MetricStream IT and Cyber Risk Management software empowers organizations to adopt a focused, business-driven approach to identifying, managing and mitigating IT and cybersecurity risks. It enables users to conduct IT risk assessments, implement controls, and take necessary mitigation actions. It enables users to conduct IT risk assessments, implement controls, and take necessary mitigation actions. Advanced cyber risk quantification capabilities help quantify cyber risks in monetary value. Sophisticated analytics and reports transform raw risk data into actionable IT risk intelligence, providing clear visibility into the top cyber risks affecting the enterprise.
Measure Your Program Outcomes
Source: Based on MetricStream customer responses and GRC Journey Business Value Calculator
-
 66 %
66 %reduction in the time taken to complete risk assessment
-
 37 %
37 %cost savings in risk assessment and related processes
-
 30 %
30 %decrease in the number of resources needed for scaling up the level of vulnerability management
Simplify IT Risk Identification, Assessment, Analysis, and Mitigation
MetricStream IT and Cyber Risk Management software empowers organizations to adopt a focused, business-driven approach to managing and mitigating IT and cyber risks. Built on the MetricStream Platform, it enables users to conduct IT risk assessments, implement controls, and take necessary mitigation actions. Advanced cyber risk quantification capabilities help quantify cyber risks in monetary value. Sophisticated analytics and reports transform raw risk data into actionable IT risk intelligence, providing clear visibility into the top cyber risks affecting the enterprise.
Read More product details

How Our IT and Cyber Risk Management Software Helps You
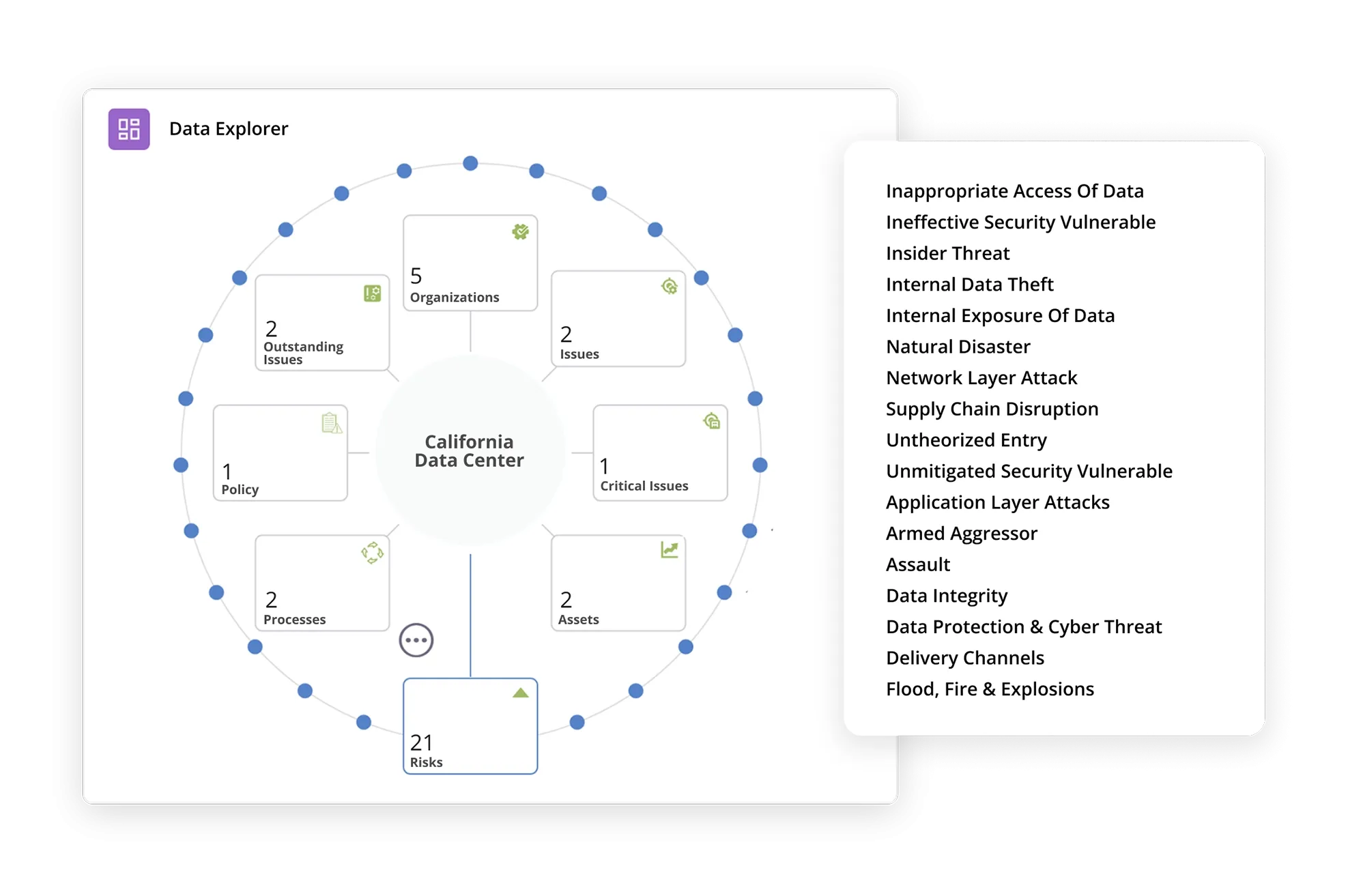

Centralized Repository for Assets, Processes, Threats, and Vulnerabilities
Define and maintain business entities such as IT risks, assets, threats, vulnerabilities, processes, and controls in a central repository on the MetricStream Platform. Map IT assets to threats and vulnerabilities along with associated details such as description, category, hierarchy, ownership, visibility, and validity.
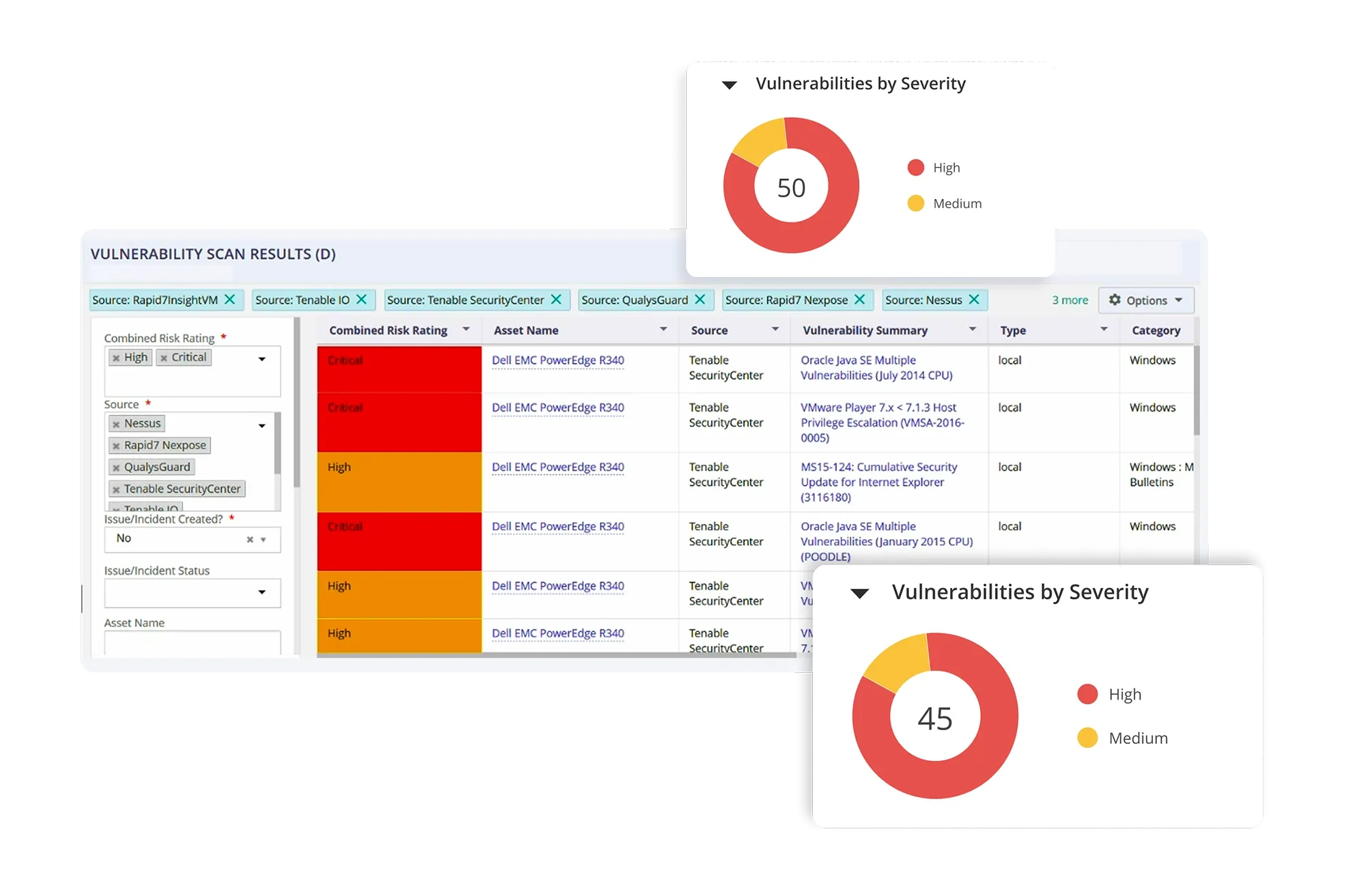
Streamlined Threat and Vulnerability Management
Monitor the threat landscape, zero-day advisories, and threat bulletins from leading industry sources. Import data from multiple vulnerability scanners and generate combined risk rating for each asset, while orchestrating the remediation process workflow.



Advanced IT Risk and Control Assessments
Assess and manage IT risks and controls in an integrated manner using industry standard frameworks such as ISO 27001 and NIST. Conduct advanced assessments by configuring risk scores and ranking them using a simple risk matrix. Roll up the scores to an assessed entity or organization.
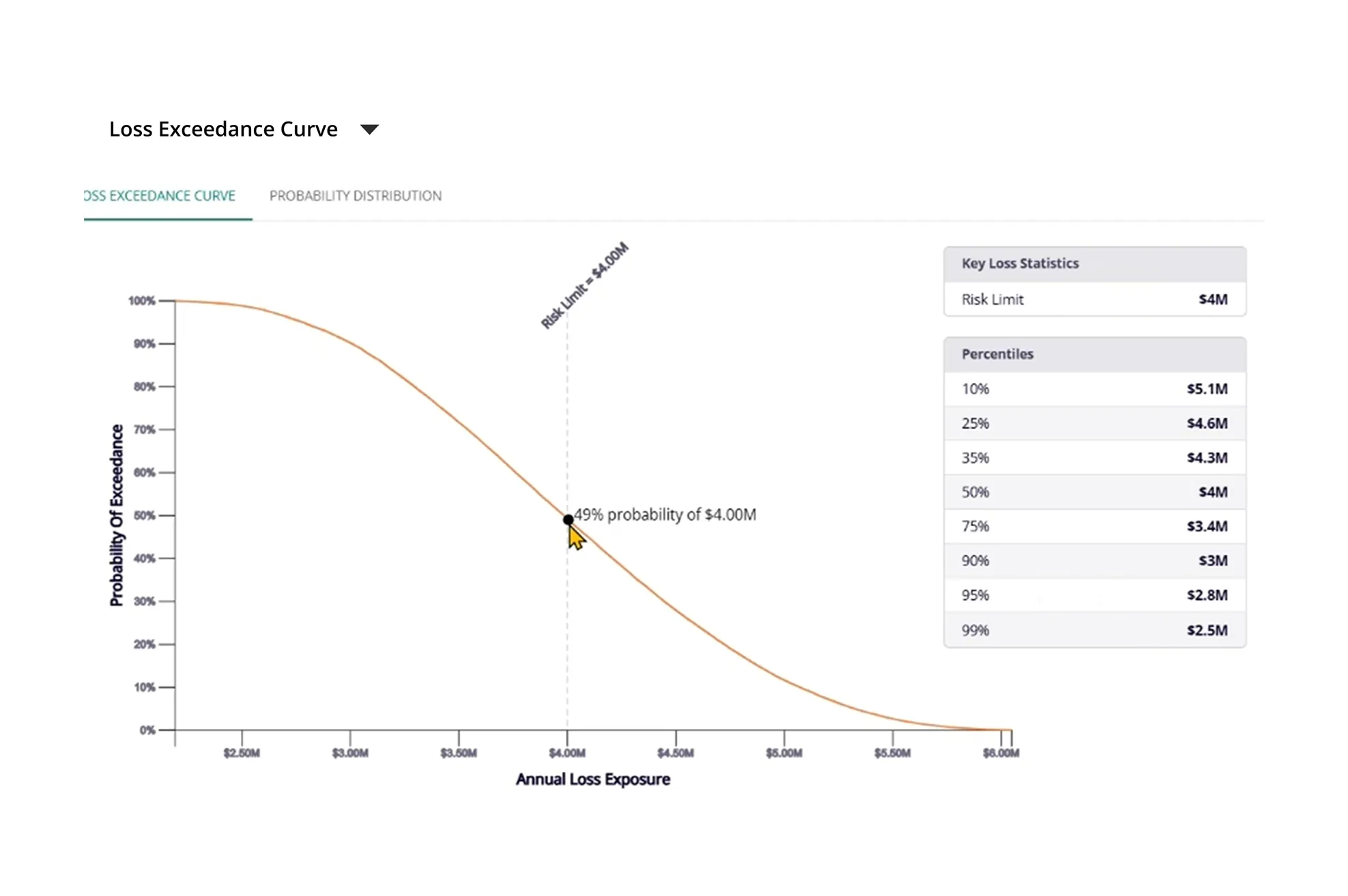
Cyber Risk Quantification and Simulation
Assess your cyber risk exposure in dollar values, using the product’s Cyber Risk Quantification capabilities. With support from the FAIR model, provide monetary impact of cyber risks like data breaches, identity theft, infrastructure downtime, etc. Create simulation techniques to transform range-based estimates into more accurate values. Enable executives to prioritize cyber investments better, driving alignment between cyber programs and business goals.

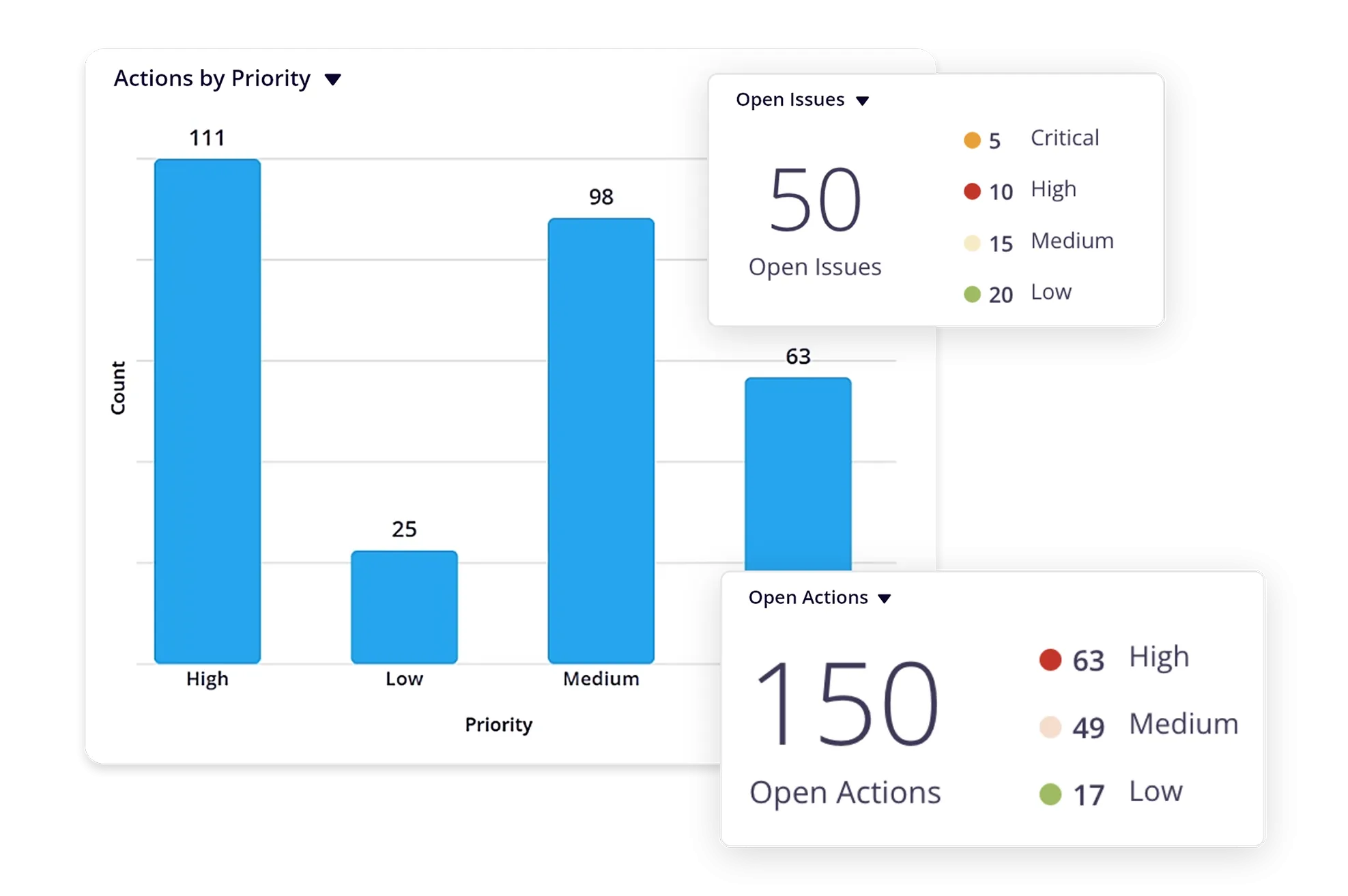

AI-Powered Intelligent Issue Management
Identify and document issues from IT risk assessments. Initiate a closed-loop process of investigation, root cause analysis, and remediation. Define rules to auto-detect vulnerability patterns among assets and to auto-trigger remediation of issues or incidents. Leverage AI/ML to quickly identify issues based on relation and recommend issue classification.
Comprehensive Visibility into Cyber Risks with Intuitive Dashboards and Reports
Built-in dashboards, user-configurable risk reports, heat maps, and role-based views aggregate relevant risk, threat, vulnerability, and control data for comprehensive visibility into overall security posture. Gain a 360-degree view of the information through the product’s data browser.
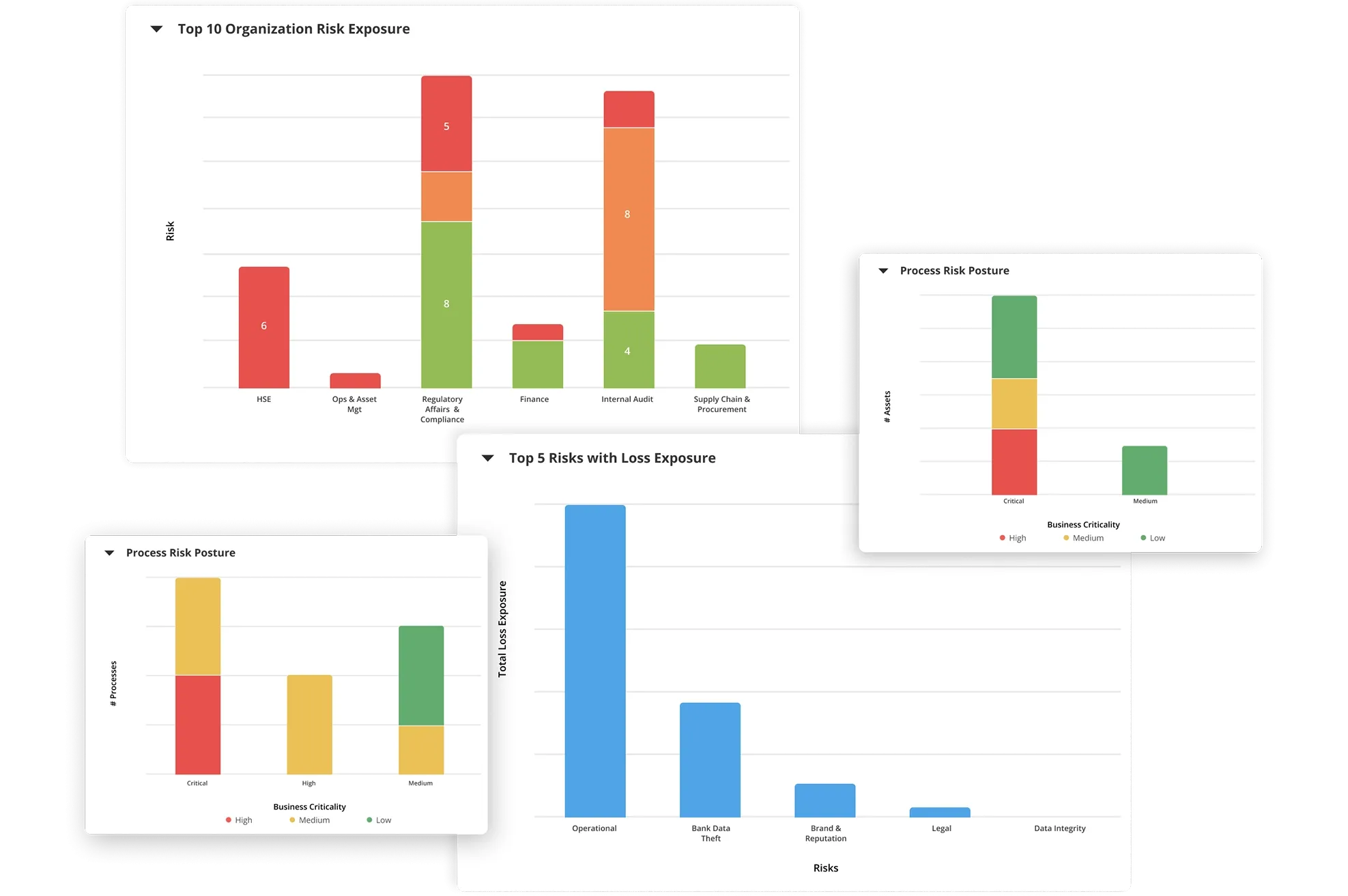
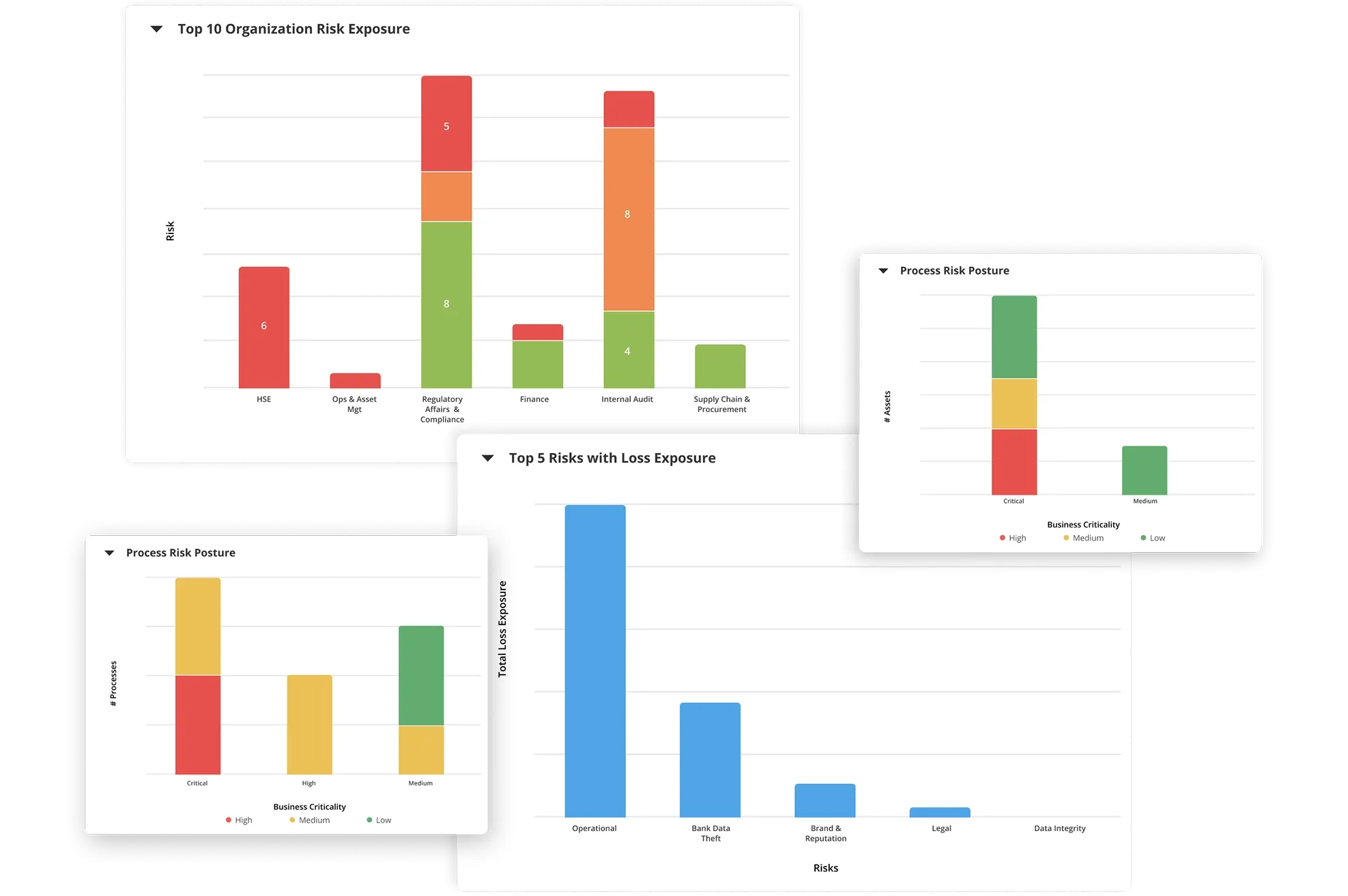
How Our IT and Cyber Risk Management Software Benefits Your Business
- Build confidence with regulators and executives through enterprise-wide cybersecurity risk management. Gain real-time threat visibility, improve efficiency by prioritizing remediation, and enhance decision-making with accurate insights from the first and second lines of defense.

Frequently Asked Questions
IT and cyber risk management software is a purpose-built solution that helps organizations identify, assess, mitigate, and monitor the risks associated with their information technology and digital infrastructure. As businesses become more tech-driven and interconnected, the exposure to threats, ranging from data breaches and ransomware to third-party vulnerabilities, has grown significantly. This software centralizes all the risk data, automates assessments, and maps threats to controls, policies, and frameworks. It empowers security and risk teams to align cyber risk with business priorities, turning digital uncertainty into informed and actionable insight.
This software covers a wide spectrum of risks that impact IT systems and digital assets. These include internal risks like system failures, misconfigurations, or user errors; external threats such as malware, phishing, and DDoS attacks; and emerging risks tied to third parties, cloud services, and regulatory gaps. It also helps address compliance-related risks tied to data privacy laws like GDPR or industry-specific regulations like HIPAA or PCI-DSS. By providing a structured view of both technical and strategic risks, the software ensures that companies can prioritize what matters most and respond to them with speed and clarity.
While cybersecurity and IT risk teams are the primary users, the software is equally valuable to CISOs, risk officers, compliance professionals, and even executive leadership. Whether it’s managing vendor risk, preparing for audits, or informing board-level decisions, this software provides the insights and coordination needed across departments. For industries that rely heavily on digital systems or operate in highly regulated environments, it’s a non-negotiable part of staying resilient. And because cyber risks touch nearly every aspect of the business now, having a unified, real-time view of those risks empowers everyone, from security analysts to boardroom members, to make smarter and faster decisions.
The tool supports IT risk documentation, control definition and management, multi-dimensional risk assessments, vulnerability consolidation and prioritization, issue identification, and implementation of recommendations and remediation plans, along with reporting and analytics.
A built-in integration engine imports and consolidates threat and vulnerability information from various sources into the MetricStream Platform. This centralized repository helps map threat and vulnerability data to assets and other business entities, enabling you to clearly visualize your information security program library and security posture, providing a unified view of the assets, asset classes, areas of compliance, and their relationships.
Using the product, you can define the scope and schedule for each assessment based on your unique requirements or industry standard frameworks such as ISO 27001, NIST CSF, CSA, and more. You can identify, quantify, monitor, and manage IT risks in an integrated manner. The product enables you to bring together all IT risk assessment related data, including a reusable library of risks and their corresponding controls, as well as results from individual assessments, key risk indicators, issues, and remediation plans. Streamline the risk assessment process through the product’s workflow capabilities and prioritize risk response strategies with the help of graphical risk heat maps.
MetricStream provides a flexible framework that enables you to measure, manage, and report cyber risk in monetary value. This Cyber Risk Quantification framework enables customers to build models to quantify their cyber risks. The framework supports FAIR, in addition to other methodologies like ISO 27005, NIST SP 800-53, CMU OCTAVE, and COBIT 5. With FAIR, asset-based risks can be quantified per their threat and vulnerability exposure, and the final dollar value at risk can be calculated.
You can explore MetricStream Cyber GRC products that enable organizations to implement a robust cybersecurity risk management program and framework based on established security standards and industry best practices. To request a demo, click here cyber-grccyber-grc.
Also, you can visit our Learn section to dive deeper into the GRC universe and the Insight section to explore our customer stories, webinars, thought leadership, and more.