Introduction
To build cyber resilience today, enterprises need a proactive and continuous approach to cyber risk management. It means embedding risk management across business processes and the extended organization in such a way that customers, partners, and third-party vendors are made full-time stakeholders in cyber resilience, while the business is made fully aware of all cyber risks to make better business decisions.
In this eBook learn how organizations can achieve cyber resilience in an increasingly digitized world. Gain quick tips on how to get the board’s attention and approval on CyberSecurity investments. And finally, deep dive into how to combat cyberattacks effectively with a CyberSecurity Incident Response Program.
Four Key Areas to Achieve Cyber Resilience
Next-generation technologies such as artificial intelligence (AI), machine learning (ML), the cloud, robotic process automation (RPA), and the internet of things (IoT) are empowering enterprises to offer a range of differentiated business experiences to their customers. Yet, for cyber risk management professionals, these emerging technologies pose multiple challenges. For one, they increase the attack surface, thus requiring new mitigating controls to protect data assets while still allowing for an elevated customer experience. Secondly, these technologies introduce multiple new cyber compliance and governance requirements which require organizations to be extremely agile in their responses.
Meanwhile, as analytics are adopted to strengthen business decisions, critical and sensitive customer information is moving into data lakes, thus increasing security risks. As organizations demand a bigger API ecosystem to interact with third-party vendors, risks in the extended enterprise are growing. As mobile and cloud technologies are constantly being upgraded, new vulnerabilities are emerging. All these challenges are fundamentally altering the cyber risk landscape and rendering many traditional cybersecurity methodologies ineffective.
To build cyber resilience today, enterprises need a proactive and continuous approach to cyber risk management. It means embedding risk management across business processes and the extended organization in such a way that customers, partners, and third-party vendors are made full-time stakeholders in cyber resilience, while the business is made fully aware of all cyber risks in their decisions. Such a paradigm demands a shift in existing cyber risk management processes and perspectives.
In the following sections, we discuss four key trends that can strengthen an organization’s cyber resilience.
Automation
With increasing attack surfaces and new threat actors emerging, manual approaches to cyber risk management are no longer sufficient. Many enterprises are adopting AI and ML technologies to automate their assessments of risks, threats, and vulnerabilities across business-critical assets.
Meanwhile, behavioral analytics are helping stakeholders notice and flag unusual user patterns quickly. Incident response playbooks are accelerating risk responses to cyber incidents, while helping ensure that they are remediated in line with industry best practices. Standard IT control testing processes are being automated, so that organizations can continuously monitor controls, as well as ensure that evidence of their effectiveness is always recent and up-to-date.
All these emerging techniques are optimizing the efficiency, productivity, and accuracy of risk assessment processes, while also enabling risk intelligence to be rolled up faster to management teams for analysis and decision-making.
Quantification
Today, the number and impact of cyberattacks continues to increase. A single major data breach can cost an enterprise millions of dollars, not just in financial losses but also in reputational damage. That, in turn, raises questions about the efficacy of traditional approaches to cyber risk management.
For years, many enterprises have evaluated their cyber risks using qualitative risk assessments based on likelihood and magnitude. Yet, these assessments only provide subjective information on the most likely and severe risks. They do not usually provide quantitative data on the financial impact of these risks.
A quantified approach, on the other hand, helps assign a specific financial amount to each identified cyber risk, signifying the actual loss that an enterprise could face. This approach helps organizations align CyberSecurity with business objectives, while also optimizing cyber investments. It facilitates collaboration by requiring cyber risk teams to sit across the table from business teams, and discuss cyber risk mitigation in line with quantified risk exposures, as well as business priorities. If done effectively, it can help top management allocate cyber risk management budgets in a proactive and transparent manner.
Security by Design
As businesses strive to meet demands for agility, digitization is a must. Yet, it cannot come at the cost of poor security because the consequences, in terms of regulatory fines, financial losses, and reputation damage, can be catastrophic.
Today, many cyber teams are working hard to embed cybersecurity best practices and standards into software development processes as non-intrusively and efficiently as possible. The focus is on “security by design” which helps ensure that application security is not just one step in the software development lifecycle, but a checkpoint at every stage. It strengthens confidence in the inherent security of applications, so that cyber teams need worry only about high-risk and high-impact use cases when conducting in-depth assessments.
Today, SecDevOps methodologies are empowering application teams with APIs, test use cases, best practice guides, and automated tools to help ensure that the agility of software development is maintained, while at the same time, the application is secure by design.
Zero Trust Model
As both cyber risks and insider threats to data become too big to ignore, the zero trust model is being adopted as an important component of cyber resilience. The underlying principle is that enterprises cannot enforce less rigorous authentication and authorization protocols for insiders, compared to outsiders. If they do, they could be exposing themselves to a high degree of risk and vulnerability because insiders cannot be trusted any more than outsiders.
The zero trust model focuses on establishing user credentials, motives, and other meta-data such as location, security perimeters, and end points to determine if users can be trusted with data access. It calls for a strong governance and compliance framework to determine user access rights and authorization matrices. Privileged access rights are minimized with multi-factor authentication, identity and access management, and encryption and behavioral analytics.
With the increasing adoption of the cloud and mobile technologies, organizations have realized that information protection needs a different way of thinking. Restricting access to data based on a “never trust, always verify” approach is an effective way of protecting valuable assets.
The Way Forward
The cost of cyber incidents increases when businesses are focused only on reactive risk detection and response. To change the game, they must think ahead of their adversaries by proactively identifying vulnerabilities, and then patching them permanently. This approach will require newer technology paradigms, models, and methodologies. The cybersecurity team will need to connect with business teams more regularly to understand not just technology perspectives, but business perspectives as well.
Emerging focus areas such as automation, security by design, and a zero trust model can help ensure that enterprises have the basic controls, policies, and remediation actions working every time, on time. Meanwhile risk quantification measures can help cybersecurity teams strengthen alignment with business priorities.
However, all these measures also require a shift in human and organizational behavior. It means giving up discretionary privileges, ensuring that decisions are driven by data, and implementing additional front-end effort and scrutiny during software design. Such shifts always need a significant amount of change management and hand-holding. The ability to effect these changes and institutionalize cybersecurity measures remains the biggest challenge in the quest for cyber resilience.
5 Tips to Get the Board’s Attention on Cyber Security Budgets
As organizations go digital, cyber-attacks and their ramifications are getting bigger. These attacks can cause real losses to organizations in both financial and reputational terms, making it hard for businesses to recover quickly. With data breaches and hacks making the news almost every other day, one wonders -- is cybersecurity getting the attention it deserves at the highest levels of the organization?
According to the 2017 BDO Cyber Governance Survey, “More than three-quarters (79%) of public company directors report their board is more involved with CyberSecurity than it was 12 months ago. A similar percentage (78%) say they have increased company investments during the past year to defend against cyber-attacks, with an average budget expansion of 19 percent. This is the fourth consecutive year that board members have reported increases in time and dollars devoted to cybersecurity.”
That is heartening news. But it also points to the increasing responsibilities and expectations of Chief Information Security Officers (CISOs). To get cybersecurity budgets approved, CISOs need to be able to translate their IT security requirements into business requirements and present their case lucidly in board meetings. They need to be able to turn a regular board discussion on IT updates into an opportunity to outline the importance of cybersecurity investments or initiatives. In addition, CISOs need to establish credibility with the board and management team, so that they can secure continuous investments to future-proof the technology perimeter.
At the GRC Summit in London, MetricStream invited industry practitioners and thought leaders to identify the key steps that CISOs and other cybersecurity professionals can take to ensure that the management and board are attentive to their cyber concerns. The panel discussion, titled CyberSecurity Makes Its Way into the Boardroom: Perspectives across Stakeholders, featured Steve Durbin, Managing Director, Information Security Forum, Dr. Gerhard Knecht, Global Head of Managed Security Services and Compliance, Unisys, and Sebastian Goodwin, Head of Information Security, Nutanix.
Create a Common Language with the Business
Here are the top 5 tips from the discussion:
Cyber risks are essentially business risks. When that is clearly communicated to the board and management team, it becomes simpler to get their buy-in on cybersecurity issues. One way of linking cyber risks to business risks is to measure the real potential losses to the organization’s bottom-line and/or reputation if a given threat or vulnerability is left unrectified. These numbers can be validated with the finance and business teams. Once all the departments speak the same language about the impact of a cyber risk on the business, the board and management team are more likely to listen and give credence to the issue. The ability to unify voices across the organization on cybersecurity concerns is very important to ensure that the business is always ahead of cyber-attackers, and is prepared to handle an incident or crisis when it hits.
Let Others Do the Talking
An even better practice than creating a common language is to let allies in the business and finance teams participate actively in the CISO’s presentations. Their support can go a long way in pitching for cybersecurity investments. If the business teams can be convinced about the worth of information security in lowering their risks, they will be willing to tell the CISO’s story from their perspective. Suddenly, the CISO will find that he or she is speaking as part of a larger business team.
Make Them Uncomfortable
Many organizations fall into a trap of complacency, thinking that they won’t be targeted by cyber attackers either because they’re not big enough, or because their firewalls are strong enough. Dispelling this notion is important because, as experts repeatedly warn, it’s not a matter of if you will be breached, but when. To make boards aware of the magnitude of the issue, CISOs would do well to use loss metrics or real-life simulations of cyber-attacks. For instance, they can conjure up a scenario of a confidential information leakage from the boardroom and its potential ramifications. The board and management team can be encouraged to visualize this scenario, and then provide their views on how to potentially stop or deal with the issue.
Suggest Self-Healing Solutions
Cyber Security may sometimes seem like an insurmountable challenge, but in truth, it comes down to a few simple steps such as conducting regular employee trainings, establishing information security policies, linking these policies to corporate objectives, and enforcing rules using technology. By understanding these simple solutions, the board and management team gain better confidence in the IT department’s capabilities. CISOs can also create a simple maturity curve to represent the level of IT compliance in the organization, and plot the progress of various compliance steps as and when they are executed. This gradient view can prove to be more powerful in building the case for Cyber Security, than a binary view of safe vs. not-safe or compliant vs. non-compliant.
Do Not Complicate
The key to successfully convincing the board about cybersecurity concerns is to start from the business’s overall strategic objectives, trickle down to management goals, and then link them to information security goals. For instance, the necessity of a firewall can be emphasized by linking its purchase to improved agility in terms of scaling web portals, and growing the business. If the CISO can present a clear, simple cybersecurity plan that is closely aligned to the organization’s overall corporate objectives, the board and management team will find it hard to shoot the plan down.
At the end of the day, it’s up to the CISO to find ways of turning his or her regular “IT updates” into a “business case” for cybersecurity - one that translates complex security risks into terms that boards and management teams can understand and act on proactively. Cybersecurity today lies at the heart of an organization’s financial and reputational health. In fact, it can make all the difference to business success and performance. Therefore, a swift, comprehensive, and precise approach to cyber risk management is important, and the board’s participation in these efforts can be invaluable.
The New Combative Role of a Cyber Security Incident Response Program
We live and do business in a world fraught with cyber threat. No one is safe – whether you are a large or small organization. Nor does it matter which sector you operate in. Today, any entity that owns, or has access to the assets and information of its consumers is a target. It has now become imperative for organizations to focus on security policies and practices as the foundational structure of their overall risk-management strategy. Furthermore, organizations need to ensure compliance with new laws and regulations that govern how they protect information assets. It is also a reality that network and systems administrators alone cannot protect corporate systems and information assets–the onus falls on the organization to do so as well. All these factors point to the compelling need for organizations to have a Cyber-Security Incident Response Team (CSIRT) in place.
The ground reality, however, is quite different. According to a Cyber-Governance Health Check Report, 68% of respondents stated that their board had received no training to deal with a cyber incident. One of the biggest concerns for CISOs as well was that their employees had not received enough training. According to the Cyber Governance report, 54% of company boards view cyber-risk as one of the key threats to their business. A recent survey conducted by MetricStream further reveals that lack of investments in training, and IT GRC, is the primary reason for low cyber security maturity.
Disruptions that occur from cyber attacks not only have direct financial implications, but also impact corporate reputation and brand. The media too is quick to receive news of such breaches, creating an additional layer of complexity in managing the incident. According to Cyber Security Ventures, the annual cost implication of cybercrime is projected to reach 6 trillion US$ by 2021. This clearly demonstrates that cybercrimes can pose serious threats to businesses and the absence of a sophisticated cyber-resilience program can put organizations in jeopardy.
We must face the fact that these threats are not going to let up .The enemy is formidable; a modern day cyber- pirate. While organizations cannot always prevent a breach, a quick response to a security event can be a game-changer when it comes to minimizing the financial damage, and in protecting the business and its reputation. Adopting a proactive approach to combating cyber risks with timely stakeholder communications helps in reducing the costs associated with increased call center activity, customer education and awareness programs, brand repair campaigns, legal and compliance fines, and expenses associated with any customer settlements.
The Computer Security Incident Response Team (CSIRT), is a center of information security, incident management, and response in an organization. Establishing a CSIRT enables organizations to quickly respond to increasingly sophisticated and complex incidents such as cyber attacks. Maintaining a CSIRT program enables organizations to build trust and confidence, and also foster a culture of security in the business and the industry. One of the other advantages of having a CSIRT program is to identify and tackle the vulnerable areas of the organization with both reactive and proactive measures, so as to safeguard and secure its critical assets.
Launching a CSIRT Program
There are important considerations to be made before starting a program. Operational and technical issues, such as equipment, security, and team staffing need to be addressed. In addition, it’s critical to determine resources needed for both newly formed teams as well as existing teams, including CSIRT consultants, who can be brought on board to help with planning.
Consider incident handling and eliminating duplication of effort. Conduct a gap analysis of your current cyber program. Include your capabilities to respond to incidents and also harness there sources to alert and inform the constituency. Determine what mitigations are currently in place to deal with all potentially serious effects of a computer security related incident. When setting up a CSIRT program and CSIRT plan, focus on the basics:
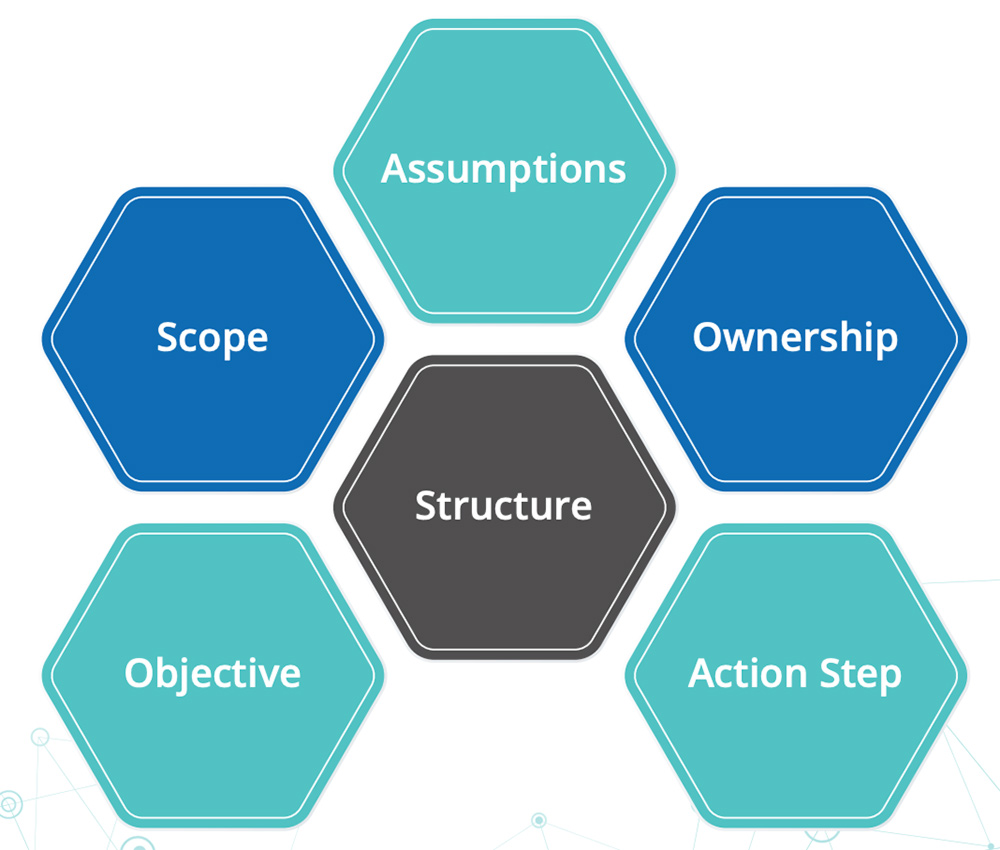
Define the CSIRT Mission
The organization’s vision is really the best starting point. Who is your constituency? Define your CSIRT mission, goals, and objectives. Select the CSIRT services to provide to the constituency (or others).Outline how the CSIRT supports its mission. Remember to determine the organizational model of CSIRT, and outline the way in which the CSIRT is structured and organized. List out the required resources, including the staff, equipment, and infrastructure needed to operate the CSIRT. Lastly, determine your CSIRT funding. How will the CSIRT be funded during its initial start up, and how will it be maintained and scaled over time?
Select Your CSIRT Combat Team
- Business Managers
- Representatives from IT
- Representatives from the Legal Department
- Representatives from Human Resources
- Representatives from Public Relations
- Any Existing Security Groups, Including Physical Security
Ideally, a CSIRT team should consist of the following staff members:
Business Managers
As the frontline of the business process, who are accountable for managing a company's activities and employees, business managers form a key component of the team. A clear understanding of the role of the CSIRT and how it can help support their business processes will be an important element of the induction process. There must be agreement regarding the CSIRT's authority over business systems, and who will make decisions if critical business systems must be disconnected from the network, or shut down.
Representatives from IT
As custodians of the IT network, a representative of the IT team will strengthen the constitution of the team. It’s important that clear guidelines are set on how the IT staff and the CSIRT should interact. The actions to be taken by the IT staff and the CSIRT members during response operations should be specified. Decisions regarding the provisions for CSIRT access to network and systems logs for analysis purposes should be clarified. Whether the CSIRT should be enabled to make recommendations to improve the security of the organizational infrastructure should be determined.
Representatives from the Legal Department
A representative from the legal department will prove crucial when legal issues need to be addressed. The time and scope of the legal department’s involvement in incident response efforts should be stated. Legal staff may be needed to review non-disclosure agreements, develop appropriate wording for contacting other sites and organizations, and determine site liability for computer security incidents.
Representatives from Human Resources
Involvement of human resources will help in developing job descriptions to hire CSIRT staff, and drafting policies and procedures for removing internal employees found engaging in unauthorized or illegal computer activity.
Representatives from Public Relations
To tackle external communications, a public relations resource needs to be on the team to handle any media queries, help develop press statements, and guidelines for information disclosure policies and practices.
Any Existing Security Groups, Including Physical Security
The CSIRT will need to exchange information with these groups about computer incidents, and may share responsibility with them for resolving issues involving computer or data theft.
Audit, and Risk Management Specialists
As threat metrics and vulnerability assessments will play a key role in planning the defense strategy, audit, and risk management specialists need to be an integral part of the team.
Set Up Your CSIRT Program

Plan the Defense
A strong defense is critical to fighting and winning the battle against cybercrime. Good procedures and processes must be put in place to defend your organization, in the present and into the future.
Here are some important steps you need to consider:
- Collect and develop better information and evidence about attack vectors and threat agents. Ensure that you have management support for the level of security required to protect sensitive information and critical assets from cyber threats. This support includes budgetary requirements that facilitate the implementation of a sound cyber security program.
- Design your supra-systems considering to counter threats that may comprise a subsystem. Build in layers of defense to segment the subsystem including interfaces that are monitored. Validate that the specifications are enforced.
- Statistics show that 80% of cyber attacks that come from within the organization may escape detection. In order to manage an uncontrolled threat environment, perform a risk assessment that is detailed and realistic. Perform a gap analysis of security controls, capabilities, and resources.
- Monitor and analyze network traffic. An enterprise security incident detection and CSIRT program are essential.
- Strategize defensive moves such as analysis to predict possible behavior and actions of attackers. Use the CSIRT to mitigate the risks and to tackle different types of breach scenarios.
- Deploy Risk Early Warning Indicators (REWI) to define security analytics and help align security metrics and analytics.
- Share information with the cyber community. For example, you can submit the malware to multi AV scanning engines such as Virus Total. The FBI also has a program called ‘Info Guard,’ where enterprises can join and share information about different attacks.
- Collaborate with information sharing and analysis centers, computer emergency response teams, or sector specific organizations such as in aerospace, and industry associations.
Defend Today for a Safer Tomorrow
CSIRT programs are a must in a world filled with complexity, new threats, and a plethora of unknowns. What remains certain is the rising probability of cybercrime and the advent of an increasingly sophisticated generation of threat agents and attackers capable of successfully attacking even the largest and most reputable organizations. Time is not on our side; defend today for a safer tomorrow.
To build cyber resilience today, enterprises need a proactive and continuous approach to cyber risk management. It means embedding risk management across business processes and the extended organization in such a way that customers, partners, and third-party vendors are made full-time stakeholders in cyber resilience, while the business is made fully aware of all cyber risks to make better business decisions.
In this eBook learn how organizations can achieve cyber resilience in an increasingly digitized world. Gain quick tips on how to get the board’s attention and approval on CyberSecurity investments. And finally, deep dive into how to combat cyberattacks effectively with a CyberSecurity Incident Response Program.
Next-generation technologies such as artificial intelligence (AI), machine learning (ML), the cloud, robotic process automation (RPA), and the internet of things (IoT) are empowering enterprises to offer a range of differentiated business experiences to their customers. Yet, for cyber risk management professionals, these emerging technologies pose multiple challenges. For one, they increase the attack surface, thus requiring new mitigating controls to protect data assets while still allowing for an elevated customer experience. Secondly, these technologies introduce multiple new cyber compliance and governance requirements which require organizations to be extremely agile in their responses.
Meanwhile, as analytics are adopted to strengthen business decisions, critical and sensitive customer information is moving into data lakes, thus increasing security risks. As organizations demand a bigger API ecosystem to interact with third-party vendors, risks in the extended enterprise are growing. As mobile and cloud technologies are constantly being upgraded, new vulnerabilities are emerging. All these challenges are fundamentally altering the cyber risk landscape and rendering many traditional cybersecurity methodologies ineffective.
To build cyber resilience today, enterprises need a proactive and continuous approach to cyber risk management. It means embedding risk management across business processes and the extended organization in such a way that customers, partners, and third-party vendors are made full-time stakeholders in cyber resilience, while the business is made fully aware of all cyber risks in their decisions. Such a paradigm demands a shift in existing cyber risk management processes and perspectives.
In the following sections, we discuss four key trends that can strengthen an organization’s cyber resilience.
Automation
With increasing attack surfaces and new threat actors emerging, manual approaches to cyber risk management are no longer sufficient. Many enterprises are adopting AI and ML technologies to automate their assessments of risks, threats, and vulnerabilities across business-critical assets.
Meanwhile, behavioral analytics are helping stakeholders notice and flag unusual user patterns quickly. Incident response playbooks are accelerating risk responses to cyber incidents, while helping ensure that they are remediated in line with industry best practices. Standard IT control testing processes are being automated, so that organizations can continuously monitor controls, as well as ensure that evidence of their effectiveness is always recent and up-to-date.
All these emerging techniques are optimizing the efficiency, productivity, and accuracy of risk assessment processes, while also enabling risk intelligence to be rolled up faster to management teams for analysis and decision-making.
Quantification
Today, the number and impact of cyberattacks continues to increase. A single major data breach can cost an enterprise millions of dollars, not just in financial losses but also in reputational damage. That, in turn, raises questions about the efficacy of traditional approaches to cyber risk management.
For years, many enterprises have evaluated their cyber risks using qualitative risk assessments based on likelihood and magnitude. Yet, these assessments only provide subjective information on the most likely and severe risks. They do not usually provide quantitative data on the financial impact of these risks.
A quantified approach, on the other hand, helps assign a specific financial amount to each identified cyber risk, signifying the actual loss that an enterprise could face. This approach helps organizations align CyberSecurity with business objectives, while also optimizing cyber investments. It facilitates collaboration by requiring cyber risk teams to sit across the table from business teams, and discuss cyber risk mitigation in line with quantified risk exposures, as well as business priorities. If done effectively, it can help top management allocate cyber risk management budgets in a proactive and transparent manner.
Security by Design
As businesses strive to meet demands for agility, digitization is a must. Yet, it cannot come at the cost of poor security because the consequences, in terms of regulatory fines, financial losses, and reputation damage, can be catastrophic.
Today, many cyber teams are working hard to embed cybersecurity best practices and standards into software development processes as non-intrusively and efficiently as possible. The focus is on “security by design” which helps ensure that application security is not just one step in the software development lifecycle, but a checkpoint at every stage. It strengthens confidence in the inherent security of applications, so that cyber teams need worry only about high-risk and high-impact use cases when conducting in-depth assessments.
Today, SecDevOps methodologies are empowering application teams with APIs, test use cases, best practice guides, and automated tools to help ensure that the agility of software development is maintained, while at the same time, the application is secure by design.
Zero Trust Model
As both cyber risks and insider threats to data become too big to ignore, the zero trust model is being adopted as an important component of cyber resilience. The underlying principle is that enterprises cannot enforce less rigorous authentication and authorization protocols for insiders, compared to outsiders. If they do, they could be exposing themselves to a high degree of risk and vulnerability because insiders cannot be trusted any more than outsiders.
The zero trust model focuses on establishing user credentials, motives, and other meta-data such as location, security perimeters, and end points to determine if users can be trusted with data access. It calls for a strong governance and compliance framework to determine user access rights and authorization matrices. Privileged access rights are minimized with multi-factor authentication, identity and access management, and encryption and behavioral analytics.
With the increasing adoption of the cloud and mobile technologies, organizations have realized that information protection needs a different way of thinking. Restricting access to data based on a “never trust, always verify” approach is an effective way of protecting valuable assets.
The Way Forward
The cost of cyber incidents increases when businesses are focused only on reactive risk detection and response. To change the game, they must think ahead of their adversaries by proactively identifying vulnerabilities, and then patching them permanently. This approach will require newer technology paradigms, models, and methodologies. The cybersecurity team will need to connect with business teams more regularly to understand not just technology perspectives, but business perspectives as well.
Emerging focus areas such as automation, security by design, and a zero trust model can help ensure that enterprises have the basic controls, policies, and remediation actions working every time, on time. Meanwhile risk quantification measures can help cybersecurity teams strengthen alignment with business priorities.
However, all these measures also require a shift in human and organizational behavior. It means giving up discretionary privileges, ensuring that decisions are driven by data, and implementing additional front-end effort and scrutiny during software design. Such shifts always need a significant amount of change management and hand-holding. The ability to effect these changes and institutionalize cybersecurity measures remains the biggest challenge in the quest for cyber resilience.
As organizations go digital, cyber-attacks and their ramifications are getting bigger. These attacks can cause real losses to organizations in both financial and reputational terms, making it hard for businesses to recover quickly. With data breaches and hacks making the news almost every other day, one wonders -- is cybersecurity getting the attention it deserves at the highest levels of the organization?
According to the 2017 BDO Cyber Governance Survey, “More than three-quarters (79%) of public company directors report their board is more involved with CyberSecurity than it was 12 months ago. A similar percentage (78%) say they have increased company investments during the past year to defend against cyber-attacks, with an average budget expansion of 19 percent. This is the fourth consecutive year that board members have reported increases in time and dollars devoted to cybersecurity.”
That is heartening news. But it also points to the increasing responsibilities and expectations of Chief Information Security Officers (CISOs). To get cybersecurity budgets approved, CISOs need to be able to translate their IT security requirements into business requirements and present their case lucidly in board meetings. They need to be able to turn a regular board discussion on IT updates into an opportunity to outline the importance of cybersecurity investments or initiatives. In addition, CISOs need to establish credibility with the board and management team, so that they can secure continuous investments to future-proof the technology perimeter.
At the GRC Summit in London, MetricStream invited industry practitioners and thought leaders to identify the key steps that CISOs and other cybersecurity professionals can take to ensure that the management and board are attentive to their cyber concerns. The panel discussion, titled CyberSecurity Makes Its Way into the Boardroom: Perspectives across Stakeholders, featured Steve Durbin, Managing Director, Information Security Forum, Dr. Gerhard Knecht, Global Head of Managed Security Services and Compliance, Unisys, and Sebastian Goodwin, Head of Information Security, Nutanix.
Create a Common Language with the Business
Here are the top 5 tips from the discussion:
Cyber risks are essentially business risks. When that is clearly communicated to the board and management team, it becomes simpler to get their buy-in on cybersecurity issues. One way of linking cyber risks to business risks is to measure the real potential losses to the organization’s bottom-line and/or reputation if a given threat or vulnerability is left unrectified. These numbers can be validated with the finance and business teams. Once all the departments speak the same language about the impact of a cyber risk on the business, the board and management team are more likely to listen and give credence to the issue. The ability to unify voices across the organization on cybersecurity concerns is very important to ensure that the business is always ahead of cyber-attackers, and is prepared to handle an incident or crisis when it hits.
Let Others Do the Talking
An even better practice than creating a common language is to let allies in the business and finance teams participate actively in the CISO’s presentations. Their support can go a long way in pitching for cybersecurity investments. If the business teams can be convinced about the worth of information security in lowering their risks, they will be willing to tell the CISO’s story from their perspective. Suddenly, the CISO will find that he or she is speaking as part of a larger business team.
Make Them Uncomfortable
Many organizations fall into a trap of complacency, thinking that they won’t be targeted by cyber attackers either because they’re not big enough, or because their firewalls are strong enough. Dispelling this notion is important because, as experts repeatedly warn, it’s not a matter of if you will be breached, but when. To make boards aware of the magnitude of the issue, CISOs would do well to use loss metrics or real-life simulations of cyber-attacks. For instance, they can conjure up a scenario of a confidential information leakage from the boardroom and its potential ramifications. The board and management team can be encouraged to visualize this scenario, and then provide their views on how to potentially stop or deal with the issue.
Suggest Self-Healing Solutions
Cyber Security may sometimes seem like an insurmountable challenge, but in truth, it comes down to a few simple steps such as conducting regular employee trainings, establishing information security policies, linking these policies to corporate objectives, and enforcing rules using technology. By understanding these simple solutions, the board and management team gain better confidence in the IT department’s capabilities. CISOs can also create a simple maturity curve to represent the level of IT compliance in the organization, and plot the progress of various compliance steps as and when they are executed. This gradient view can prove to be more powerful in building the case for Cyber Security, than a binary view of safe vs. not-safe or compliant vs. non-compliant.
Do Not Complicate
The key to successfully convincing the board about cybersecurity concerns is to start from the business’s overall strategic objectives, trickle down to management goals, and then link them to information security goals. For instance, the necessity of a firewall can be emphasized by linking its purchase to improved agility in terms of scaling web portals, and growing the business. If the CISO can present a clear, simple cybersecurity plan that is closely aligned to the organization’s overall corporate objectives, the board and management team will find it hard to shoot the plan down.
At the end of the day, it’s up to the CISO to find ways of turning his or her regular “IT updates” into a “business case” for cybersecurity - one that translates complex security risks into terms that boards and management teams can understand and act on proactively. Cybersecurity today lies at the heart of an organization’s financial and reputational health. In fact, it can make all the difference to business success and performance. Therefore, a swift, comprehensive, and precise approach to cyber risk management is important, and the board’s participation in these efforts can be invaluable.
We live and do business in a world fraught with cyber threat. No one is safe – whether you are a large or small organization. Nor does it matter which sector you operate in. Today, any entity that owns, or has access to the assets and information of its consumers is a target. It has now become imperative for organizations to focus on security policies and practices as the foundational structure of their overall risk-management strategy. Furthermore, organizations need to ensure compliance with new laws and regulations that govern how they protect information assets. It is also a reality that network and systems administrators alone cannot protect corporate systems and information assets–the onus falls on the organization to do so as well. All these factors point to the compelling need for organizations to have a Cyber-Security Incident Response Team (CSIRT) in place.
The ground reality, however, is quite different. According to a Cyber-Governance Health Check Report, 68% of respondents stated that their board had received no training to deal with a cyber incident. One of the biggest concerns for CISOs as well was that their employees had not received enough training. According to the Cyber Governance report, 54% of company boards view cyber-risk as one of the key threats to their business. A recent survey conducted by MetricStream further reveals that lack of investments in training, and IT GRC, is the primary reason for low cyber security maturity.
Disruptions that occur from cyber attacks not only have direct financial implications, but also impact corporate reputation and brand. The media too is quick to receive news of such breaches, creating an additional layer of complexity in managing the incident. According to Cyber Security Ventures, the annual cost implication of cybercrime is projected to reach 6 trillion US$ by 2021. This clearly demonstrates that cybercrimes can pose serious threats to businesses and the absence of a sophisticated cyber-resilience program can put organizations in jeopardy.
We must face the fact that these threats are not going to let up .The enemy is formidable; a modern day cyber- pirate. While organizations cannot always prevent a breach, a quick response to a security event can be a game-changer when it comes to minimizing the financial damage, and in protecting the business and its reputation. Adopting a proactive approach to combating cyber risks with timely stakeholder communications helps in reducing the costs associated with increased call center activity, customer education and awareness programs, brand repair campaigns, legal and compliance fines, and expenses associated with any customer settlements.
The Computer Security Incident Response Team (CSIRT), is a center of information security, incident management, and response in an organization. Establishing a CSIRT enables organizations to quickly respond to increasingly sophisticated and complex incidents such as cyber attacks. Maintaining a CSIRT program enables organizations to build trust and confidence, and also foster a culture of security in the business and the industry. One of the other advantages of having a CSIRT program is to identify and tackle the vulnerable areas of the organization with both reactive and proactive measures, so as to safeguard and secure its critical assets.
Launching a CSIRT Program
There are important considerations to be made before starting a program. Operational and technical issues, such as equipment, security, and team staffing need to be addressed. In addition, it’s critical to determine resources needed for both newly formed teams as well as existing teams, including CSIRT consultants, who can be brought on board to help with planning.
Consider incident handling and eliminating duplication of effort. Conduct a gap analysis of your current cyber program. Include your capabilities to respond to incidents and also harness there sources to alert and inform the constituency. Determine what mitigations are currently in place to deal with all potentially serious effects of a computer security related incident. When setting up a CSIRT program and CSIRT plan, focus on the basics:

Define the CSIRT Mission
The organization’s vision is really the best starting point. Who is your constituency? Define your CSIRT mission, goals, and objectives. Select the CSIRT services to provide to the constituency (or others).Outline how the CSIRT supports its mission. Remember to determine the organizational model of CSIRT, and outline the way in which the CSIRT is structured and organized. List out the required resources, including the staff, equipment, and infrastructure needed to operate the CSIRT. Lastly, determine your CSIRT funding. How will the CSIRT be funded during its initial start up, and how will it be maintained and scaled over time?
- Business Managers
- Representatives from IT
- Representatives from the Legal Department
- Representatives from Human Resources
- Representatives from Public Relations
- Any Existing Security Groups, Including Physical Security
Ideally, a CSIRT team should consist of the following staff members:
Business Managers
As the frontline of the business process, who are accountable for managing a company's activities and employees, business managers form a key component of the team. A clear understanding of the role of the CSIRT and how it can help support their business processes will be an important element of the induction process. There must be agreement regarding the CSIRT's authority over business systems, and who will make decisions if critical business systems must be disconnected from the network, or shut down.
Representatives from IT
As custodians of the IT network, a representative of the IT team will strengthen the constitution of the team. It’s important that clear guidelines are set on how the IT staff and the CSIRT should interact. The actions to be taken by the IT staff and the CSIRT members during response operations should be specified. Decisions regarding the provisions for CSIRT access to network and systems logs for analysis purposes should be clarified. Whether the CSIRT should be enabled to make recommendations to improve the security of the organizational infrastructure should be determined.
Representatives from the Legal Department
A representative from the legal department will prove crucial when legal issues need to be addressed. The time and scope of the legal department’s involvement in incident response efforts should be stated. Legal staff may be needed to review non-disclosure agreements, develop appropriate wording for contacting other sites and organizations, and determine site liability for computer security incidents.
Representatives from Human Resources
Involvement of human resources will help in developing job descriptions to hire CSIRT staff, and drafting policies and procedures for removing internal employees found engaging in unauthorized or illegal computer activity.
Representatives from Public Relations
To tackle external communications, a public relations resource needs to be on the team to handle any media queries, help develop press statements, and guidelines for information disclosure policies and practices.
Any Existing Security Groups, Including Physical Security
The CSIRT will need to exchange information with these groups about computer incidents, and may share responsibility with them for resolving issues involving computer or data theft.
Audit, and Risk Management Specialists
As threat metrics and vulnerability assessments will play a key role in planning the defense strategy, audit, and risk management specialists need to be an integral part of the team.

Plan the Defense
A strong defense is critical to fighting and winning the battle against cybercrime. Good procedures and processes must be put in place to defend your organization, in the present and into the future.
Here are some important steps you need to consider:
- Collect and develop better information and evidence about attack vectors and threat agents. Ensure that you have management support for the level of security required to protect sensitive information and critical assets from cyber threats. This support includes budgetary requirements that facilitate the implementation of a sound cyber security program.
- Design your supra-systems considering to counter threats that may comprise a subsystem. Build in layers of defense to segment the subsystem including interfaces that are monitored. Validate that the specifications are enforced.
- Statistics show that 80% of cyber attacks that come from within the organization may escape detection. In order to manage an uncontrolled threat environment, perform a risk assessment that is detailed and realistic. Perform a gap analysis of security controls, capabilities, and resources.
- Monitor and analyze network traffic. An enterprise security incident detection and CSIRT program are essential.
- Strategize defensive moves such as analysis to predict possible behavior and actions of attackers. Use the CSIRT to mitigate the risks and to tackle different types of breach scenarios.
- Deploy Risk Early Warning Indicators (REWI) to define security analytics and help align security metrics and analytics.
- Share information with the cyber community. For example, you can submit the malware to multi AV scanning engines such as Virus Total. The FBI also has a program called ‘Info Guard,’ where enterprises can join and share information about different attacks.
- Collaborate with information sharing and analysis centers, computer emergency response teams, or sector specific organizations such as in aerospace, and industry associations.
Defend Today for a Safer Tomorrow
CSIRT programs are a must in a world filled with complexity, new threats, and a plethora of unknowns. What remains certain is the rising probability of cybercrime and the advent of an increasingly sophisticated generation of threat agents and attackers capable of successfully attacking even the largest and most reputable organizations. Time is not on our side; defend today for a safer tomorrow.








