
AI-First Connected GRC
Drive a Connected GRC Program for Improved Agility, Performance, and Resilience
Discover Connected GRC Solutions for Enterprise and Operational Resilience
Explore What Makes MetricStream the Right Choice for Our Customers
Discover How Our Collaborative Partnerships Drive Innovation and Success
- Want to become a Partner?
Your Insight Hub for Simpler, Smarter, Connected GRC
Enforcing Policies Key to Managing Compliance Programs in Energy and Utilities
Overview
Energy and utilities organizations are facing a rapidly changing business environment. With growing cyber threats on one side and complex regulatory requirements on the other, organizations find themselves struggling to strike a balance between managing and monitoring numerous auditable tasks and compliance activities related to FERC, NERC, ERO, NRC and other regulatory requirements. In such a scenario, developing and enforcing relevant policies and procedure, implementing a robust compliance program and adopting the right risk assessment methods will help manage the growing number of compliance programs.

Policy Development and Enforcement
Organizations can be gauged on their governance risk culture by the policies and procedures that they implement. Policies and procedures establish accountability and responsibilities and ensure compliance. For policies to be properly implemented, enforced and managed, one of the most important elements required is to have a well-designed policy management lifecycle process. The policy development cycle helps you to manage and maintain policies and utilize them appropriately. Some of most important processes of policy management lifecycle process are discussed below.
Policy Development
Before you begin on developing policies, you first need to identify the policies that you want implemented. In this process, you will avoid hoarding meaningless and unnecessary policies within the organization. Relevant policies can be identified by taking into account the corporate environment, the risks the organization is exposed to, and the regulatory landscape. Here are some guidelines to ensure that the policies are developed properly:
- Understand who is/are responsible for the policy
- Map and track the various stages, networks and channels in the policy development procedure
- Plan a policy communication and education system
- Ensure that all policies are recognized and every action in the policy development process is documented
- Design audit trails to measure quality and efficiency of the policies
Policy Implementation
Effective implementation of policy starts with the manner in which the policies and procedures are written and is the next step after policy development. The important action points during the policy implementation process are:
- Recognizing the areas of implementing a policy will invite change management challenges
- Creating a formal communication channel where policy issues can be voiced and resolved
- Defining the responsibilities of the personnel in their commitment to policies
Policy Enforcement
During the policy enforcement process, there needs to be a high level visibility of all enforcement procedures so that oversight gaps can be identified and resolved. You also need to:
- Maintain proportionality between non-compliance and their penalties depending on their criticality
- Have an internal process where non-compliance issues are evaluated and appropriate measures are drawn up for amending policies if required
- Create a feedback loop which tracks the views and suggestions for policy enhancement
- Embed audit programs into the policies:
- Include regular audits, unannounced control-oriented audits
- Ensure proper document management for a successful audit
- Audit programs should not only cover what regulatory agencies like FERC and NERC expect, but should be designed using best practices so that you are a step ahead in eradicating risks
- Review and co-ordinate existing internal audit functions so that it adheres to processes that have been defined
Every organization looks at establishing a compliance program and one of the fundamental elements that go into structuring a compliance program is defining and implementing the policies the organization. Once this is done, you need to follow a disciplined approach to build a compliance program that is aligned with the policies, procedures, and regulations set by the regulatory bodies, and at the same time ensures that the growing regulatory demands are met.
Creating a Modern, Proactive, Risk-based Enterprise Compliance Program
The energy and utilities industry has seen a surge of transformation due to technology, regulations and competition. And more than ever, it is crucial for energy and utilities organizations to implement and manage a robust compliance program that is aligned to the specific challenges faced by your business enterprise and efficiently adapts to the changing regulatory environment.
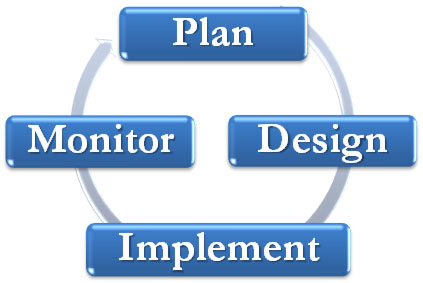
Most compliance programs go through four stages, the most crucial being the first two:
- Planning
- Designing
- Implementing
- Monitoring
Planning:
In the initial stage of the compliance program, you need to gather vital information by:
- Identifying compliance resources: Create an inventory of the personnel who will be part of the compliance program, budgetary allocations, training courses and delivery mechanisms, past and current documents related to compliance, and compliance reporting processes .
- Referring to historical records: Take into account the records of the last five years â€" the violations that occurred, how they were mitigated, previous compliance assessments, audits and internal reports, as well as the compliance budget history.
- Interviewing company personnel: Gather information from departmental managers who are directly or indirectly connected to the compliance program. Talk to internal auditors and legal teams to define their capacities and capabilities. Meet with human resources to identify employees with compliance-related goals, and external counsel to determine the level of involvement of the organization.
- Analyzing IT systems: Understand the tools and systems that will be utilized in the compliance program
Designing:
The vital information gathered in the first stage is utilized in designing the compliance program. The design stage has three integral phases â€" initial, secondary, and final.
The fundamentals in the initial design phase are to:
- Create an inventory of all the rules, laws, and regulations that need to be complied with.
- Structure an internal compliance communication system to ensure compliance issues are identified and assessed across the different levels in the organization.
- Make an effective violation and risk mitigation plan based on violations and risks that the organization can be or has been exposed to.
During the secondary design phase you need to:
- Plan mitigation processes and identify the available resources through which compliance issues are mitigated.
- Form a compliance committee to ensure that the program runs smoothly.
The final design phase involves:
- Creating a compliance manual wherein policies, procedures, and controls are identified, and outlined.
- Drawing up an investigation contingency program where certain tasks can be assigned to people to handle things at the front end when regulators come knocking at the door.
- Maintain a continuous compliance log which records the guidelines â€" principles, implementation, monitoring, and improvement of the compliance program especially with respect to FERC and NERC compliance.
Implementation
Once the first two stages have been successfully completed, it is time the compliance program is rolled out across the organization. During the implementation stage you need to ensure:
- Availability of sufficient personnel support across the organization â€" from the compliance committee, to the law and human resource department and the internal and external audit department.
- Appropriate system and technology is in place to track compliance metrics and provide training.
- Regular activities where employees can give their feedback on their response to the compliance requirements and how they can improve compliance program
Monitoring
After the compliance program has been implemented, it needs to be monitored on a regular basis through:
- Audit and assessment plans: Conduct enforcement actions and audits, review periodical records, and utilize external monitoring sources to validate internal controls.
- Systems: With recent advances in technology, you can automate time-intensive processes such as report generation and leverage dashboards which enable real-time tracking and monitoring of compliance programs across the enterprise.
- Reporting: Besides the automated reports enabled through technology, the compliance committee needs to have knowledge about the indicators and metrics of the compliance program and communicate them internally within the organization regularly.
Conducting Regulatory Risk Assessments
Every year, energy and utilities organization have numerous and newer challenges to tackle. Be they, the introduction of stringent reliability standards introduced by regulatory bodies such as NERC, FERC, OSHA, EPA, or the increased exposure to cyber thefts and attacks due to the Smart Grid technology. Organizations need to have a well-defined approach to mitigating these risks and stay clear from penalties and hefty fines.
Regular risk assessments enable you to focus on critical areas of concern, and prioritize the use of resources to maximize response and recovery efforts. The Risk Assessment Matrix (RAM) is a logical extension of the risk assessment process that helps organizations identify critical processes, threats that would impact those processes, and the vulnerability of those processes to the threats. The six-step process will help you implement RAM and achieve a risk-based compliance:
- Identify the rules, regulations, and laws specific to your organization: Make a note of all the regulatory directives that are applicable to your organization's business model.
- Identify the most important processes and functions: Create a comprehensive list of the separate functions and processes that go into providing necessary services. Some of the processes and functions are:
- Compliance
- Communications
- Operations
- Legal
- Marketing
- Facility Management
- Service
- Finance
- Human Resources
- Training
- Information Technology
- Rank functions and processes according to criticality: Determine the criticality according to the importance and impact that a function or process has on the compliance program.
- Identify threats to compliance processes: Categorize and identify the threats that have occurred due to natural disasters, facilities-related emergencies, asset protection incidents, and information systems difficulties.
- Determine the vulnerability of critical processes and functions: Assess the level of vulnerability of a process to threats by considering the probability of a threat, the frequency with which it occurs, and its severity.
- Prioritize the deployment of resources to address threats and vulnerabilities: Ensure that there are appropriate controls and adequate resources to help resolve threats.
NERC Standards Compliance and Reliability Standard Audit Worksheets (RSAWs)
Another area of compliance that needs to be regularly monitored and continually assessed for risks is NERC. Through the years, there has been a rise in standards as well as risks associated with NERC. From 83 standards in 2007, today there are more than 300 compliance standards. Non-compliance with any NERC standard could invite penalties based on the severity and impact of the non-compliance activity on the reliability of services. Most organizations have elements to manage NERC compliance, including:
|
|
The Reliability Standard Audit Worksheets (RSAWs):
The NERC developed RSAWs as an assessment and documentation tool in the Compliance Monitoring Program for each regional entity. The RSAWs can be used as part of internal audits to help determine that there is sufficient evidence to verify compliance with the requirements of each standard before regulators come in for an inspection. The worksheets provide a logical order for organizing documents, and a formal communication method with the compliance enforcement authority.
The Role of Technology in Managing Compliance and Policies
The best defense against the pressures of regulations and risks is to manage and monitor your compliance program efficiently and establish processes to prevent non-compliance from happening. Technology enables organizations to adapt a compliance program that is efficient, agile and cost-effective and also provides:
- A collaborative compliance environment
- An integrated compliance platform
- A disciplined methodology
- A centralized repository of compliance data and documents
Collaborative Environment: A typical compliance environment has a multitude of regulations that need to be followed and a number of people managing and monitoring a host of compliance processes. Employing the appropriate technological tools can enhance collaboration across your organization, enable seamless sharing of information, break down redundancies and duplicated efforts, and improve cross-enterprise co-ordination. This kind of a collaborative environment also affords an enterprise-level view to closely track compliance processes and enable real-time risk detection and mitigation.
Integrated Compliance Processes: Energy and utilities organizations have standards like FERC, NERC, ERO, EPA, PCI, and SOX to comply with. Each of these standards consists of many further sub-requirements. Technology enables you to implement an integrated compliance framework that maps all these compliance requirements, standards, and policies with the corresponding risks, controls, control tests, documents, and compliance processes to simplify and strengthen end-to-end compliance management.
Disciplined Methodology: Technology automates many cumbersome compliance processes, thereby saving valuable costs, and accelerating and strengthening compliance management â€" right from implementing policies, to mapping these policies to compliance processes, to tracking policy exceptions, and managing policy risks. With the help of technology you can assign and escalate tasks to the relevant users implement specific follow-up activities to track, escalate and confirm task completion.
Centralized Repository: There are numerous compliance standards, policies and procedures that need to be implemented. With the help of a centralized library, you can efficiently and easily store, maintain, and access these policies and standards and also provide easy search capability. With this information access, you can fulfill requests by external auditors to provide documentation and evidence that validate that you have met a specific compliance requirement, and controls are in place to ensure ongoing compliance.
Conclusion
A robust compliance and policy management program not only earns you the respect of regulators, but also improves your credibility in the market, and ups your competitive advantage. The key is to develop relevant policies and procedures, and manage them through a proactive, risk-based, and integrated compliance program. Leveraging technology can improve the effectiveness of the program by automating various compliance activities, tracking compliance metrics, and helping you stay on track with regulatory deadlines and changing regulatory reforms.

Subscribe for Latest Updates
Subscribe Now





