

ConnectedGRC
Drive a Connected GRC Program for Improved Agility, Performance, and Resilience
-
BusinessGRC
Power Business Performance and Resilience
Discover ConnectedGRC Solutions for Enterprise and Operational Resilience
Explore What Makes MetricStream the Right Choice for Our Customers
Discover How Our Collaborative Partnerships Drive Innovation and Success
- Want to become a Partner?
Find Everything You Need to Build Your GRC Journey and Thrive on Risk
Learn about our mission, vision, and core values
The Chief Risk Officer’s Role in 2018 and Beyond
Managing the Challenges and Opportunities of a Digital Era
Overview
Over the last decade, Chief Risk Officers (CROs) have become indispensable to executive teams – particularly in their role of managing risk appetites, developing a risk framework and policies, and acting as an advisor to the board and C-suite. However, as enterprises set sail into the new and often unpredictable waters of the digital age, the responsibilities of the CRO are swiftly evolving.

Two key factors are driving this shift. The first is the rapid disruption in traditional business models. Companies today are building billion-dollar enterprises simply by aggregating goods or services from different sources onto a single platform. Meanwhile, with the advent of the fourth industrial revolution, technology is reinventing the way we do business. Blockchains are radically simplifying banking transactions, while the internet of things (IoT) is changing the way we gather and analyze data, and artificial intelligence is transforming workplace productivity.
So, what does all this mean for the CRO? Essentially, as technologies and business models change, so do the associated risks. Back in 2013, cyber incidents didn’t even feature in the Allianz Barometer of top 10 global business risks. Today, it is the #1 business risk in the US and UK, and #2 business risk globally.
CROs are uniquely positioned to not only manage and mitigate these risks, but to also help the business take advantage of the upside opportunities for innovation and growth. It’s a chance to guide the enterprise towards exceptional performance in a fast-changing digital era. While that’s a challenging role—one that requires CROs to venture into new and complex risk areas such as cybersecurity risks, data privacy risks, third-party risks, and conduct risks—it’s also an opportunity to add real value to the business.
New Roles of the CRO
1. Guarding the Digital Universe
Enterprises today are privy to an unprecedented amount of digital data on their customers. Much of this data is highly sensitive, and can be misused easily by hackers and other cyber criminals looking to extort money or simply create chaos. Therefore, it isn’t surprising that data related risks are ranked as the top emerging risk over the next five years by both global banks and regulators in the eighth annual global bank risk management survey conducted by Ernst & Young (EY) and the Institute of International Finance (IIF).
Effective data protection begins by appointing a data custodian or guardian—someone who understands the risks surrounding the data universe, and ensures that there are sufficient mitigating controls, processes, and policies in place. The CRO is often best suited to this role by virtue of his or her in-depth understanding of risk management. In fact, a recent MetricStream Research survey on IT risk management found that in more than a third of banks and financial services institutions (36%), the CRO is responsible for IT risk management programs that include data related risks.
Traditional Role of the CRO
• Act as an objective and unbiased advisor to the business
• Reduce income and valuation volatility
• Be a custodian of the risk appetite
• Implement a risk culture
Additional Role of the CRO
• Be a guardian of the digital universe
• Enable digital innovation
• Build cyber risk resilience
• Leverage risk technology to predict risk outcomes
• Integrate digital risks into the ERM framework
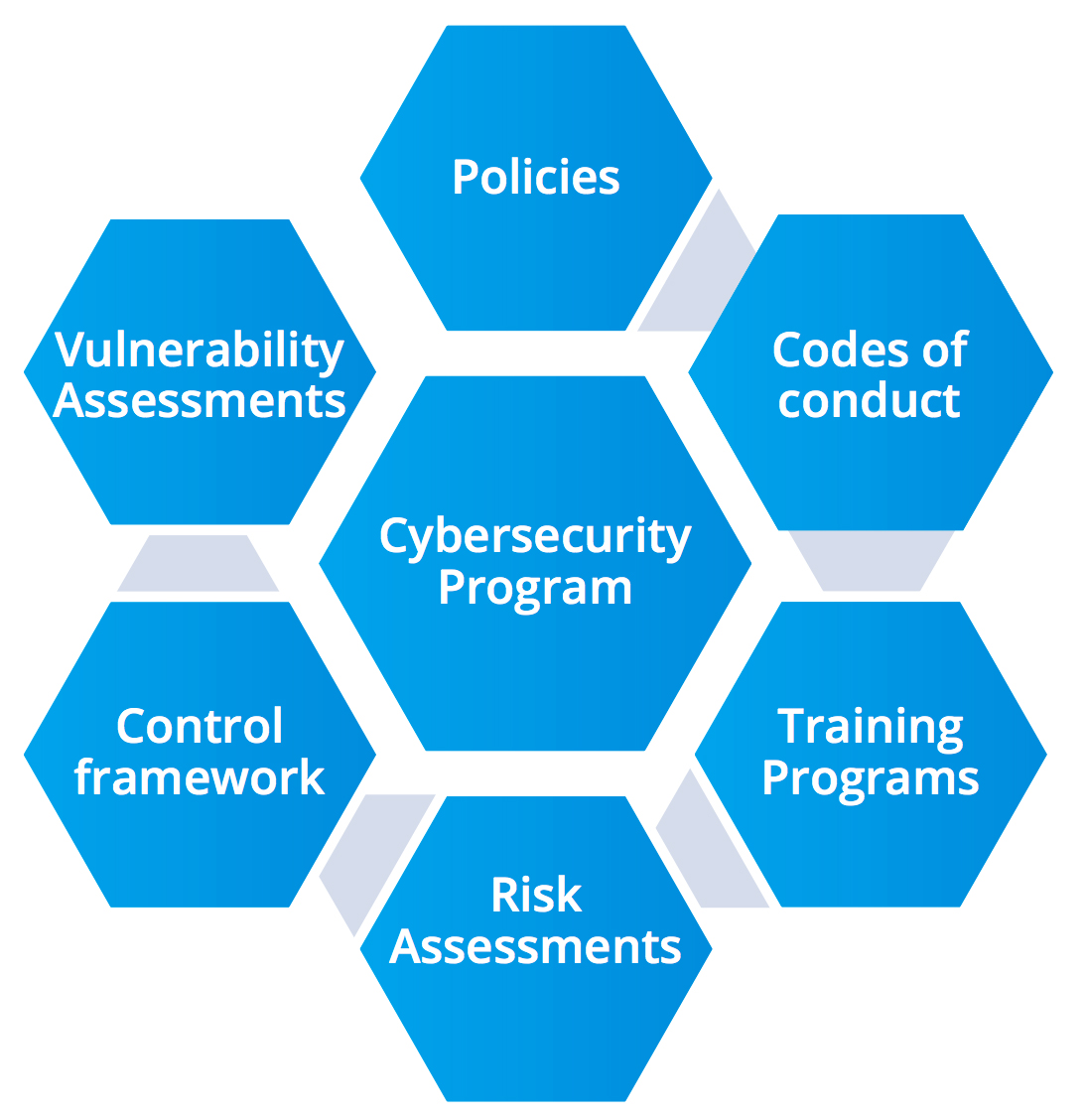
5 Point Cybersecurity Checklist for the CRO
• Build a cybersecurity strategy that brings together multiple security elements into a single, collaborative program
• Strengthen cybersecurity policies
• Assess and rank information assets based on their criticality and inherent risks
• Ensure appropriate digital controls, including patches for vulnerabilities in critical assets
• Align with IT compliance frameworks such as NIST, COSO, COBIT and ISO 270011
Some organizations may already have an IT security team to manage data risks, while others may rely on their Chief Information Officer (CIO), Chief Information Security Officer (CISO), or even their Data Protection Officer (DPO) as mandated by the EU General Data Protection Regulation (GDPR). However, even in these scenarios, it’s important for the CRO to be involved because data security isn’t just an IT risk – it’s an enterprise risk, and a top risk at that. What’s more, data security risks don’t exist in isolation. They often amplify the impact of other business risks such as compliance risks, reputational risks, and even financial risks.
The CRO needs to be able to understand these risk inter-relationships – to determine how a risk like a data breach can influence other enterprise risks, and be influenced in return. The key to do that is to build a cohesive risk data governance model – one that integrates and maps all enterprise risks into a single framework along with the associated controls and control tests. This risk data model can then be mapped to the business universe, compliance universe, and audit universe for a clear and contextual view of risks, which enables the CRO to take informed steps towards protecting digital assets.
2. Enabling Digital Innovation
While the data that the CRO “guards” is vulnerable to multiple risks, it is also a treasure trove of insights into what customers and prospects might be searching for, which marketing strategies they respond to best, how they can be convinced to increase their investments, and much more. Using this data in an ethical and legal manner is critical, and that’s where the CRO comes in. He or she can help the business optimize the value of their data without compromising on its security, privacy, and confidentiality. In other words, the CRO can propel the organization’s digital innovation agenda forward, while also stepping on the brakes whenever required to ensure that data is used ethically and securely.
The other aspect of the CRO’s role as enabler of innovation lies in helping the business keep up with the changes in technologies and business models. Markets across the world are being disrupted faster than ever, and if companies don’t evolve at the same pace, they could be shunted out swiftly. For CROs, that means shedding their traditional and often misguided reputation as corporate naysayers or prophets of doom and gloom, and instead becoming the facilitators and partners that the business needs them to be. Of course, they must continue to be the voice of reason in the C-suite, but they must also understand that in a rapidly changing digital era, time is critical, and if the business wants to get the rewards it seeks, it has to take risks. The key is to understand those risks well enough, so that decision-makers know exactly how and where to capitalize on the upside opportunities.
Better risk understanding comes when the three lines of defense work together like a well-oiled machine i.e. when risk information and intelligence flow quickly from the front lines up to the risk management function and other second line groups (e.g. compliance management), onward to the internal audit function, and finally to the management team and board who can then use these risk insights to make informed decisions that put the company ahead of the innovation curve.
There is one important partner in innovation and growth that the CRO cannot afford to overlook – third parties. They are often at the heart of operational processes, and can be critical to a company’s success. However, as we saw with the Target cyberattack and many others since, a third-party risk such as a security vulnerability can have a catastrophic impact on everyone downstream of the chain.
To mitigate these risks, organizations need to first understand which third parties have access to sensitive data. These entities then need to undergo regular due diligence, risk assessments, continuous third-party monitoring activities, and audits. The CRO is well-positioned to drive these activities, enabling the business to gain value from their third-party relationships while keeping the associated risks in check.
3. Predicting Business Outcomes
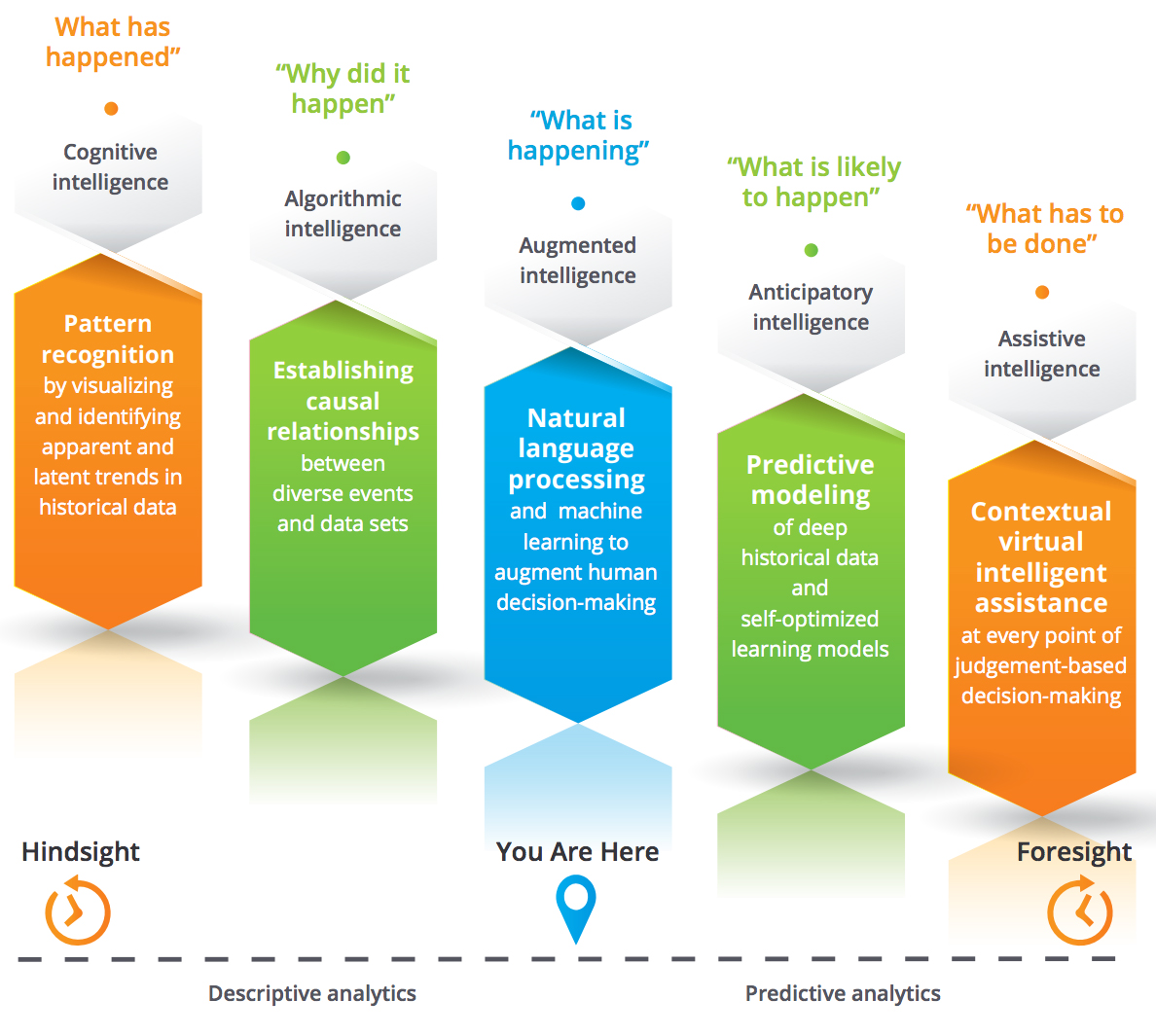
As both a guardian of the data universe, and an enabler of digital innovation, the CRO has access to a significant amount of risk insights and intelligence. Earlier, these insights might have been more retrospective i.e. analyzing risk incidents that have already occurred to understand what happened and why. But today, CROs have the tools to look ahead – to predict potential risk incidents and their impact with greater accuracy and speed than ever.
New generations of risk management solutions come with automated data mining, scenario modeling, and forecasting capabilities that provide an in-depth glimpse into what risks are likely to occur, and what has to be done to keep them in check. Cognitive and algorithmic intelligence are giving way to augmented and assistive intelligence based on technologies such as natural language processing and predictive modeling which serve to augment and accelerate decision-making.
Today’s solutions are also designed to be adaptable across mobile devices and business critical apps in such a way that risk management processes can be seamlessly and deeply embedded into the organization’s culture and DNA. User interfaces have become highly intuitive and engaging, helping CROs and their teams accomplish their risk management tasks with ease. Interactive reports, as well as hover cards and data explorers, offer the ability to slice, dice, and analyze risk data from various perspectives. All these capabilities allow CROs to be a true partner to the business, keeping potential risks under control, while steering the enterprise towards better growth and performance.
4. Building Risk Resilience
CROs have traditionally focused on preventing risk incidents. However, when it comes to cybersecurity, prevention isn’t always a fool-proof strategy. Cyberthreats are growing more sophisticated, and despite an organization’s best
efforts at defense, an attack or data breach could occur. Therefore, CROs need to prepare for the worst by having a robust business continuity and resilience strategy in place.
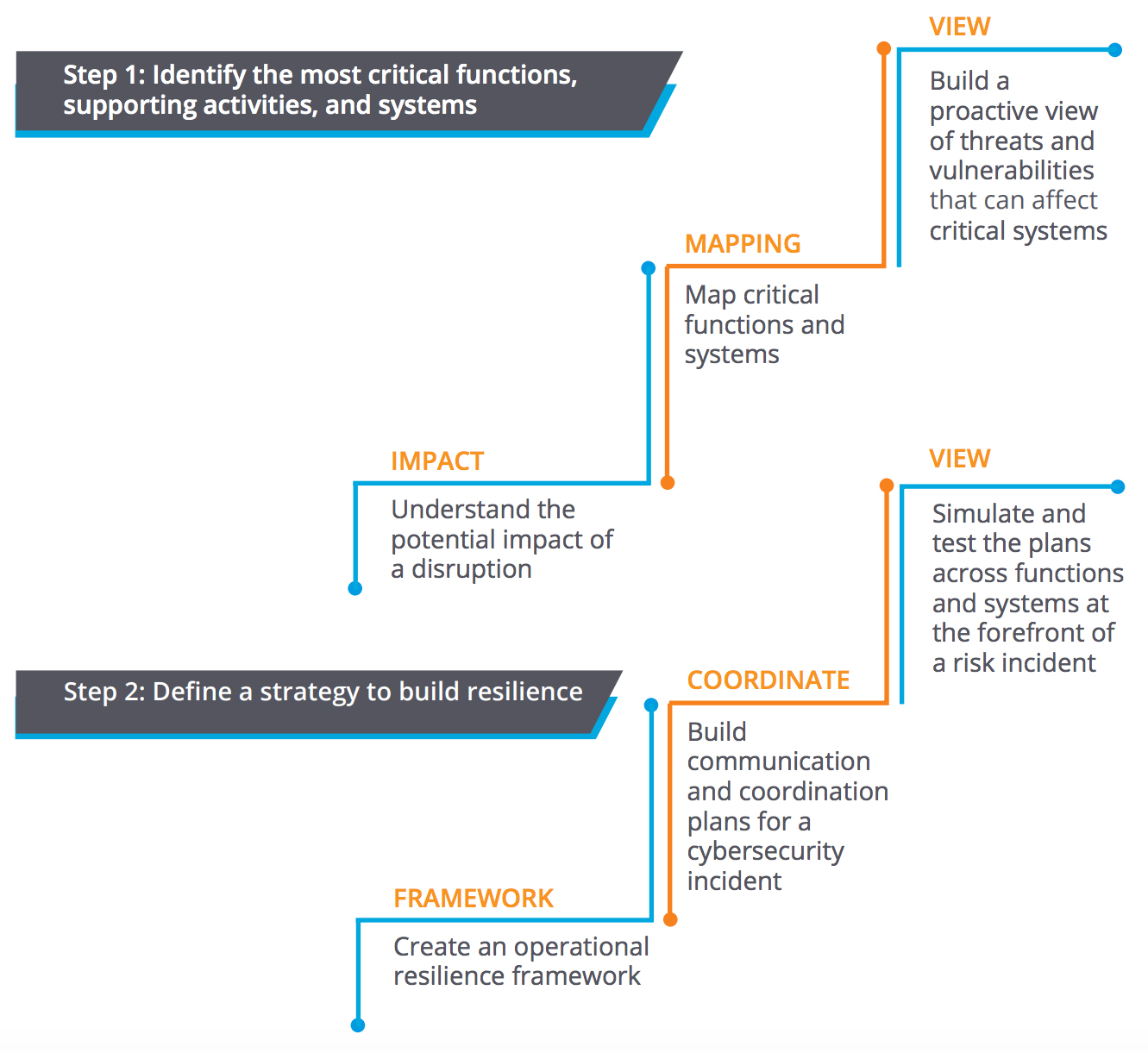
The first step in that direction is to understand the most critical information assets in the enterprise, and then determine how they can be impacted by a disruption such as a cybersecurity attack. Accordingly, a business continuity plan can be developed with clearly defined roles and responsibilities, as well as steps for communication and coordination. All plans and processes must be tested at regular intervals, so that employees and stakeholders know exactly what they need to do if a disruption occurs.
At the end of the day, business resilience is what matters. And when the CRO leads these efforts, the organization can be well-prepared with a holistic strategy that focuses not only on defending against threats, but also bouncing back swiftly from adverse incidents that do occur.
How MetricStream Can Help
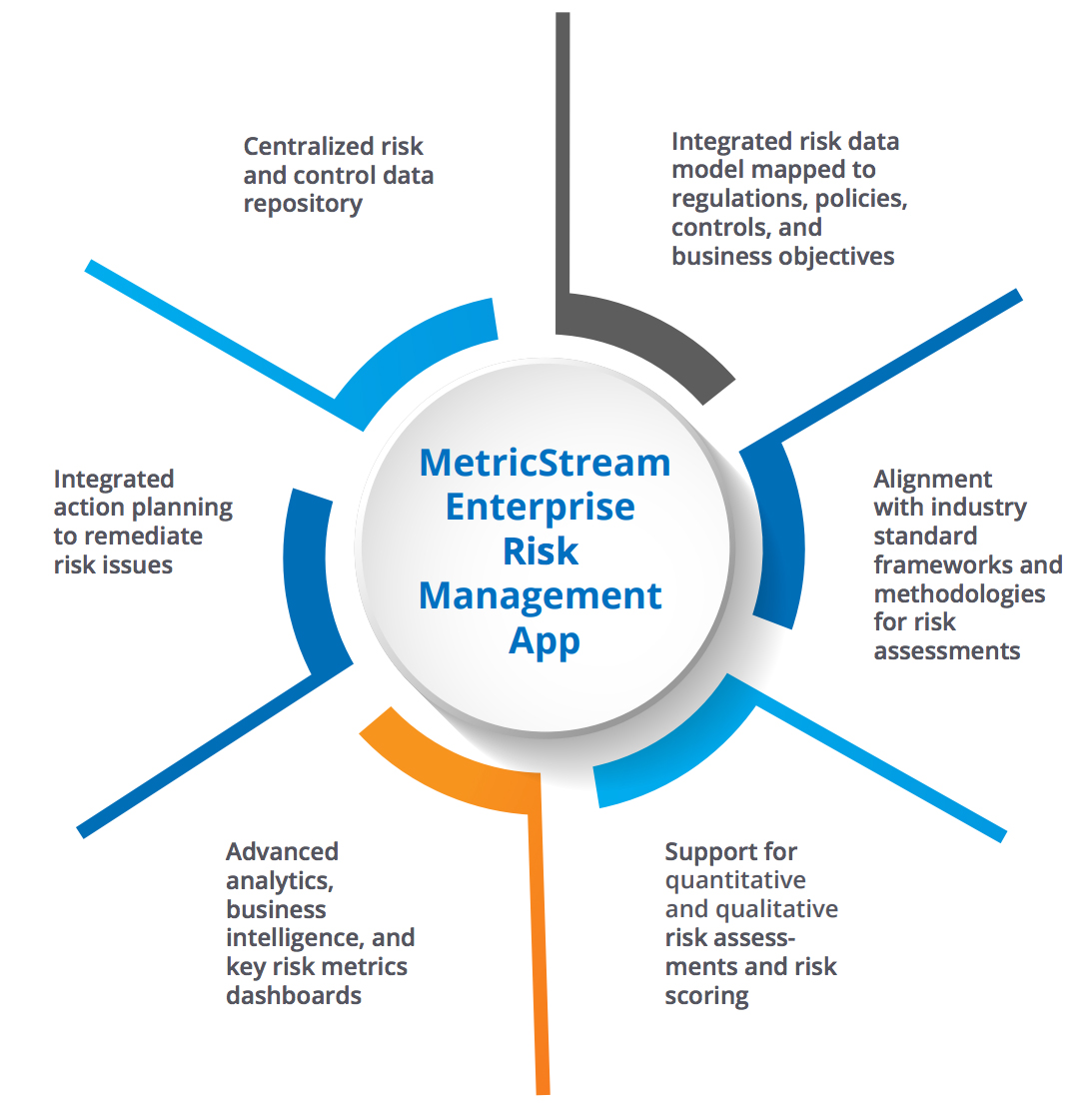
MetricStream’s Enterprise Risk Management App enables a simple, yet effective approach to risk detection, evaluation, mitigation, and monitoring, while also providing real-time risk intelligence to support decision-making.
MetricStream M7 GRC Platform
MetricStream apps are built on the M7 GRC platform which provides:
• A responsive and personalized interface designed for risk professionals
• High configurability to meet specific risk and control requirements
• Mobile readiness, enabling assessments anywhere, anytime
• Real-time risk intelligence and insights for better decisions
• Architecture that is fast, lean, and ready for the future

Subscribe for Latest Updates
Subscribe Now





