Introduction
Given today’s highly precarious digital operating environment, regulatory authorities and standard-setting bodies around the world regularly issue guidance, laws, regulations, frameworks, and standards to ensure organizations have the necessary measures in place to prevent cyber attacks.
NIST released the Cybersecurity Framework (CSF) with the objective of establishing a standard for organizations to effectively understand, manage, and reduce cybersecurity risk. Developed in collaboration with the private sector, NIST CSF provides a series of flexible guidelines that organizations can tailor to suit their unique cybersecurity needs. Since its release, the framework has been downloaded over two million times across 185+ countries and translated into at least nine languages.
Key Takeaways
- The NIST Cybersecurity Framework (CSF) is widely recognized as a best practice for managing cybersecurity risk. It has no certification or audit scheme like other compliance frameworks.
- The CSF provides guidelines to organizations to improve their cybersecurity posture and reduce the risk of cyberattacks. These guidelines are flexible, and organizations can tailor them to meet their unique needs.
- The version 2.0 of the framework classifies Cybersecurity Framework Functions into five categories: Govern, Identify, Protect, Detect, Respond, and Recover.
- To get started with the framework, it is essential for organizations to identify organizational assets, cyber risks, and cybersecurity risk management processes; classify the processes into the six functions of the CSF, conduct risk assessments, create current and target profiles and perform gap analysis, develop action plan to address gaps, and implement and monitor the plan.
What is NIST?
National Institute of Standards and Technology (NIST) is a non-regulatory agency of the US Department of Commerce that works to improve our economic security and quality of life by advancing measurement science, standards, and technology. The agency’s Cybersecurity and Privacy Program has published an extensive collection of standards, frameworks, guidelines, and research related to the security and privacy of information and information systems. This includes FIPS, SP 800 series, NIST CSF, and more.
What is the NIST Cybersecurity Framework (CSF)?
The NIST Cybersecurity Framework (CSF) is a set of guidelines and best practices designed to help businesses manage and reduce cybersecurity risks.It provides a structured approach to identify ,protect , detect , respond to , and recover from cyber threats.
The NIST Cybersecurity Framework (NIST CSF) is voluntary framework that guides critical infrastructure organizations to manage and reduce cybersecurity risks. It comprises standards, guidelines, and best practices for organizations to develop, implement, and improve cybersecurity programs.
The framework was first published in 2014 and then updated in 2018. In August 2023, the agency announced some of the biggest reforms to the framework with the draft CSF 2.0 in its effort to ensure the framework is aligned to the evolving cybersecurity landscape. To learn what’s new in the revised version, read our blog, Demystifying NIST CSF 2.0: What's New and Why it Matters.
In February 2024, NIST released the CSF 2.0, along with supplementary resources, which can be leveraged by organizations to understand, assess, prioritize, and communicate cybersecurity risks.
Who is Covered Under NIST Cybersecurity Framework?
NIST CSF is designed for universal application across industries and organizations, regardless of size. It offers a flexible framework for entities aiming to improve cybersecurity practices or align with compliance requirements.
The NIST Cybersecurity Framework (CSF) is flexible and adaptable to organizations of all sizes and across industries, including:
- Critical infrastructure sectors
- Small and medium-sized businesses
- Government agencies
- Non-profit organizations
- International organizations
What are NIST CSF Components?
The NIST Cybersecurity Framework (CSF) comprises three key components: the Core, which outlines essential cybersecurity activities and outcomes; the Organizational Profile, which describes the organization's current or target cybersecurity state; and Tiers, which measure the maturity and effectiveness of the organization's cybersecurity risk management practices.
As per the version 2.0, NIST CSF consists of three main components:
CSF Core:
This provides a high-level view of outcomes that can help organizations effectively manage cybersecurity risk. It includes a set of cybersecurity outcomes that are organized on the basis of six core functions:
- Govern: The Govern function involves establishing, communicating, and monitoring the cybersecurity risk management strategy, expectations, and policy. These activities are essential for integrating an organizations cybersecurity program with the overarching enterprise risk management (ERM) strategy.
- Identify: The Identify function requires understanding the cybersecurity risks faced by an organization, its assets that it wants to protect, suppliers, etc., enabling effective prioritization of its cybersecurity risk management efforts. It also includes identifying potential areas of improvement for an organization’s cybersecurity risk management policies, plans, processes, procedures, and practices.
- Protect: The Protect function includes the outcomes that help an organization safeguard its assets and prevent or mitigate cyber incidents. It includes outcomes including identity management, authentication, access control, data and platform security, resilience of technology infrastructure, and training and awareness.
- Detect: The Detect function supports the ability to discover and analyze cyber attacks, compromises, and potential adverse events in a timely manner. The outcomes of this function enable effective incident response and recovery activities.
- Respond: The Respond functions includes actions that can help contain the impact of detected cybersecurity incidents. The outcomes in this function include incident management, analysis, mitigation, reporting, and communication.
- Recover: The Recover function supports the ability to restore assets and operations affected by cybersecurity incidents in a timely manner.
CSF Organizational Profile:
This basically describes an organization’s current and and/or target cybersecurity posture based on its CSF Core’s outcomes. This component helps an organization understand, adapt, evaluate, prioritize, and communicate the Core’s outcomes in line with its objectives, threat landscape, stakeholder expectations, and requirements.
CSF Tiers:
Tiers are applied to the Organizational Profiles and enable organizations to gauge their cybersecurity risk governance and management practices. The framework outlines four tiers – Partial (Tier 1), Risk Informed (Tier 2), Repeatable (Tier 3), and Adaptive (Tier 4), with every tier building on the previous one and indicating an organization’s advancement from informal, ad hoc responses to agile, risk-informed, and continuously improving approaches.
How to Get Started with NIST CSF?
Implementing the NIST Cybersecurity Framework requires identifying organizational assets, processes, and operations; cyber risks, threats, and vulnerabilities; control measures in place; and more. Importantly, organizations need to categorize cybersecurity risk management activities under the six core functions and monitor them regularly to proactively identify and address any issues.
Here are some of the key steps that can help organizations get started with the framework:
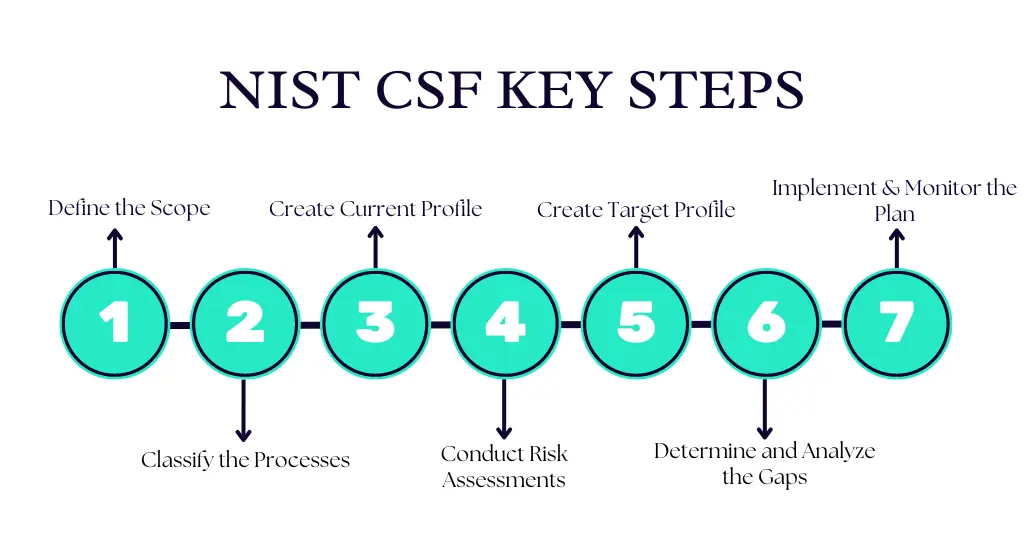
Define the Scope:
Define the scope of the project in line with strategic business goals and objectives. This includes determining risk appetite and tolerance, identifying and documenting organizational assets, business processes, and cybersecurity risks; current cybersecurity risk management processes, including key controls; business continuity, incident response, and disaster recovery plans; relevant regulations, and more
Classify the Processes:
Categorize the identified cybersecurity risk management processes, plans, and measures into the six functions as defined in the framework.
Create Current Profile:
Based on the categories and subcategories of the framework, create the current profile of how the organization views and manages cybersecurity risk.
Conduct Risk Assessments:
Assess the cyber risks faced by the organization to determine their likelihood and impact.
Create Target Profile:
Determine the target cybersecurity posture that the organization wants to achieve.
Determine and Analyze the Gaps:
Identify and analyze the gaps between the current and the target profile. Leverage this information to develop and action plan to address those gaps. This includes risk register, risk detail report, plan of action, milestones, etc.
Implement and Monitor the Plan:
Implement the action plan and regularly monitor it to ensure it is on track and proactively address any deviations or issues.
How MetricStream Helps with NIST Compliance?
MetricStream helps companies comply with many regulations and security standards, including those from the National Institute of Standards and Technology (NIST).
With MetricStream IT and Cyber Compliance Management, organizations can employ a 'test once, comply with many' approach to harmonize mappings. Companies can quickly get their IT compliance program up and running by uploading pre-packaged information such as the NIST Cybersecurity Framework. The software solution streamlines the various processes, including conducting risk identification, mapping it to critical assets, processes, business functions, controls, etc., conducting self-assessments and surveys, identifying and remediating issues, and more.
Furthermore, continuous control monitoring capabilities enable organizations to continuously test and monitor their organizational controls on AWS cloud infrastructure. These results are then integrated with the results of testing performed for the entire control environment.
To learn more about how MetricStream can help with IT compliance management, request a personalized product demo.
Given today’s highly precarious digital operating environment, regulatory authorities and standard-setting bodies around the world regularly issue guidance, laws, regulations, frameworks, and standards to ensure organizations have the necessary measures in place to prevent cyber attacks.
NIST released the Cybersecurity Framework (CSF) with the objective of establishing a standard for organizations to effectively understand, manage, and reduce cybersecurity risk. Developed in collaboration with the private sector, NIST CSF provides a series of flexible guidelines that organizations can tailor to suit their unique cybersecurity needs. Since its release, the framework has been downloaded over two million times across 185+ countries and translated into at least nine languages.
- The NIST Cybersecurity Framework (CSF) is widely recognized as a best practice for managing cybersecurity risk. It has no certification or audit scheme like other compliance frameworks.
- The CSF provides guidelines to organizations to improve their cybersecurity posture and reduce the risk of cyberattacks. These guidelines are flexible, and organizations can tailor them to meet their unique needs.
- The version 2.0 of the framework classifies Cybersecurity Framework Functions into five categories: Govern, Identify, Protect, Detect, Respond, and Recover.
- To get started with the framework, it is essential for organizations to identify organizational assets, cyber risks, and cybersecurity risk management processes; classify the processes into the six functions of the CSF, conduct risk assessments, create current and target profiles and perform gap analysis, develop action plan to address gaps, and implement and monitor the plan.
National Institute of Standards and Technology (NIST) is a non-regulatory agency of the US Department of Commerce that works to improve our economic security and quality of life by advancing measurement science, standards, and technology. The agency’s Cybersecurity and Privacy Program has published an extensive collection of standards, frameworks, guidelines, and research related to the security and privacy of information and information systems. This includes FIPS, SP 800 series, NIST CSF, and more.
The NIST Cybersecurity Framework (CSF) is a set of guidelines and best practices designed to help businesses manage and reduce cybersecurity risks.It provides a structured approach to identify ,protect , detect , respond to , and recover from cyber threats.
The NIST Cybersecurity Framework (NIST CSF) is voluntary framework that guides critical infrastructure organizations to manage and reduce cybersecurity risks. It comprises standards, guidelines, and best practices for organizations to develop, implement, and improve cybersecurity programs.
The framework was first published in 2014 and then updated in 2018. In August 2023, the agency announced some of the biggest reforms to the framework with the draft CSF 2.0 in its effort to ensure the framework is aligned to the evolving cybersecurity landscape. To learn what’s new in the revised version, read our blog, Demystifying NIST CSF 2.0: What's New and Why it Matters.
In February 2024, NIST released the CSF 2.0, along with supplementary resources, which can be leveraged by organizations to understand, assess, prioritize, and communicate cybersecurity risks.
NIST CSF is designed for universal application across industries and organizations, regardless of size. It offers a flexible framework for entities aiming to improve cybersecurity practices or align with compliance requirements.
The NIST Cybersecurity Framework (CSF) is flexible and adaptable to organizations of all sizes and across industries, including:
- Critical infrastructure sectors
- Small and medium-sized businesses
- Government agencies
- Non-profit organizations
- International organizations
The NIST Cybersecurity Framework (CSF) comprises three key components: the Core, which outlines essential cybersecurity activities and outcomes; the Organizational Profile, which describes the organization's current or target cybersecurity state; and Tiers, which measure the maturity and effectiveness of the organization's cybersecurity risk management practices.
As per the version 2.0, NIST CSF consists of three main components:
CSF Core:
This provides a high-level view of outcomes that can help organizations effectively manage cybersecurity risk. It includes a set of cybersecurity outcomes that are organized on the basis of six core functions:
- Govern: The Govern function involves establishing, communicating, and monitoring the cybersecurity risk management strategy, expectations, and policy. These activities are essential for integrating an organizations cybersecurity program with the overarching enterprise risk management (ERM) strategy.
- Identify: The Identify function requires understanding the cybersecurity risks faced by an organization, its assets that it wants to protect, suppliers, etc., enabling effective prioritization of its cybersecurity risk management efforts. It also includes identifying potential areas of improvement for an organization’s cybersecurity risk management policies, plans, processes, procedures, and practices.
- Protect: The Protect function includes the outcomes that help an organization safeguard its assets and prevent or mitigate cyber incidents. It includes outcomes including identity management, authentication, access control, data and platform security, resilience of technology infrastructure, and training and awareness.
- Detect: The Detect function supports the ability to discover and analyze cyber attacks, compromises, and potential adverse events in a timely manner. The outcomes of this function enable effective incident response and recovery activities.
- Respond: The Respond functions includes actions that can help contain the impact of detected cybersecurity incidents. The outcomes in this function include incident management, analysis, mitigation, reporting, and communication.
- Recover: The Recover function supports the ability to restore assets and operations affected by cybersecurity incidents in a timely manner.
CSF Organizational Profile:
This basically describes an organization’s current and and/or target cybersecurity posture based on its CSF Core’s outcomes. This component helps an organization understand, adapt, evaluate, prioritize, and communicate the Core’s outcomes in line with its objectives, threat landscape, stakeholder expectations, and requirements.
CSF Tiers:
Tiers are applied to the Organizational Profiles and enable organizations to gauge their cybersecurity risk governance and management practices. The framework outlines four tiers – Partial (Tier 1), Risk Informed (Tier 2), Repeatable (Tier 3), and Adaptive (Tier 4), with every tier building on the previous one and indicating an organization’s advancement from informal, ad hoc responses to agile, risk-informed, and continuously improving approaches.
Implementing the NIST Cybersecurity Framework requires identifying organizational assets, processes, and operations; cyber risks, threats, and vulnerabilities; control measures in place; and more. Importantly, organizations need to categorize cybersecurity risk management activities under the six core functions and monitor them regularly to proactively identify and address any issues.
Here are some of the key steps that can help organizations get started with the framework:

Define the Scope:
Define the scope of the project in line with strategic business goals and objectives. This includes determining risk appetite and tolerance, identifying and documenting organizational assets, business processes, and cybersecurity risks; current cybersecurity risk management processes, including key controls; business continuity, incident response, and disaster recovery plans; relevant regulations, and more
Classify the Processes:
Categorize the identified cybersecurity risk management processes, plans, and measures into the six functions as defined in the framework.
Create Current Profile:
Based on the categories and subcategories of the framework, create the current profile of how the organization views and manages cybersecurity risk.
Conduct Risk Assessments:
Assess the cyber risks faced by the organization to determine their likelihood and impact.
Create Target Profile:
Determine the target cybersecurity posture that the organization wants to achieve.
Determine and Analyze the Gaps:
Identify and analyze the gaps between the current and the target profile. Leverage this information to develop and action plan to address those gaps. This includes risk register, risk detail report, plan of action, milestones, etc.
Implement and Monitor the Plan:
Implement the action plan and regularly monitor it to ensure it is on track and proactively address any deviations or issues.
MetricStream helps companies comply with many regulations and security standards, including those from the National Institute of Standards and Technology (NIST).
With MetricStream IT and Cyber Compliance Management, organizations can employ a 'test once, comply with many' approach to harmonize mappings. Companies can quickly get their IT compliance program up and running by uploading pre-packaged information such as the NIST Cybersecurity Framework. The software solution streamlines the various processes, including conducting risk identification, mapping it to critical assets, processes, business functions, controls, etc., conducting self-assessments and surveys, identifying and remediating issues, and more.
Furthermore, continuous control monitoring capabilities enable organizations to continuously test and monitor their organizational controls on AWS cloud infrastructure. These results are then integrated with the results of testing performed for the entire control environment.
To learn more about how MetricStream can help with IT compliance management, request a personalized product demo.
Frequently Asked Questions
What is the NIST Cybersecurity Framework?
The NIST Cybersecurity Framework is a set of guidelines and best practices designed to help organizations identify, protect, detect, respond to, and recover from cybersecurity threats. It provides a flexible, risk-based approach applicable to organizations of all sizes and industries.
What are the 5 steps of the NIST Cybersecurity Framework?
The 5 steps align with its core functions: Identify, Protect, Detect, Respond, and Recover. These steps guide organizations in assessing their cybersecurity posture, mitigating threats, detecting vulnerabilities, managing incidents, and ensuring business continuity after cyber events.
What is the NIST Cybersecurity Framework?
The NIST Cybersecurity Framework is a set of guidelines and best practices designed to help organizations identify, protect, detect, respond to, and recover from cybersecurity threats. It provides a flexible, risk-based approach applicable to organizations of all sizes and industries.
What are the 5 steps of the NIST Cybersecurity Framework?
The 5 steps align with its core functions: Identify, Protect, Detect, Respond, and Recover. These steps guide organizations in assessing their cybersecurity posture, mitigating threats, detecting vulnerabilities, managing incidents, and ensuring business continuity after cyber events.








