Measure Your Program Outcomes
Source: Based on MetricStream customer responses and GRC Journey Business Value Calculator
-
 55 %
55 %reduction in the time taken to create and update policies
-
 90 %
90 %decrease in the time taken to review and approve policies
-
 50 %
50 %time saved in tracking and linking policies to regulations
Easily Create, Communicate, and Manage IT and Cyber Policies
MetricStream IT and Cyber Policy Management software, part of the Cyber GRC solution suite, simplifies the creation, communication, management, reporting, and maintenance of IT policies. It stores and organizes IT policy and procedure documents in a centralized repository, streamlining the process of developing new policies, modifying existing ones, and reviewing and approving policies across the enterprise. IT Policy Management also enables mapping of IT policies to compliance requirements, implementation of the policies across the enterprise, tracking of policy reviews and acceptance, and management of policy exceptions using automation, continuous testing, and cloud technology. Powerful analytics and reporting functionality help track each IT policy throughout the lifecycle, providing managers complete visibility into the system, and helping them strengthen IT governance and policy compliance.
Read More product details Download RFP product details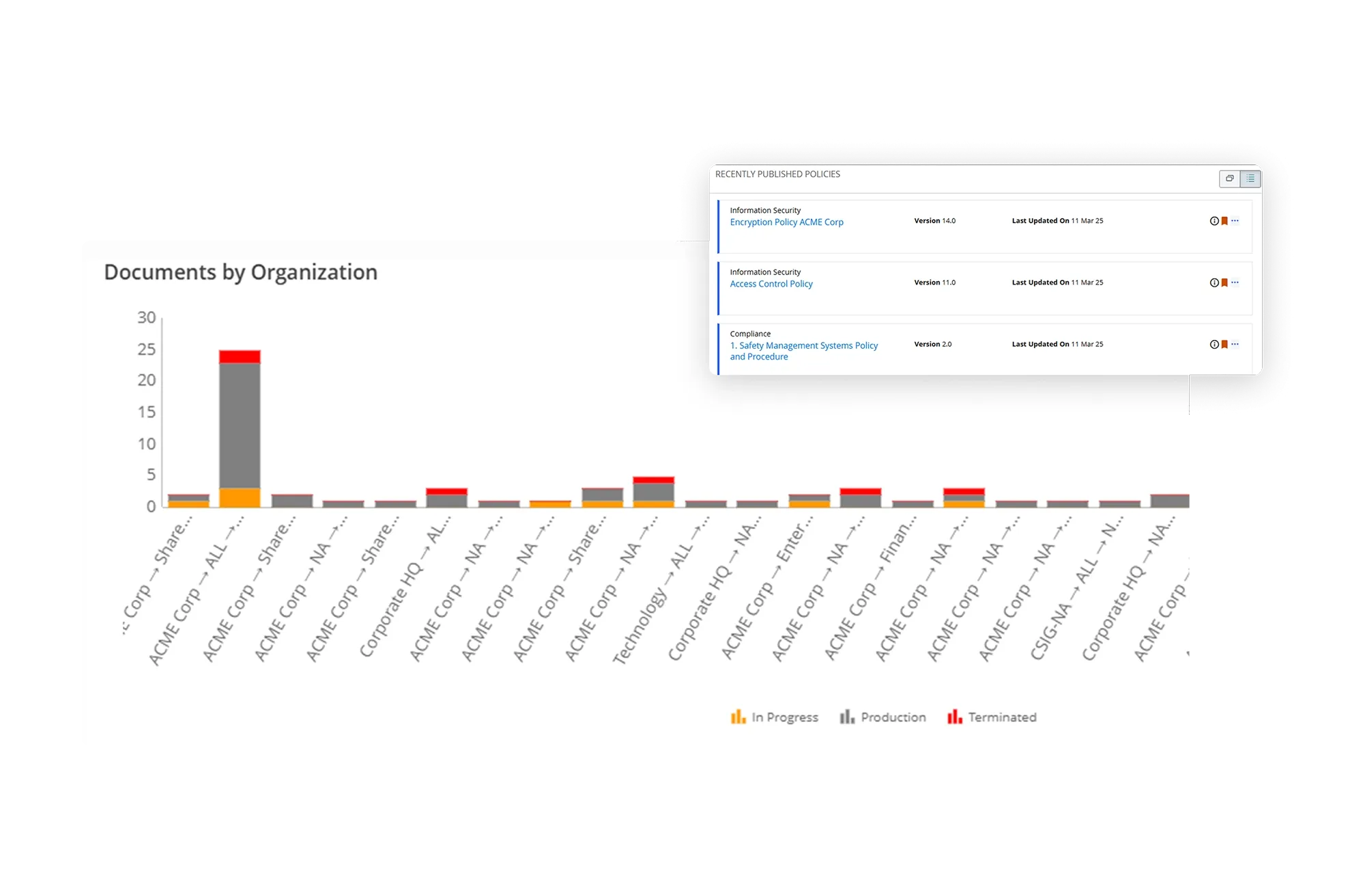
How Our IT and Cyber Policy Management Software Helps You


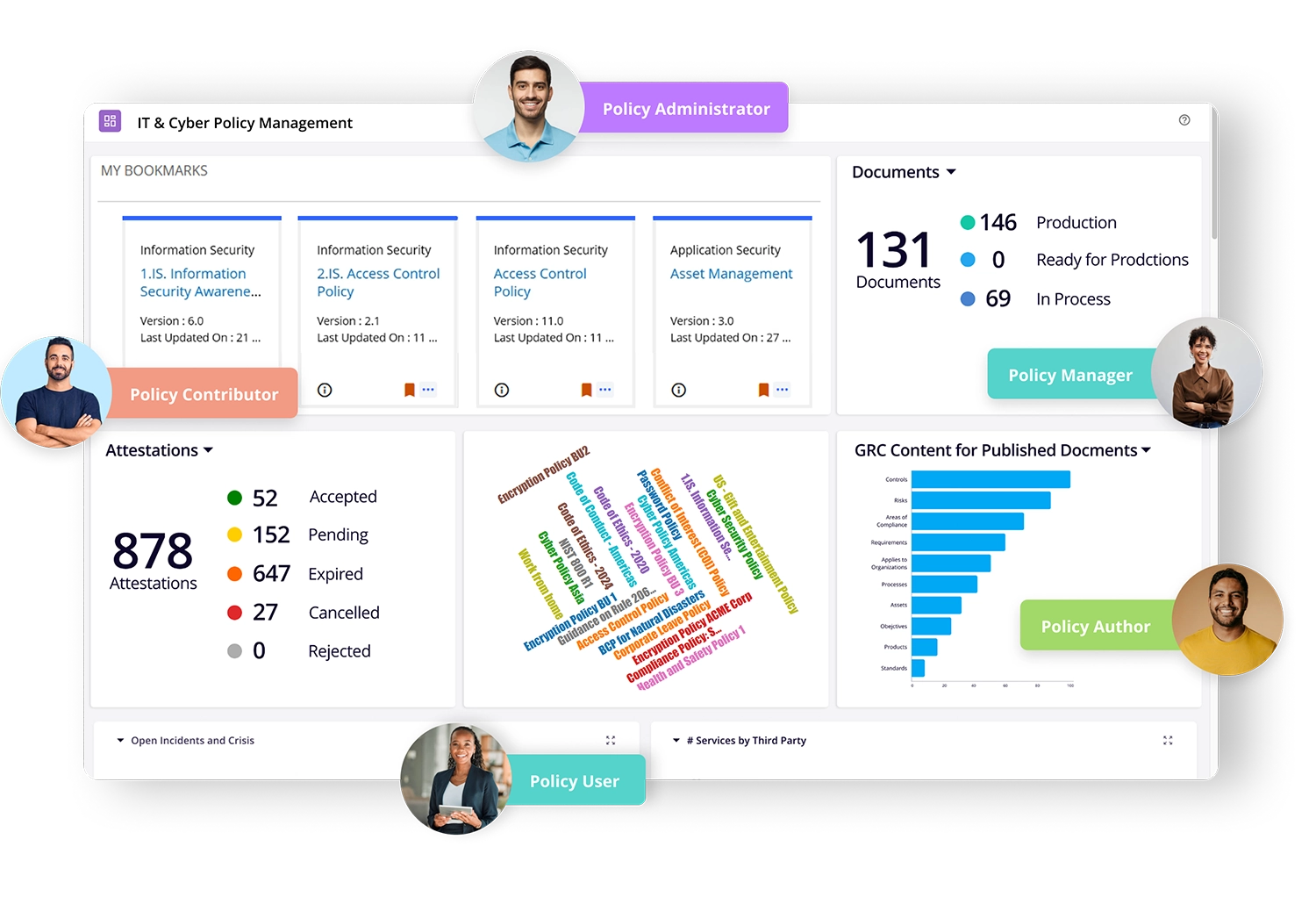
Quick Access to IT and Cyber Policies
Leverage our easy-to-use centralized policy portal to access the latest organizational IT and cyber policies, simply and easily. View a brief snapshot of each IT and cyber policy before going through the details. Bookmark policies for quick reference and browse through those that are accessed frequently or have been recently published.
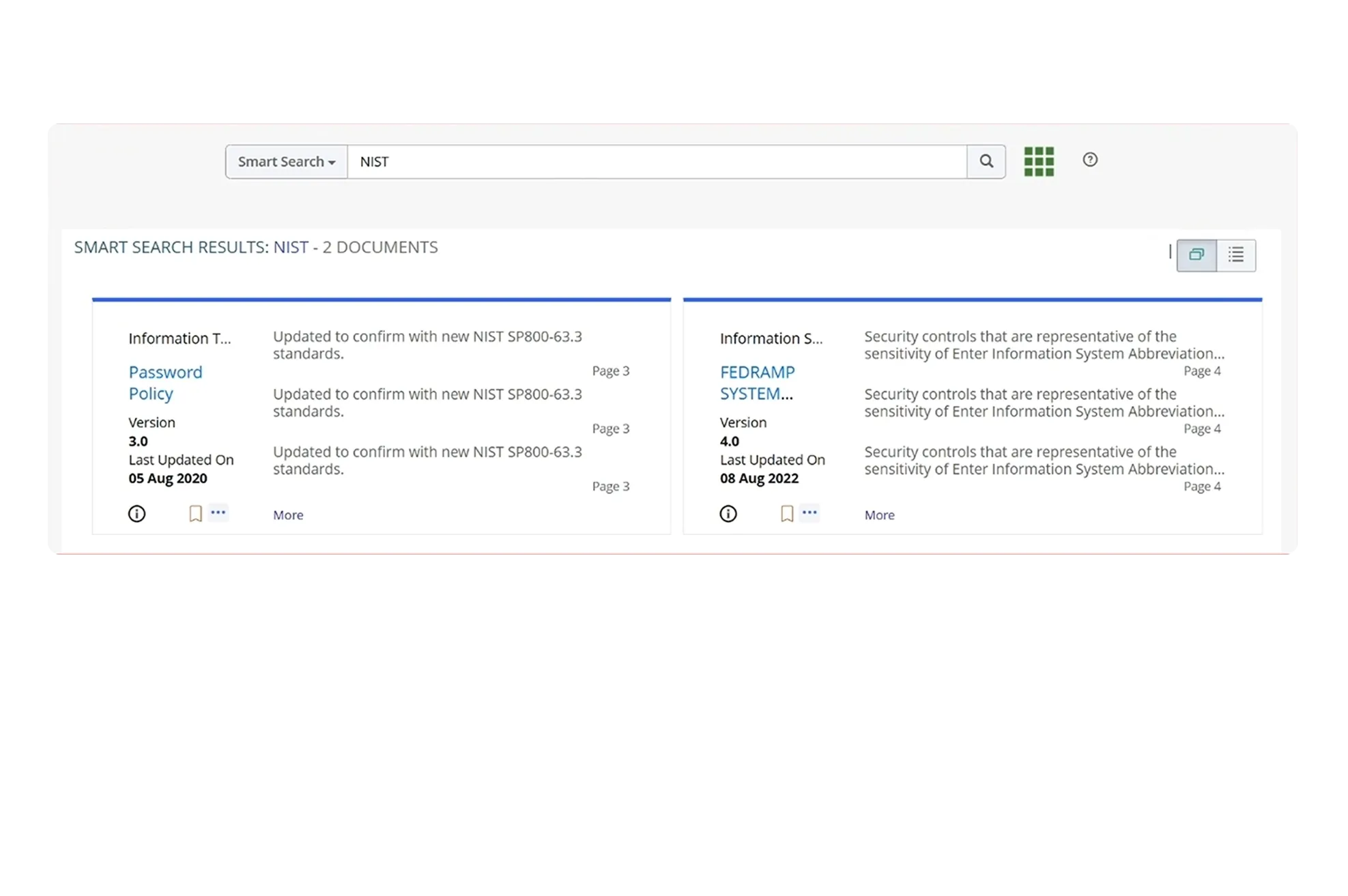
Intent-Based Policy Search
Quickly search for relevant IT and cyber policies anywhere, anytime, with policy search widgets that can be connected to your intranet, conversational chatbot, or any other tool of your choice. Enable your frontline employees to easily find relevant IT and cyber policy information based on search intent by leveraging natural language processing (NLP) based smart search. The search also considers related risk and compliance aspects

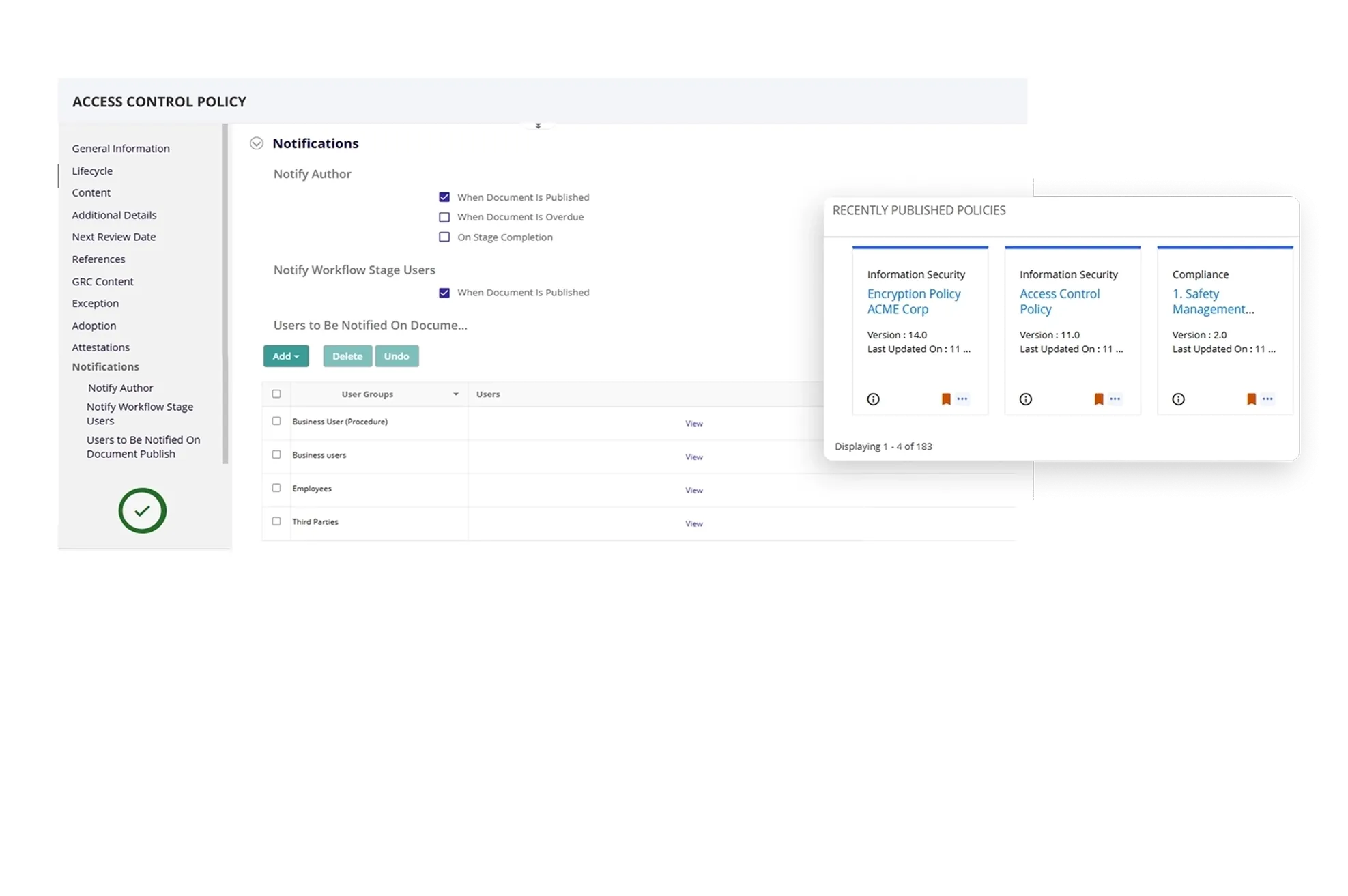

Collaborative IT and Cyber Policy Creation Process
Simplify IT and cyber policy creation and collaboration using the product’s built-in automated workflows. Easily upload IT and cyber policies directly from your system as well as modify existing policies. With Microsoft Office 365 integration, collaborate with relevant stakeholders to simultaneously view and edit IT and cyber policies, saving time and driving faster results.
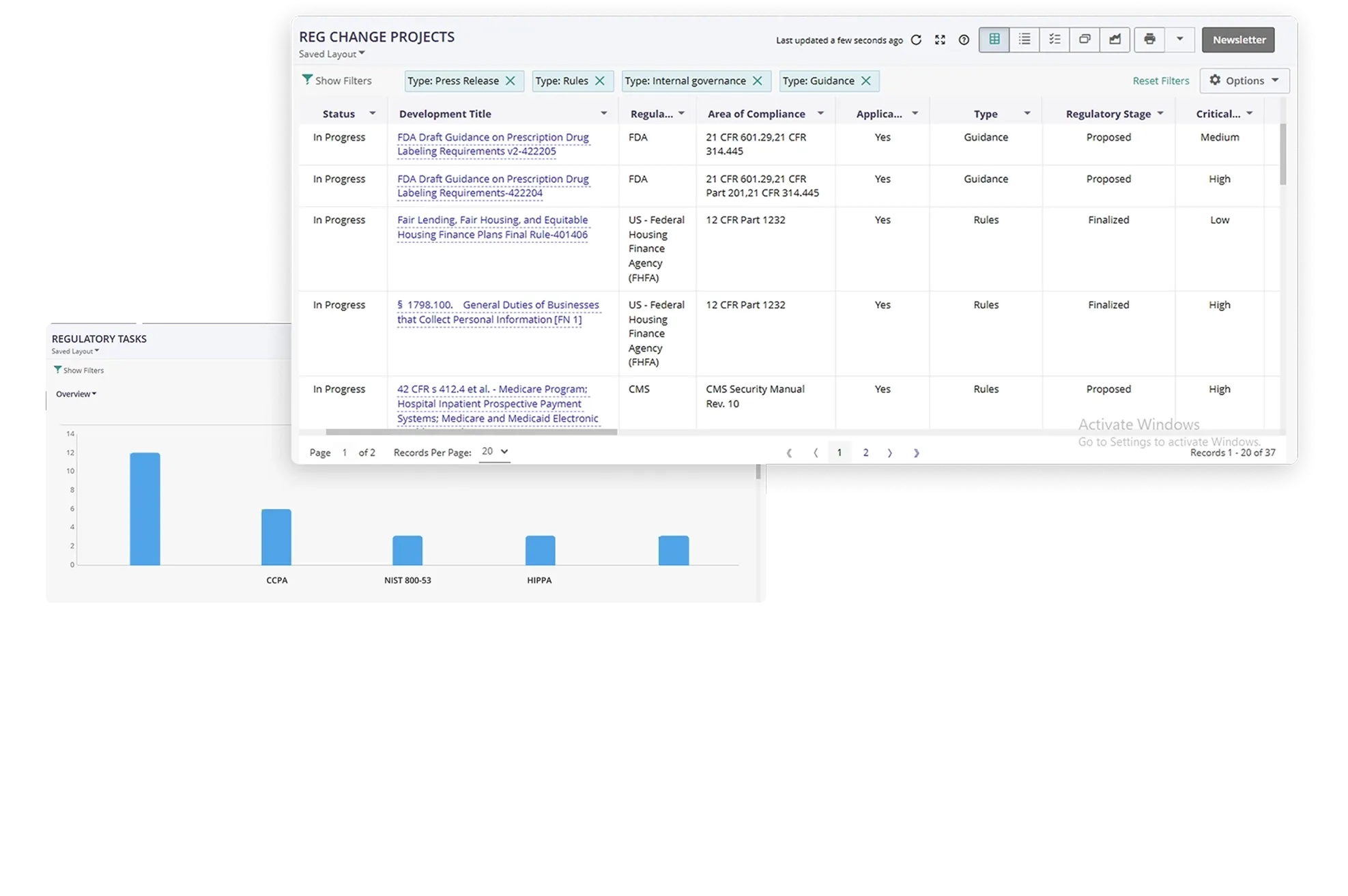
Simplified Policy Mapping to Regulations
Strengthen compliance by mapping IT and cyber policies or sections to regulations, risks, controls, legal requirements, processes, and organizations. Send out automated email notifications and alerts to relevant stakeholders indicating changes in IT policies.

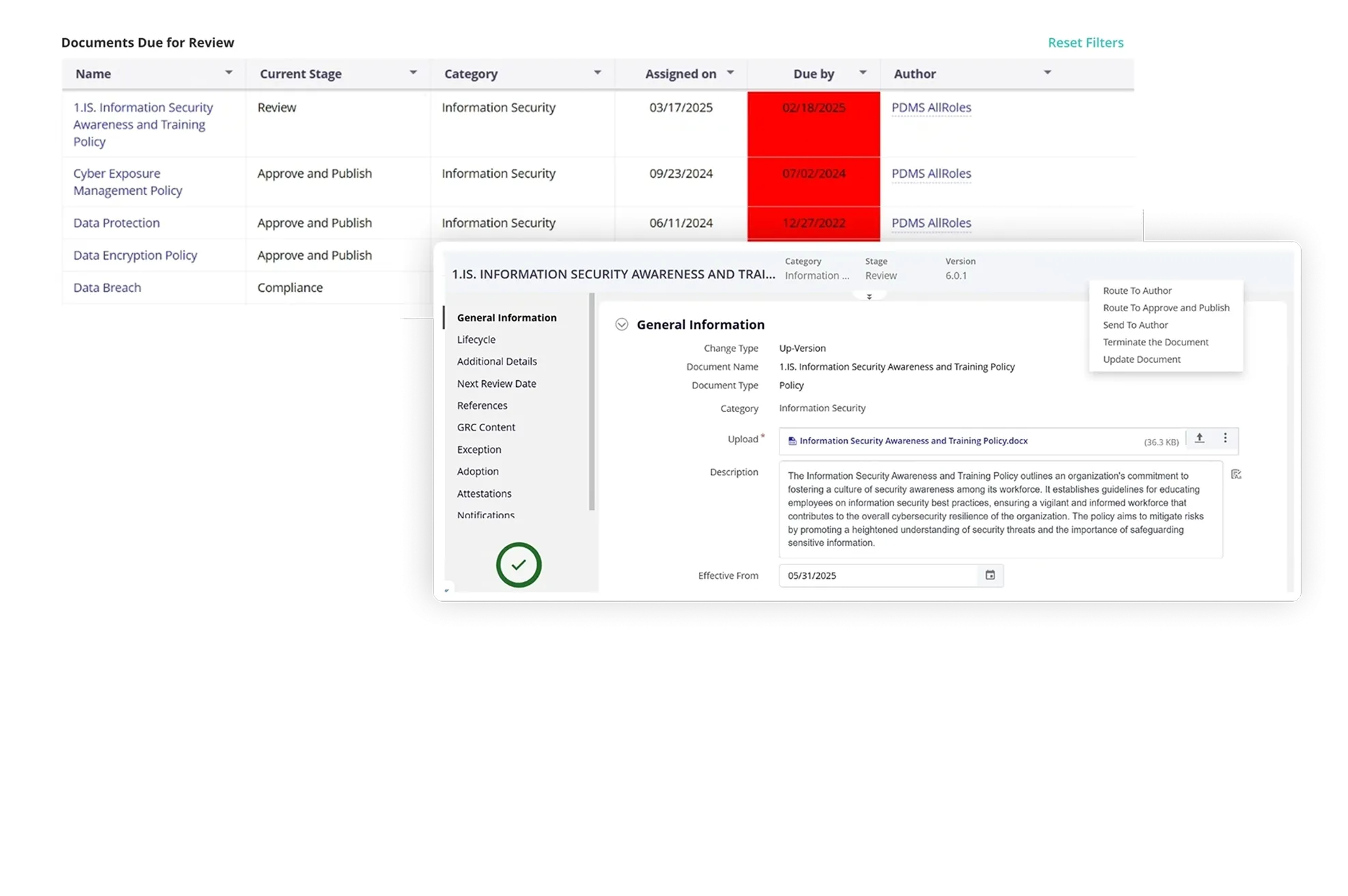

Collaborative Review and Approval Processes
Simplify policy review and approval process by routing either the entire IT and cyber document or sections to relevant users. Enable different sections to be reviewed by different users if needed. Allow multiple reviewers and approvers to collaborate on the review and approval process and add their comments or feedback.
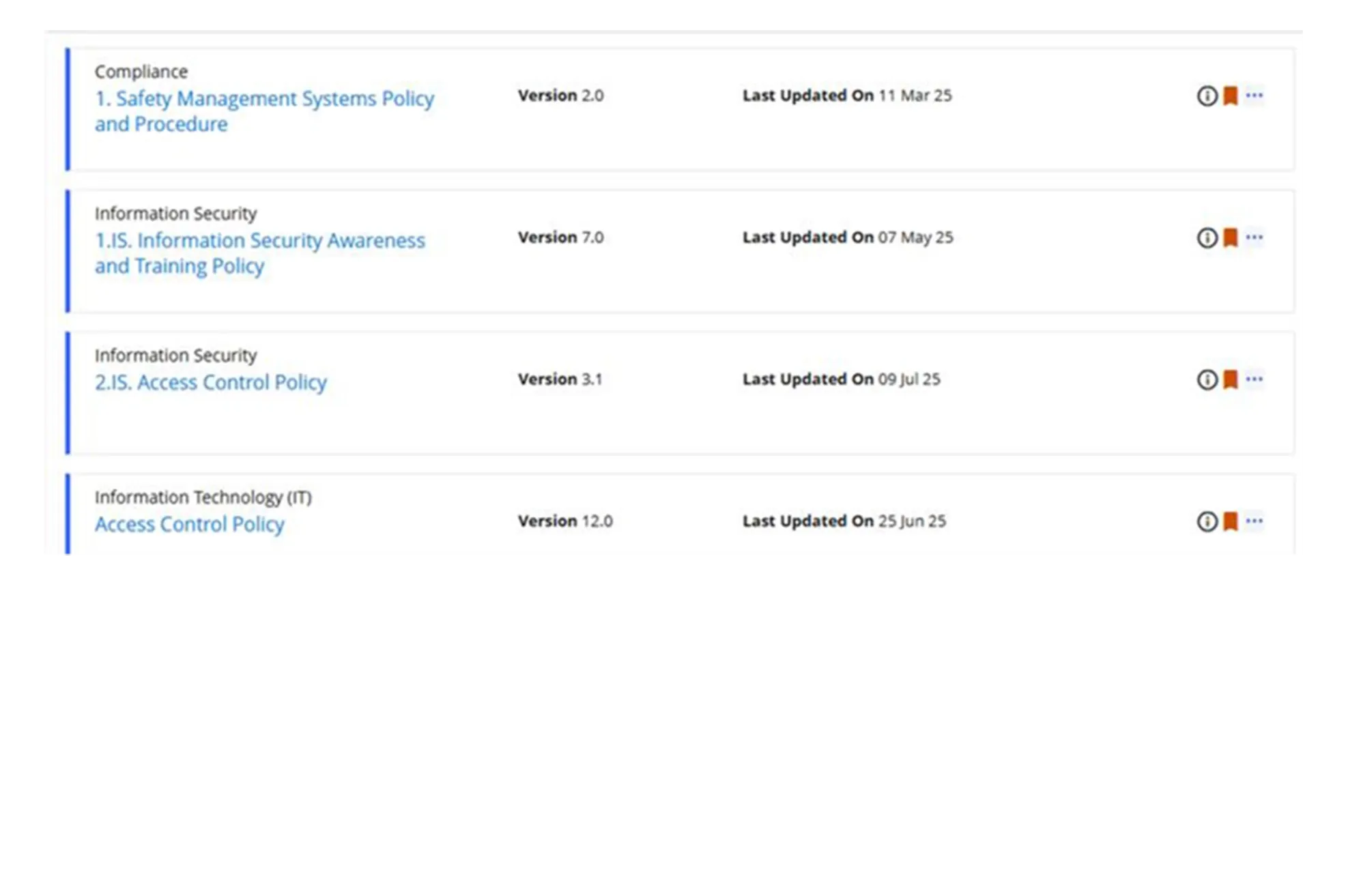
Enhanced IT and Cyber Policy Communication
Send out automatic email notifications to the target audience to communicate IT and cyber policy once it is published. Categorize users based on their roles and allow them to access and read the policy depending on their assigned category.


Streamlined Policy Attestation Processes
Enable attestations for IT and cyber policies for a chosen user or user group. View attestation tasks on the policy portal and allow attestations only after each user scrolls through the entire policy document.
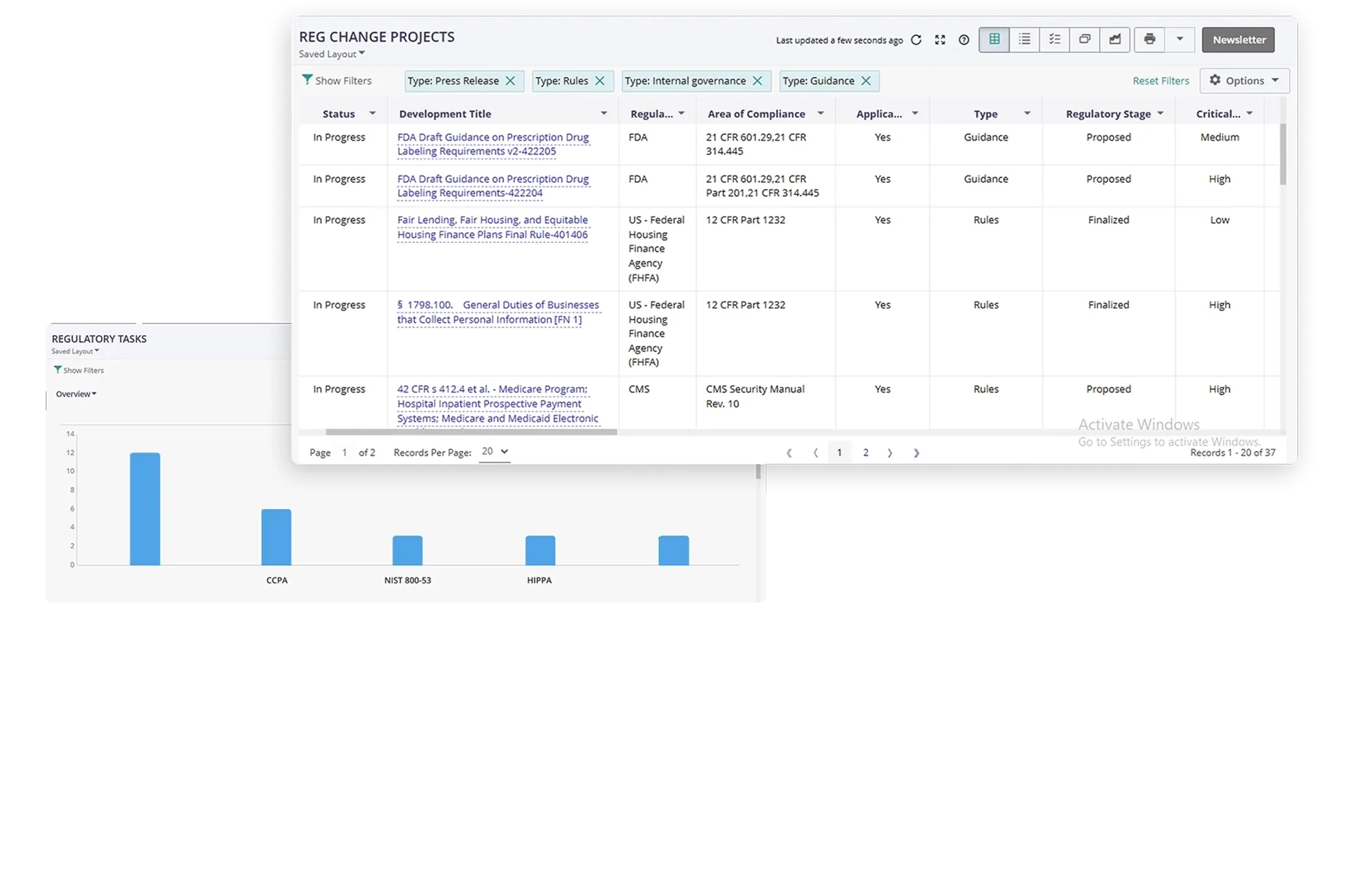
Well-Defined Policy Exceptions Request Process
Request exceptions for IT and cyber policies directly from the policy portal. Provide the reason for the exception and specify the duration for which it is required. Easily manage exceptions by configuring workflows and track the status of all exceptions.
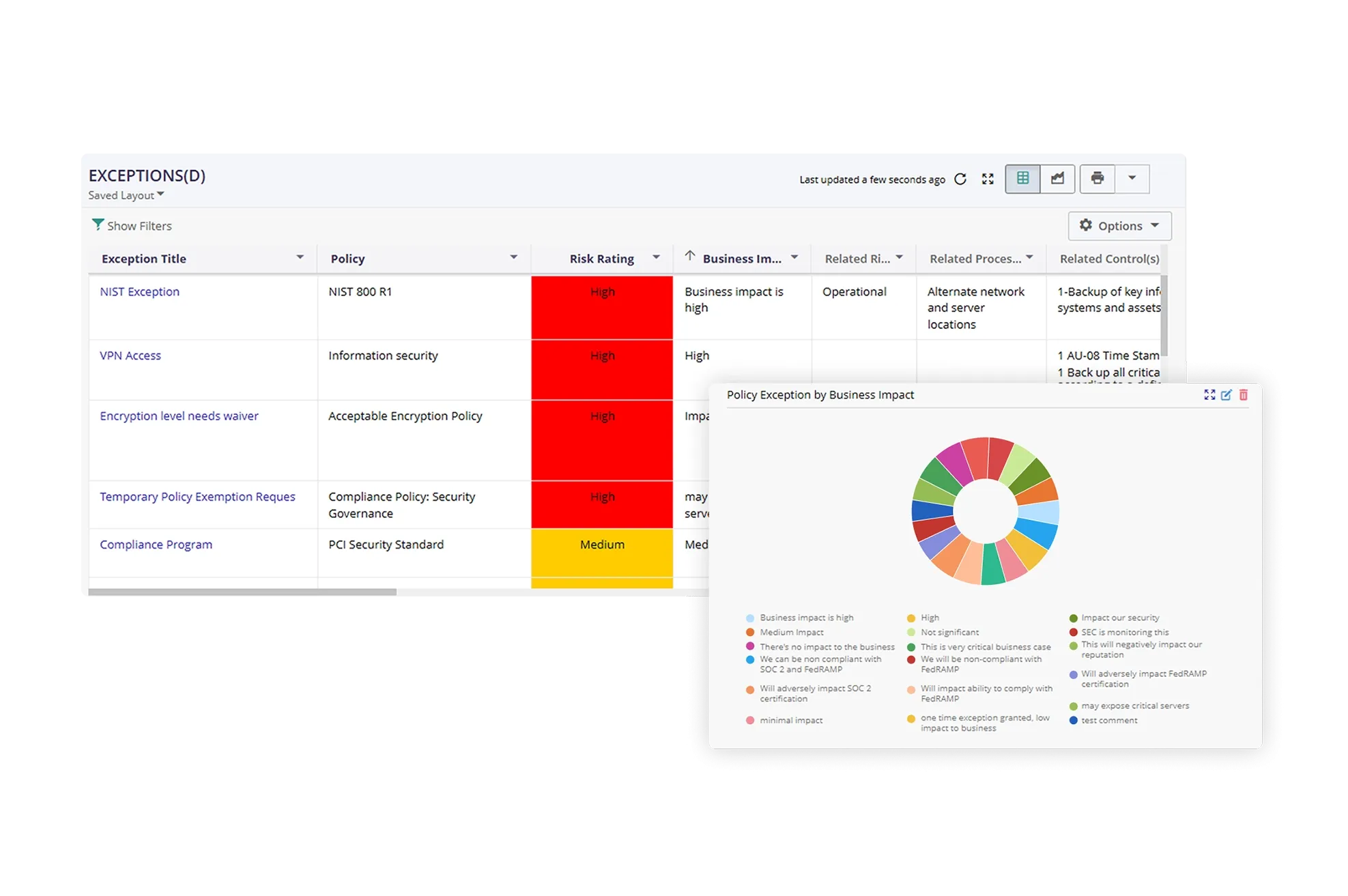

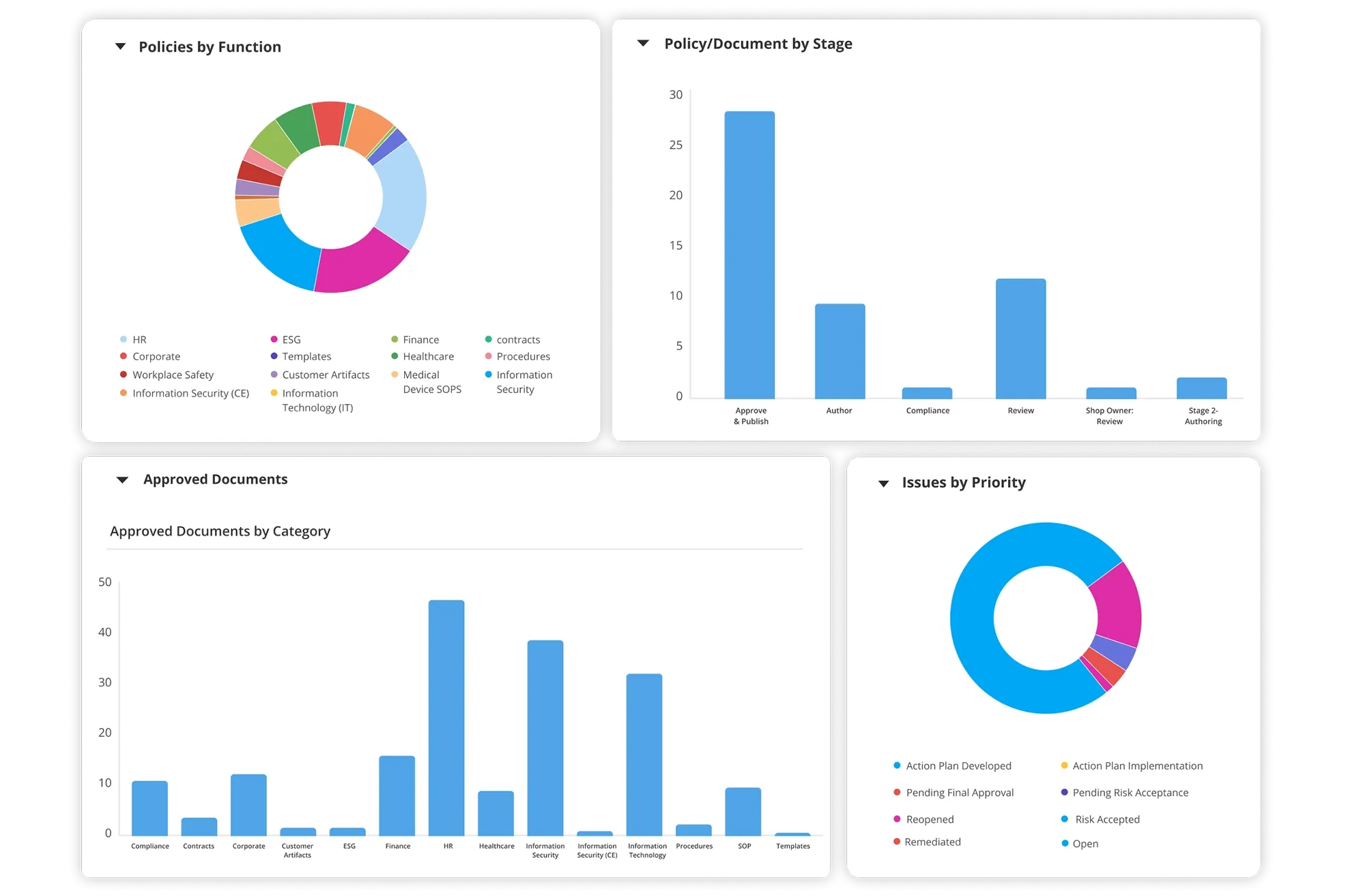

Improved Visibility with Reports and Dynamic Dashboards
Gain real-time visibility into the IT policy management program through powerful reports and graphical dashboards. Leverage drill-down capabilities to view statistics and data on IT policies based on different parameters such as policy type, status, audit history, in-process documents, links to compliance, and related risks and controls.
How Our IT and Cyber Policy Management Software Benefits Your Business
- Reduce time in creating IT and cyber policies and aligning them with regulations. Ensure compliance through timely communication, attestations, and evidence collection, while efficiently managing exceptions and proactively identifying potential policy violations across the organization.

Frequently Asked Questions
With MetricStream IT and Cyber Policy Management, create IT and cyber policies either inline or using attachments. Inline policy creation allows you to break up a policy development into various sections, enabling multiple users to simultaneously access the same inline document. You can then collate and publish the IT policy. Furthermore, policy authors can upload a draft IT and cyber policy that will go through the policy management lifecycle process. With attachment-based policy creation, you can submit IT and cyber policies as attached documents.
Yes. MetricStream IT and Cyber Policy Management allows you to link IT and cyber policies or sections to regulations, risks, controls, departments, business units, etc. You can also link various reference documents to the policies as well as its sections. The product allows linking in one-to-one, one-to-many, many-to-one, many-to-many mapping between policies and other GRC areas like compliance, risk, and the control framework.
The product sends out automatic email notifications to the relevant users for the attestation of IT policies. The email includes a link that takes the user directly to the section that needs to be attested/acknowledged. Users can confirm attestation by using electronic signatures or check-boxes.
Yes. MetricStream IT and Cyber Policy Management provides workflows for policy exceptions. You can raise an exception for an IT and cyber policy by specifying the reason for the exception and the duration for which it is needed.
You can explore MetricStream Cyber GRC products which help organizations to implement a comprehensive IT and Cyber Risk and Compliance Management Framework based on established security standards. To request a demo, click here. cyber grc
Visit our Learn section to dive deeper into the GRC universe and the Insights section to explore our customer stories, webinars, thought leadership, and more.