthen compliance with multiple IT regulations, laws, and standards
- Facilitate a culture of collaboration and proactive IT risk management

Subscribe for Latest Updates
Subscribe Now