
AI-First Connected GRC
Drive a Connected GRC Program for Improved Agility, Performance, and Resilience
Discover Connected GRC Solutions for Enterprise and Operational Resilience
Explore What Makes MetricStream the Right Choice for Our Customers
Discover How Our Collaborative Partnerships Drive Innovation and Success
- Want to become a Partner?
Your Insight Hub for Simpler, Smarter, Connected GRC
Emerging Cybersecurity Risks and Safety Tips for Organizations in COVID-19 Era
Overview
As we all know the COVID-19 pandemic has affected every business in some way or the other and has created many new risks as well. Organizations are forced to shut down their operations and employees are working from home. While Industries are busy handling the COVID-19 crisis, this has emboldened cyber criminals to increase attacks on vulnerable organizations.
Employees are the first line of defense working on their laptop devices remotely and this has exposed them to hackers using social engineering techniques to steal corporate credentials. As per a recent NASA report, phishing email scams have doubled.
This article examines the different types of attack vectors cyber criminals are using these days in the COVID-19 era. We will also learn about how we can protect our organizations from these risks.

-
Top Cybersecurity Risks during COVID-19
When we think of cyber security, we think of its components – people, processes, and technology. And looking at the current scenario, all three components are vulnerable and compromised by cyber criminals in some ways.
If we analyze the recent attack vector, almost all the attackers are using coronavirus themes, including business email compromise (BEC), credential phishing, malware, and spam email campaigns. The most popular and effective attack is credential phishing.
Here’s a list of emerging cybersecurity risks and attack vectors based on recent cybersecurity attacks and related activities during COVID-19.
1. Phishing Attacks
Phishing has always been the basic and the most used attack vector. But in the current pandemic scenario, performing mass attacks on employees has become more popular as they are perceived as low hanging fruits for hackers.
Some of the reasons that have made phishing the most the used attack vector in this time are:
- With people working from home there’s enough time to open an email, attachment– whether out of curiosity to learn and read about the coronavirus or out of boredom
- Gaps in the security training and cybersecurity awareness of a remote workforce make them an easy target for hackers
- HR and admin, government, health agencies etc. are sending a lot of emails related to COVID-19, which gives an opportunity for hackers to use COVID related phishing mails as an easy and obvious attack vector.
These fraudulent emails contain logos and other images related with the Center for Disease Control (CDC) and the World Health Organization (WHO). To lure their targets, emails include links to items of interest, such as "updated cases of the coronavirus near you." These links redirect users to landing pages which look legitimate, but the sites are often malicious and may be designed to steal email credentials.
Example - credential phishing - ‘‘COVID-19 Infected Our Staff
- A relatively small campaign in the US
- Credential phishing attack uses a company-wide email to target retail companies and uses concerns about infected staff members to try and lure victims to click
- This leads to Microsoft Office credential phishing
Some other Examples of Phishing Attacks are as below:
Industry Specific Targeting: (Targeting Affected Industries)
- Emails with subject lines like “Coronavirus – Brief note for the shipping industry,” have been sent to employees of companies in industries being disrupted by the virus.
- BEC (business email compromise) campaigns are targeting manufacturing, finance, pharmaceuticals, healthcare, and transportation companies.
Hidden Malware:
Malicious emails directing recipients to educational and health-related websites with malware, thus infecting their systems.
Example –hidden malware – Your Neighbors Tested Positive
- Smaller campaign in the US
- Targets energy, construction, and telcos with an email using the subject line ‘coronavirus disease update (COVID-19) your neighbors tested positive’.
False advice and cures
- Hackers disguising as regional medical providers
- These type of emails were sent to people in Japan in January and February, and were among the first coronavirus-related phishing attacks.
False charity:
In this difficult time, many people have come forward to help the needy and poor. Hackers are using this as an opportunity to send phishing emails asking for donations disguised as a recognized body/ NGO.
2. Spoofing:
Spoofing has been another popular attack vector for many cyber-attacks in recent times. There were cases of hackers spoofing emails from trusted sources, such as government bodies and health agencies, pretending to offer coronavirus tips and advice, and making victims fall into their trap by clicking on the embedded tip sheet, getting their systems infected with malware, or in some instances, it’s encrypted ransomware.
Tips: Grammatical mistakes are the most glaring clues hinting at malicious intent and can be commonly seen in many email cyber-attacks impersonating a reputable source or organization.
3. Exploiting Human Emotions (Social Engineering Attacks):
In these hard times, people are worried about their health and are looking for information from different sources to stay safe. Hackers are using techniques such as social engineering and spear-phishing scams, which are both well-known attack vectors for achieving business email account compromise. These attacks are attempts made through email (phishing), voice calls (vishing) or SMS (smishing) by cyber criminals fooling people and collecting sensitive information.
Other types of social engineering attacks are as below:
- Social Media Deception – Creating fake profiles in different social media platforms (especially LinkedIn) and tricking people to part with sensitive information
- Pretexting – Cyber criminals pretending to need certain information from their targets in order to confirm their identity.
- WaterHoling – In this technique, cyber criminals will:
- Find out the interests of target groups (websites, applications they visit)
- Look for vulnerabilities in these sites and applications in order to infect them with malware.
- If the target group access these websites or applications, they too will get infected
4. Fake Application:
Many cases of malicious fake COVID-19-related Android applications have been reported. Installing these apps give attackers access to smartphone data or a window to encrypt devices for ransom.
100,000 new COVID-19 web domains have been registered, which should be treated with suspicion, even though not all of them are malicious.
5. Security Vulnerability in Technology Used:
To work remotely, employees are using different kinds of tools. With all these tools they are increasing their exposure of the digital attack surface. CISA (Cybersecurity and Infrastructure Security Agency) has just issued an alert regarding vulnerabilities caused by remote access to organizations’ computer systems. A proliferation of cloud-based apps makes it easier for bad actors to exploit holes in networks.
Example - Zoom Security Vulnerabilities: As the coronavirus pandemic forced millions of people to stay home over the past few days, Zoom suddenly became the video meeting service of choice: Daily meeting participants on the platform surged from 10 million in December to 200 million in March.
This surge in users have also got the cyber criminal’s attention. Recently (16th Apr), 2 new massive Zoom hacks were uncovered. In one incident, a security researcher found a way to access -- and download -- a company's videos previously recorded in the cloud through an unsecured link. The researcher also discovered that previously recorded user videos may live on in the cloud for hours, even after being deleted by the user. Even the login credentials of Zoom users are being sold in the dark web.
It’s not only Zoom, there are many other apps being used by a remote workforce that are putting organizations at risk.
- Cybersecurity Tips for Organizations in COVID-19
It’s important for businesses and employees to know and follow cybersecurity basics/hygiene. All organizations should practice a good cyber hygiene and ensure that their governance and enterprise risk management (policies, procedures, and controls) is effective and is enforced appropriately for the remote workforce.
Given below is the list of tips which will help organizations strengthen their security hygiene and be prepared for challenges and risks from COVID-19 cyber-attacks:
Cybersecurity Checklist
Organizations can enforce this checklist issued by INTERPOL as shown in picture below to their employees who are working from home. We have divided our cyber security tips into three sections: Precaution, Identification, and Action.
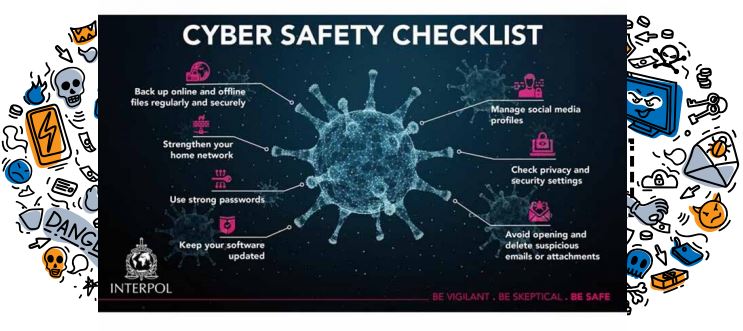
1. Precaution: As rightly said, prevention is better than cure. This is true for cyber security as well, especially in the current scenario. Employees should know the do’s and don’ts while working remotely.
- Be skeptical of emails from unknown senders or familiar people (like your company’s CEO or your doctor) who do not usually communicate directly with you.
- Don't click on links or open attachments from those senders.
- Don't forward suspicious emails to co-workers.
- Don’t use the office laptop for personal use.
- Don’t use weak passwords for your home network -- because if the home network is compromised, hackers will have a good shot at getting into the work network.
- Increase vigilance – Be vigilant not to spread COVID-19, and we also need vigilance in protecting our digital infrastructure.
- Keep backups: All institutions, including hospitals and public health organizations, should have recent back-ups (a few copies with a few stakeholders) that would allow them to rapidly restore services in the event of a ransomware attack.
- Ask others: If you are expecting an email, verify with your co-workers (for example, if you receive a strange email claiming to be your friend, try calling your friend over the phone to double-check that it’s from them)
2. Identification: There are certain ways by which employees can identify the social engineering attacks (if an email, link, or attachment is malicious or not). Organizations should communicate and train their employees so that they can differentiate between malicious and authorized emails, links, attachments etc. This will help organizations to secure their employees from most of the traps used by cybercriminals.
Spoofing email signals: These email address look like original email addresses of an authorized entity -- slight character changes that make email addresses appear visually accurate — a .com domain where it should be .gov, for example. To handle this situation, before opening or clicking on any link in an email, look for the slight changes in email addresses in the “From:” and “To:” sections.
- Grammatical errors in the text of the email; they’re usually a sure sign of fraud.
- Hover over any link to see the address and report the suspicious address.
3. Action: Once the user is skeptical and suspects a malicious attack vector, they should responsibly escalate to the concerned team so that team can communicate the threat to other employees and save them from the trap of cyber criminals. This step is very important because not everybody in an organization is equally aware of cybersecurity, and the weakest link can help cyber criminals to breach an organization. Also, security teams should be deploy tested and robust tools and technologies used to make sure that employees are secure from most of the attack vectors.
- Take precautions not to fall into the trap laid by cyber criminals.
- If you receive any suspicious email, report it to the IT or security department.
- Install the corporate-approved anti-phishing filter on browsers and emails.
- Use the corporate-approved anti-virus software to scan attachments.
- Never donate to charities via links included in an email; instead, go directly to the charity website to donate --- these links might be malicious or redirect to malicious website.
- Prioritize governance, risk, and compliance in cybersecurity programs: The reality that many organizations do not have proper policy and processes to maintain the remote workforce, and other challenges which arise from COVID-19, has raised an alarm to their preparedness for such conditions. It’s important to review and revise company policies and procedures. Even if employees are working from home, they still need to adhere to company policies. As all the lines of defense are working remotely, it becomes hard to manage policies manually.
Strengthen your perimeter:
- Use security solutions to proactively identify threats and fix them before attackers can penetrate your systems
Use continuous automated risk monitoring – end point protection
- Monitor devices of the first lines of defense or other end point devices of employees remotely, reducing exposure to hackers.
- Protect devices against standard and advanced malware.
- Test security software to make sure it works as it should and use it in your broader detection-and-monitoring program.
- Harden and patch your devices 2 3
Secure third-party apps and other external-facing applications:
- Employees are working remotely and using many third-party tools like Zoom, which again increases the attack surface, and can be a cause of a breach. As a best practice, employees should only use approved application in corporate devices.
- Even employees who are using their home network for office work should avoid using malicious and unapproved tools because if the home network is compromised, there are good chances of the corporate account getting compromised as well.
- Organizations should use multifactor authentication and risk-based authentication, especially for applications that would allow a supplier (or a cybercriminal posing as a supplier) to change bank account information, divert payments, or make other changes that may impact financial payments which can be the main motive for hackers.
Strengthen your remote access management policy and procedures.
Implement multifactor authentication for VPN access, IP address whitelisting, limits on remote desktop protocol (RDP) access and added scrutiny of remote network connections. And keep patching all access management software on a timely basis
Use a collaborative approach: (Gain a full view into your risks):
- Cybersecurity is not only the responsibility of the security team. The cybersecurity of an organization is as strong as its weakest link. Any weak link can cause a breach.
- Organizations should team up with other functions — including Financial Controls, Treasury and Fraud teams — to sharpen fraud prevention and detection. This will broaden their view of threats and risks during the crisis.
Increase security awareness and training to employees:
- As for most of the organizations, this might be the first time that all three line of defense are working remotely and many of the employees are probably not aware of cybersecurity best practices for working remotely (the do’s and don’ts).
- As employees are the first line and defense as well as easiest target for hackers, organizations must make sure that employees are aware and trained about these best practices. Organizations should also conduct some social engineering exercises internally to test their defenses.
In conclusion, just following this checklist is not enough. Organizations should make sure that cybersecurity best practice are inbuilt in their culture. It’s the entire organization’s responsibility to fight against cyber criminals.
During this crisis, besides cybersecurity, organizations are grappling with many other kinds of risks like workforce effectiveness, other operational risks, third party and vendor risks, supply chain risks etc. Organizations must monitor all these risks and make sure they are identified and managed without impacting business performance or corporate reputation.
At MetricStream we understand the challenges organizations are facing in this pandemic and have launched a COVID-19 solution to help organizations stay resilient through this crisis. With this solution, organizations will have the ability to manage information, processes, and responses, and take better, real-time decisions that impact employees, business leaders, customers, vendors and partners.

Subscribe for Latest Updates
Subscribe Now





