Introduction
Staying on top of cyber governance, IT risk, and compliance trends is a business imperative in today's volatile environment. 2022 was a tough year for IT and cyber risk – and will affect how businesses manage cyber risk and compliance in 2023.
There has been a sharp escalation of ransomware, social engineering, and third-party cyber-attacks along with the increase in geopolitical crises, state-sponsored attacks, and cyber warfare. Digital transformation also continues, with hybrid work and ‘bring your own device’ mandates compelling security teams to design and maintain effective controls. And, as more businesses digitize and automate their processes, attack surfaces will continue to expand, making them more vulnerable to external threats.
Rapid cloud adoption has also increased risk exposure. According to CloudEra, the top two Cloud Service Providers (CSPs) have a combined market share of 60.5%. While a public cloud provides a scalable, robust, and distributed IT environment, ensuring cyber resilience in the cloud is an increasing concern. In 2020, the Uptime Institute documented 21 cloud/internet major outages with substantial financial or other negative repercussions.
Organizations must also contend with evolving IT standards and emerging regulations. Streamlining and simplifying compliance with cyber frameworks such as NIST CSF, HIPAA, ISO 27001, COSO, SOC 2, CCPA, PCI-DSS, and CMMC 2.0 is imperative.
MetricStream is committed to helping the cyber community succeed in the face of risk and uncertainty. Based on our interactions with customers, thought leaders, and our own market research, here are the top 10 cyber risk trends that you can use as you prepare for 2023.
“Cyber risk management applies to all industries, all sectors, and organizations of all sizes. Anybody with an internet connection has exposure to cyber risk.”
Prasad Sabbineni, Co-CEO and Chief Technology Officer, MetricStream
What’s Ahead for 2023? Ten Cyber Risk Trends
Automation and Artificial Intelligence (AI)
Cyber attacks are becoming increasingly sophisticated, with cybercriminals resorting to artificial intelligence and sophisticated social engineering tactics. Hyper automation is transforming modern and legacy processes using artificial intelligence (AI), machine learning, and robotic process automation (RPA), so organizations gain cost and resource efficiencies to thrive in a competitive landscape. Hyper automation is especially relevant given the ongoing shortage of cybersecurity skills among employees.
Gartner predicts that hyper-automation will become an increasingly prominent characteristic of business continuity and digital transformation across industries. Cyber risk management will not be an exception. In 2022, the global market for technologies that enable hyper-automation was anticipated to reach $596.6 billion. By 2024, hyper-automation technologies could reduce operating expenses by up to 30%.
Hyper automation will equip cyber specialists, chief security officers, and CISOs to implement a robust, proactive cyber risk management and compliance program. Continuous sensing, discovery, and detection of security risks enable IT to prioritize significant issues for resolution and discover what is being actively targeted. The goal of this automation is to eventually lead to autonomy with processes running continuously and sending threshold alerts and notifications without human intervention.
Most companies recognize that proactive review is vital to compliance success. As a result, there is an active move to adopt real-time continuous monitoring models rather than point-in-time reactive models.
Continuous control monitoring or real-time monitoring of activities helps organizations proactively identify control gaps and improvement areas before a serious lapse occurs.
Risk-First Cloud Strategy
While a 'cloud-first' approach and cloud migration strategy offer several advantages, especially efficiency and convenience, the cloud also introduces a new set of cyber risks. In fact, security risks are often considered the greatest deterrent to a cloud-first strategy. Moreover, the growing number of policies and rules regarding data storage means that businesses regularly risk being fined or losing customer trust due to minor lapses that can quickly spiral out of control.
For these reasons, investing in cloud security, risk management, and creating resilience against data loss and unknowns will be a top priority in the coming year. Cloud security, IT compliance, and risk management solutions will also ensure proactive threat and vulnerability monitoring, higher resilience and compliance, and more stakeholder confidence.
Gartner discovered that 75% of security breaches could be traced to improper privilege management. To avoid such lapses, everyone in the business—from the CEO to the software developers—must adopt a risk-first approach to cloud services.
Increased Regulatory Reporting and Transparency
Governments and regulatory agencies are actively taking measures to help organizations secure their IT and cyber-infrastructure. As cyber-attacks continue to rise, government agencies have begun to provide new legislation and guidelines for firms to bolster their cybersecurity, compliance, and risk management. In 2021, the market for regulatory reporting solutions had a revenue of approximately $4.5 billion. It is anticipated to reach $20.2 billion by 2032, with a CAGR of 14.7% from 2022 to 2032.
Significant legislative amendments have emerged in recent years, including the US Cyber Incident Reporting for Critical Infrastructure Act (CIRCIA), cyber security, and Europe’s DORA. We expect this trend to continue well into 2023 and beyond.
To maintain compliance, organizations must assume the responsibility of being updated on the proposed regulations and view them as an opportunity to grow in cybersecurity transparency. Aligning cyber risk management programs to regulatory requirements and frameworks and adopting industry best practices help organizations prepare for growing compliance standards and regulatory reporting. Solutions like autonomous control testing also play a huge role here. Manual testing and monitoring will no longer serve as regulations and standards become increasingly complex.
Qualitative Plus Quantitative Cyber Risk Assessments
2023 will see an increased emphasis on ‘true risk assessment,’ a 360-degree perspective of risk that combines qualitative and quantitative risk assessments to gain a panoramic visibility into organizational cyber risk posture.
Qualitative cyber risk assessments like heatmaps and high, medium, and low ratings help provide an overview of the likelihood, severity, and effect of risks and the overall risk landscape. They work well for high-level, at a glance views.
Quantitative risk assessments, on the other hand, help risk practitioners assign a monetary value to risk. An organization can determine whether its risk exposure matches its risk appetite, tolerance level, investments needed to improve controls, and other factors by evaluating both financial and non-financial risks.
Together, qualitative and quantitative provide a balanced perspective of risk that’s easy to share and justify with your board and senior leaders.
Understanding which risks to tackle first, how to quantify cyber risks in monetary terms, and where to focus cybersecurity investments are critical decisions that CIOs and CISOs must grapple with.
MetricStream’s deep-dive guide into cyber risk quantification answers all these questions and offers tips and best practices that have helped other players in the space.
Escalation of Third-Party Cyber Risks
Cyber risks posed by third and fourth parties have accelerated and will continue to be a major risk for organizations. In Third-Party Risk: A Turbulent Outlook Survey Report 2022, 60% of respondents said that had experienced an IT security incident in the past two years due to a third-party partner with access privileges. And when it came to damages, some paid as much as $1 million or more with 45% incurring at least $100,000.
Businesses will need to put plans in place to strike a balance between monitoring their suppliers' cybersecurity hygiene and overburdening them with demands. Third and fourth parties will have to comply with security that supports the enterprise's goals, both technically and in contract-driven risk-mitigation components. To ensure collaboration and safety for all parties, businesses must bring third and fourth parties into their cyber risk perimeters.
Integrated Approach for Interconnected Risks
Enterprise risk management is a highly demanding and complex business function. Organizations must simultaneously address many risks—cyber, geopolitical, third-party, physical, privacy, financial, ESG, etc. As the business environment becomes more digitized and interconnected, these risk categories too evolve and become more interlinked.
Traditional risk management approaches, which rely on isolated processes, manual labor, and spreadsheets, do not provide comprehensive visibility into risks and their interconnectedness. By analyzing risks in isolation, GRC professionals will not understand the cascading impacts of risk, nor can they devise effective business resilience strategies.
Organizations must therefore look at adopting a future-ready GRC strategy built around an integrated risk management approach. They must not only integrate cyber governance, risk management, and compliance processes but also look at cyber risk and compliance management as part of the overarching GRC program and align it to business objectives and strategic goals. This was corroborated as far back as 2019 in Deloitte's Risk Management Survey. When combined with automated and autonomous workflows, a forward-thinking and resilience-focused GRC approach will increase the organization's readiness to tackle future risks.
The growing web of risk relationships has made enterprise risk management increasingly complex. When these risks are not evaluated holistically, they continue to evolve within their silos, eventually leading to a systemic, industry-wide collapse. Here are five key recommendations to help organizations efficiently manage interconnected risks.
The Rise of the Business-Oriented CISO
As businesses continue to evolve with digital-first, cloud-first strategies, so is the role of CISO in today’s dynamic enterprises. The CISO is not only expected to work directly with C-level executives and the board of directors, keeping them informed about cybersecurity threats and mitigation strategies but also help them make sound strategic business decisions.
As the board becomes more ‘cyber-aware,’ they expect CISOs to disclose the organization's cybersecurity posture to them routinely. According to Gartner, “By 2025, 40% of boards of directors will have a dedicated cybersecurity committee overseen by a qualified board member, up from less than 10% today.”
A CISO does not merely have to be a technological specialist. While they need to be aware of the newest technology and security issues, they must also be multifaceted, playing a pivotal role in developing the organization’s cyber risk culture. Along with a deep understanding of cybersecurity and an undivided focus on cyber resilience, they must also possess a strategic vision—the ability to look at the bigger picture as part of the entire C-suite and make cyber risk-aware business decisions.
Continuous learning, mastery of new abilities, and deep domain knowledge will be critical components in developing the next generation of CISOs.
Industry-Wide Collaboration
Organizations increasingly acknowledge that no single entity, government, or vendor can address the cybersecurity problem. Interoperability enables the ‘power of the crowd’ to be used as a ‘force multiplier against increasingly sophisticated adversaries.’
With this principle in mind, 2022 saw the birth of the OCSF (Open Cybersecurity Schema Framework)—an open-source project bringing together key technology and cybersecurity organizations to detect and prevent cyberattacks more quickly and efficiently. It is a crucial step in standardizing the data that teams depend on and allows vital information to be integrated and shared, enabling efficacy and security. This is something that we expect to see more of in 2023 and beyond.
IT Vendor Consolidation
A 2022 Gartner survey showed that 75% of organizations were pursuing security vendor consolidation in 2022. This trend will likely continue through 2023 as organizations seek to minimize the complexity of their security stack. By consolidating the number of cybersecurity vendors they engage with, companies can reduce the operational complexities associated with multiple vendors, strengthen their risk mitigation strategy, address skill shortages, improve staff productivity, and enhance visibility and reporting.
As nation-states and criminal actors launch ransomware attacks and exploit software vulnerabilities, CISOs opt to work with integrated platform providers who "already have done the work to integrate their toolsets," rather than working via multiple tools that may or may not work together.
The emergence of super solution integrators (SSIs) could also be fueling the trend. SSIs have the expertise to design, manage, and execute IT projects from beginning to end. This means they can help organizations dramatically pare down their vendor lists, helping them achieve both cost-efficiency and innovation goals.
Prioritizing a Risk-Aware Security Culture
Globally, 80% of firms experienced at least one security breach due to a lack of cybersecurity skills and awareness. Cyber risks are real, and addressing them requires recognizing that organizational security does not end with implementing a software solution but requires a cyber risk-aware mindset across the enterprise. Cyber risk management is not just the responsibility of the security team, but the entire workforce.
Increasingly, organizations are focusing on building a risk-first culture by operating with a cyber-risk-aware mindset. Senior leadership teams need a framework to facilitate an all-encompassing risk management approach. It requires an understanding that the cyber-skills gap is not just about recruiting and maintaining qualified cybersecurity professionals but about enabling workers who can independently embrace certain digital practices.
How MetricStream Can Help
MetricStream CyberGRC assists enterprises in actively managing cyber risk and compliance areas through an IT and Cyber Risk and Compliance Framework aligned with recognized security standards, allowing them to pass IT audits more rapidly and get the support of upper management. Organizations get end-to-end insight into their overall IT risk and compliance posture.
Companies can get their IT and Cyber Risk and Compliance programs up and running quickly using pre-packaged material and industry standards like ISO 27001, NIST CSF, and NIST SP800-53, and tie rules to IT controls and policy exceptions. With CyberGRC, you can:
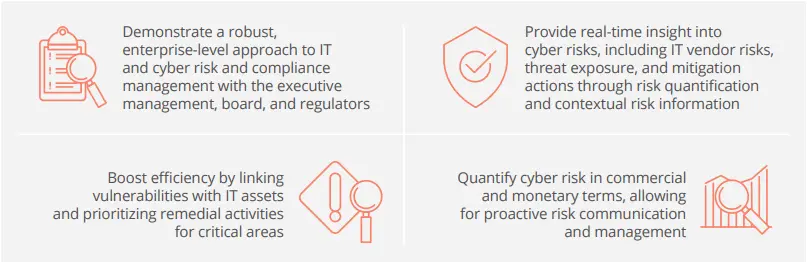
Staying on top of cyber governance, IT risk, and compliance trends is a business imperative in today's volatile environment. 2022 was a tough year for IT and cyber risk – and will affect how businesses manage cyber risk and compliance in 2023.
There has been a sharp escalation of ransomware, social engineering, and third-party cyber-attacks along with the increase in geopolitical crises, state-sponsored attacks, and cyber warfare. Digital transformation also continues, with hybrid work and ‘bring your own device’ mandates compelling security teams to design and maintain effective controls. And, as more businesses digitize and automate their processes, attack surfaces will continue to expand, making them more vulnerable to external threats.
Rapid cloud adoption has also increased risk exposure. According to CloudEra, the top two Cloud Service Providers (CSPs) have a combined market share of 60.5%. While a public cloud provides a scalable, robust, and distributed IT environment, ensuring cyber resilience in the cloud is an increasing concern. In 2020, the Uptime Institute documented 21 cloud/internet major outages with substantial financial or other negative repercussions.
Organizations must also contend with evolving IT standards and emerging regulations. Streamlining and simplifying compliance with cyber frameworks such as NIST CSF, HIPAA, ISO 27001, COSO, SOC 2, CCPA, PCI-DSS, and CMMC 2.0 is imperative.
MetricStream is committed to helping the cyber community succeed in the face of risk and uncertainty. Based on our interactions with customers, thought leaders, and our own market research, here are the top 10 cyber risk trends that you can use as you prepare for 2023.
“Cyber risk management applies to all industries, all sectors, and organizations of all sizes. Anybody with an internet connection has exposure to cyber risk.”
Prasad Sabbineni, Co-CEO and Chief Technology Officer, MetricStream
Automation and Artificial Intelligence (AI)
Cyber attacks are becoming increasingly sophisticated, with cybercriminals resorting to artificial intelligence and sophisticated social engineering tactics. Hyper automation is transforming modern and legacy processes using artificial intelligence (AI), machine learning, and robotic process automation (RPA), so organizations gain cost and resource efficiencies to thrive in a competitive landscape. Hyper automation is especially relevant given the ongoing shortage of cybersecurity skills among employees.
Gartner predicts that hyper-automation will become an increasingly prominent characteristic of business continuity and digital transformation across industries. Cyber risk management will not be an exception. In 2022, the global market for technologies that enable hyper-automation was anticipated to reach $596.6 billion. By 2024, hyper-automation technologies could reduce operating expenses by up to 30%.
Hyper automation will equip cyber specialists, chief security officers, and CISOs to implement a robust, proactive cyber risk management and compliance program. Continuous sensing, discovery, and detection of security risks enable IT to prioritize significant issues for resolution and discover what is being actively targeted. The goal of this automation is to eventually lead to autonomy with processes running continuously and sending threshold alerts and notifications without human intervention.
Most companies recognize that proactive review is vital to compliance success. As a result, there is an active move to adopt real-time continuous monitoring models rather than point-in-time reactive models.
Continuous control monitoring or real-time monitoring of activities helps organizations proactively identify control gaps and improvement areas before a serious lapse occurs.
Risk-First Cloud Strategy
While a 'cloud-first' approach and cloud migration strategy offer several advantages, especially efficiency and convenience, the cloud also introduces a new set of cyber risks. In fact, security risks are often considered the greatest deterrent to a cloud-first strategy. Moreover, the growing number of policies and rules regarding data storage means that businesses regularly risk being fined or losing customer trust due to minor lapses that can quickly spiral out of control.
For these reasons, investing in cloud security, risk management, and creating resilience against data loss and unknowns will be a top priority in the coming year. Cloud security, IT compliance, and risk management solutions will also ensure proactive threat and vulnerability monitoring, higher resilience and compliance, and more stakeholder confidence.
Gartner discovered that 75% of security breaches could be traced to improper privilege management. To avoid such lapses, everyone in the business—from the CEO to the software developers—must adopt a risk-first approach to cloud services.
Increased Regulatory Reporting and Transparency
Governments and regulatory agencies are actively taking measures to help organizations secure their IT and cyber-infrastructure. As cyber-attacks continue to rise, government agencies have begun to provide new legislation and guidelines for firms to bolster their cybersecurity, compliance, and risk management. In 2021, the market for regulatory reporting solutions had a revenue of approximately $4.5 billion. It is anticipated to reach $20.2 billion by 2032, with a CAGR of 14.7% from 2022 to 2032.
Significant legislative amendments have emerged in recent years, including the US Cyber Incident Reporting for Critical Infrastructure Act (CIRCIA), cyber security, and Europe’s DORA. We expect this trend to continue well into 2023 and beyond.
To maintain compliance, organizations must assume the responsibility of being updated on the proposed regulations and view them as an opportunity to grow in cybersecurity transparency. Aligning cyber risk management programs to regulatory requirements and frameworks and adopting industry best practices help organizations prepare for growing compliance standards and regulatory reporting. Solutions like autonomous control testing also play a huge role here. Manual testing and monitoring will no longer serve as regulations and standards become increasingly complex.
Qualitative Plus Quantitative Cyber Risk Assessments
2023 will see an increased emphasis on ‘true risk assessment,’ a 360-degree perspective of risk that combines qualitative and quantitative risk assessments to gain a panoramic visibility into organizational cyber risk posture.
Qualitative cyber risk assessments like heatmaps and high, medium, and low ratings help provide an overview of the likelihood, severity, and effect of risks and the overall risk landscape. They work well for high-level, at a glance views.
Quantitative risk assessments, on the other hand, help risk practitioners assign a monetary value to risk. An organization can determine whether its risk exposure matches its risk appetite, tolerance level, investments needed to improve controls, and other factors by evaluating both financial and non-financial risks.
Together, qualitative and quantitative provide a balanced perspective of risk that’s easy to share and justify with your board and senior leaders.
Understanding which risks to tackle first, how to quantify cyber risks in monetary terms, and where to focus cybersecurity investments are critical decisions that CIOs and CISOs must grapple with.
MetricStream’s deep-dive guide into cyber risk quantification answers all these questions and offers tips and best practices that have helped other players in the space.
Escalation of Third-Party Cyber Risks
Cyber risks posed by third and fourth parties have accelerated and will continue to be a major risk for organizations. In Third-Party Risk: A Turbulent Outlook Survey Report 2022, 60% of respondents said that had experienced an IT security incident in the past two years due to a third-party partner with access privileges. And when it came to damages, some paid as much as $1 million or more with 45% incurring at least $100,000.
Businesses will need to put plans in place to strike a balance between monitoring their suppliers' cybersecurity hygiene and overburdening them with demands. Third and fourth parties will have to comply with security that supports the enterprise's goals, both technically and in contract-driven risk-mitigation components. To ensure collaboration and safety for all parties, businesses must bring third and fourth parties into their cyber risk perimeters.
Integrated Approach for Interconnected Risks
Enterprise risk management is a highly demanding and complex business function. Organizations must simultaneously address many risks—cyber, geopolitical, third-party, physical, privacy, financial, ESG, etc. As the business environment becomes more digitized and interconnected, these risk categories too evolve and become more interlinked.
Traditional risk management approaches, which rely on isolated processes, manual labor, and spreadsheets, do not provide comprehensive visibility into risks and their interconnectedness. By analyzing risks in isolation, GRC professionals will not understand the cascading impacts of risk, nor can they devise effective business resilience strategies.
Organizations must therefore look at adopting a future-ready GRC strategy built around an integrated risk management approach. They must not only integrate cyber governance, risk management, and compliance processes but also look at cyber risk and compliance management as part of the overarching GRC program and align it to business objectives and strategic goals. This was corroborated as far back as 2019 in Deloitte's Risk Management Survey. When combined with automated and autonomous workflows, a forward-thinking and resilience-focused GRC approach will increase the organization's readiness to tackle future risks.
The growing web of risk relationships has made enterprise risk management increasingly complex. When these risks are not evaluated holistically, they continue to evolve within their silos, eventually leading to a systemic, industry-wide collapse. Here are five key recommendations to help organizations efficiently manage interconnected risks.
The Rise of the Business-Oriented CISO
As businesses continue to evolve with digital-first, cloud-first strategies, so is the role of CISO in today’s dynamic enterprises. The CISO is not only expected to work directly with C-level executives and the board of directors, keeping them informed about cybersecurity threats and mitigation strategies but also help them make sound strategic business decisions.
As the board becomes more ‘cyber-aware,’ they expect CISOs to disclose the organization's cybersecurity posture to them routinely. According to Gartner, “By 2025, 40% of boards of directors will have a dedicated cybersecurity committee overseen by a qualified board member, up from less than 10% today.”
A CISO does not merely have to be a technological specialist. While they need to be aware of the newest technology and security issues, they must also be multifaceted, playing a pivotal role in developing the organization’s cyber risk culture. Along with a deep understanding of cybersecurity and an undivided focus on cyber resilience, they must also possess a strategic vision—the ability to look at the bigger picture as part of the entire C-suite and make cyber risk-aware business decisions.
Continuous learning, mastery of new abilities, and deep domain knowledge will be critical components in developing the next generation of CISOs.
Industry-Wide Collaboration
Organizations increasingly acknowledge that no single entity, government, or vendor can address the cybersecurity problem. Interoperability enables the ‘power of the crowd’ to be used as a ‘force multiplier against increasingly sophisticated adversaries.’
With this principle in mind, 2022 saw the birth of the OCSF (Open Cybersecurity Schema Framework)—an open-source project bringing together key technology and cybersecurity organizations to detect and prevent cyberattacks more quickly and efficiently. It is a crucial step in standardizing the data that teams depend on and allows vital information to be integrated and shared, enabling efficacy and security. This is something that we expect to see more of in 2023 and beyond.
IT Vendor Consolidation
A 2022 Gartner survey showed that 75% of organizations were pursuing security vendor consolidation in 2022. This trend will likely continue through 2023 as organizations seek to minimize the complexity of their security stack. By consolidating the number of cybersecurity vendors they engage with, companies can reduce the operational complexities associated with multiple vendors, strengthen their risk mitigation strategy, address skill shortages, improve staff productivity, and enhance visibility and reporting.
As nation-states and criminal actors launch ransomware attacks and exploit software vulnerabilities, CISOs opt to work with integrated platform providers who "already have done the work to integrate their toolsets," rather than working via multiple tools that may or may not work together.
The emergence of super solution integrators (SSIs) could also be fueling the trend. SSIs have the expertise to design, manage, and execute IT projects from beginning to end. This means they can help organizations dramatically pare down their vendor lists, helping them achieve both cost-efficiency and innovation goals.
Prioritizing a Risk-Aware Security Culture
Globally, 80% of firms experienced at least one security breach due to a lack of cybersecurity skills and awareness. Cyber risks are real, and addressing them requires recognizing that organizational security does not end with implementing a software solution but requires a cyber risk-aware mindset across the enterprise. Cyber risk management is not just the responsibility of the security team, but the entire workforce.
Increasingly, organizations are focusing on building a risk-first culture by operating with a cyber-risk-aware mindset. Senior leadership teams need a framework to facilitate an all-encompassing risk management approach. It requires an understanding that the cyber-skills gap is not just about recruiting and maintaining qualified cybersecurity professionals but about enabling workers who can independently embrace certain digital practices.
MetricStream CyberGRC assists enterprises in actively managing cyber risk and compliance areas through an IT and Cyber Risk and Compliance Framework aligned with recognized security standards, allowing them to pass IT audits more rapidly and get the support of upper management. Organizations get end-to-end insight into their overall IT risk and compliance posture.
Companies can get their IT and Cyber Risk and Compliance programs up and running quickly using pre-packaged material and industry standards like ISO 27001, NIST CSF, and NIST SP800-53, and tie rules to IT controls and policy exceptions. With CyberGRC, you can:









