Integrated Risk Management is the Mantra to Manage Interconnected Risks
- Risk Management
- 26 May 21
Introduction
In today's business world, silos are coming crashing down. The business landscape has been redefined as a result of digitalization and the evolution of the internet, mobile computing, and data sciences have led to a greater interconnectedness of operating markets across geopolitical borders.
The unprecedented after-effects of COVID-19 also made us realize that the world we live in today has a high degree of interdependency. For instance, this slow shift toward working remotely on a permanent basis could result in some long-term impacts on different industry sectors simply because everything is connected. A disruption anywhere on the transaction chain has the potential to create a domino effect and send ripples down the market. If businesses fail to understand and analyze the interconnections, they can make myopic decisions that could cause organizations to fail in developing and executing effective recovery strategies.
Despite the ongoing effort to adopt new technologies and tools to implement a pervasive approach to risk management, business leaders and risk teams are still unable to fully understand the interconnectedness of risks. In our recent webinar, risk professionals and leaders discussed why that happens and how businesses can take a holistic and integrated approach to make risk management processes more efficient and effective.
What impedes businesses from being able to understand and analyze interrelated risks?
- Even if risk management is perceived as a critical function, some executives push back on risk management efforts because they simply don’t have enough information to put the risks into proper perspective. They may understand that a risk exists but might not have a detailed understanding of what it could mean or its potential impact on the organization’s long-term success. Therefore, a lack of a strong organizational risk identification and analysis program can lead to poor risk management practices within business units.
- Lack of top-down (business level) and bottom-up (process level) risk assessments: Organizations often lack a bi-directional risk identification and assessment strategy. One where the senior management identifies the strategic priorities and risks while the bottom identifies related operational breakdowns and patterns to inform the top. This type of approach allows both the business level and process level functions to make adjustments as needed within their operational plans and strategies.
- Risk management strategies are reactive and not proactive: Risk management is often treated as a compliance problem that can be solved by drafting a set of rules and making sure that all employees follow them. Instead of tying risk management with strategic planning to develop appropriate mitigation strategies, businesses view risk management as more of a check the box, rather than as a proactive decision support to identify gaps and blind spots.
- Lack of framework for analysis and aggregation of risk themes: Data alone doesn’t guarantee that a business can make effective decisions about risk. This is, in fact, a major challenge for organizations—while risk data is available, they lack the expertise to mine valuable insights and understand the interconnectedness of risks. Organizations need to break down data for granular insights that the board can understand and use. Reports based on risk data should be accurate, clear, and complete. They should contain the correct content and be presented to the appropriate decision-makers in a time that allows for an appropriate response. High-quality risk management reports rely on the existence of strong risk data aggregation capabilities, and sound infrastructure and governance ensure the information flow from one to the other.
Even today, businesses implement control without understanding the implications of how it impacts different business areas. Implementing controls within a siloed system can lead to overabundance, overlap, and duplicated controls which are unnecessarily expensive, time-consuming, and eventually reduce efficiency. Therefore, it is absolutely critical to have an integrated approach to risk management where you’re not spending 80% of your time in data collection and only 20% in analysis.
Risk management needs to evolve and help businesses obtain a deeper understanding of all aspects of the risks they face as well as the intricate spider web of interconnections they create because these links among risks can amplify the overall impact, indirectly or indirectly.
Checklist for an Effective Risk Management Program
- Establish a formal risk identification and assessment program for emerging risk identification based on business environmental changes.
- Define and implement risk and performance measurements based on objectives.
- Facilitate and foster increased data sharing and communication between business divisions.
- Define and implement an enterprise risk taxonomy with a common risk language across the organization.
- Derive a greater insight into risk interrelations through cause-impact understanding.
- Implement a tool for risk aggregation to identify themes, patterns, and hotspots across the organization.
- Improve risk management automation to avoid repetitive data-gathering tasks using data and analytics-based risk assessment.
- Enable continuous monitoring to preemptively notify teams of imminent risk events.
- The idea behind Integrated Risk Management is not to discard everything that we do today around identifying, assessing, and managing risks, but to do so in a manner that helps the business understand the relationship and connectivity between different risk areas so that they can be identified and managed proactively.
And, in order for IRM to be effective, people, processes, technology, and perhaps even data need to come together and work as part of a common ecosystem with a common purpose and goal in mind.
However, risk identification and assessment programs by themselves do not serve the full purpose without having quantifiable measures put in place to support risk identification. This requires some carefully thought-out measurement components to be designed and implemented that would provide useful insight on the risk.
While many of us would like to believe that enabling technology for IRM is primarily about implementing an enterprise GRC tool, it requires some broader thinking. IRM is an extension of your GRC program where risk management practice is seamlessly embedded into compliance, cybersecurity, vendor risk management, and business continuity planning.
Businesses need to understand and break down the complex interrelationships. And that means risk identification needs to happen, where risk happens.
Our MetricStream Platform can help you cut across organizational silos by standardizing risk and control taxonomies and enabling stakeholders to effectively coordinate and unify risk management activities across all business functions. Organizations can use our product to align their assurance programs and gain comprehensive visibility into both risk exposure and relationships. Reach out to us to know how to achieve forward-looking risk visibility with predictive risk metrics and indicators in your Risk Management program today!
Improving Third-Party Cyber Risk Management with MetricStream and BitSight
- IT Risk & Cyber Risk
- 12 May 21
Introduction
With the growing reliance of organizations on an interconnected network of third parties, they are becoming increasingly vulnerable to a plethora of risks. A 2020 Ponemon survey found that a typical enterprise has an average of 5,800 third parties, and the number is expected to grow by 15 percent this year. As the third-party network of an organization expands, so does the number of potential points of failure.
Companies often have to share sensitive information with third-party vendors for business-critical goods and services. And, if the latter suffers any data breach, it could have a deleterious effect on the organization. Recent incidents, such as security breaches at Microsoft and Accellion, and SolarWinds hack, are unfortunate reminders of how third-party risks can make multiple organizations susceptible to illicit actors and impede their operations. Moreover, in this digital era and hyper-connected business environment, a security lapse at even a small-sized enterprise can have far reaching and disastrous consequences.
As such, implementing an effective third-party risk management (TPRM) program has become critical for today’s extended enterprise. The objective is to identify and mitigate the business, operational and cyber risks associated with the third parties, fourth, and subsequent parties, including security breaches, supply chain disruptions, unethical actions, poor performance, financial impact, and more.
TPRM Key Considerations
There are certain must-haves when it comes to a robust TPRM framework:
- Comprehensive visibility into supply chain hierarchy and mapping of the third parties to products, services, business units, fourth and subsequent parties
- Segregating third parties into critical and non-critical categories depending on their access to critical organizational assets and impact on margins and profitability
- Well-defined and comprehensive vendor contracts that details roles and responsibilities of third parties even after the contract terminates
- Performing third-party due diligence and risk assessment to determine if they are financially stable and ensure that they are operating in secure and compliant manner
- Continuous monitoring of third-party risks to determine changes in risk levels, identify new risks, and ascertain how secure third parties are
- Extend TPRM framework to fourth, fifth and subsequent parties
Implementing a centralized and technology based TPRM solution, which streamlines and digitizes these processes, has become vital for organizations to mitigate third-party risks in an efficient manner. MetricStream Third-Party Risk Management provides organizations with an integrated, real-time view of the extended enterprise and helps automate various associated processes including collating information, onboarding, continuous monitoring, risk, compliance and control assessments, and risk mitigation.
The MetricStream Arno release enhances BitSight integration, enabling proactive identification and mitigation of cybersecurity risks in the extended enterprise. When setting up the due diligence task, organizations can now define one of the stages as information security risk assessment using BitSight content. The task to review the content will be triggered as part of the due diligence workflow – the information security score and rating from BitSight can be reviewed and risk mitigation steps can be documented.
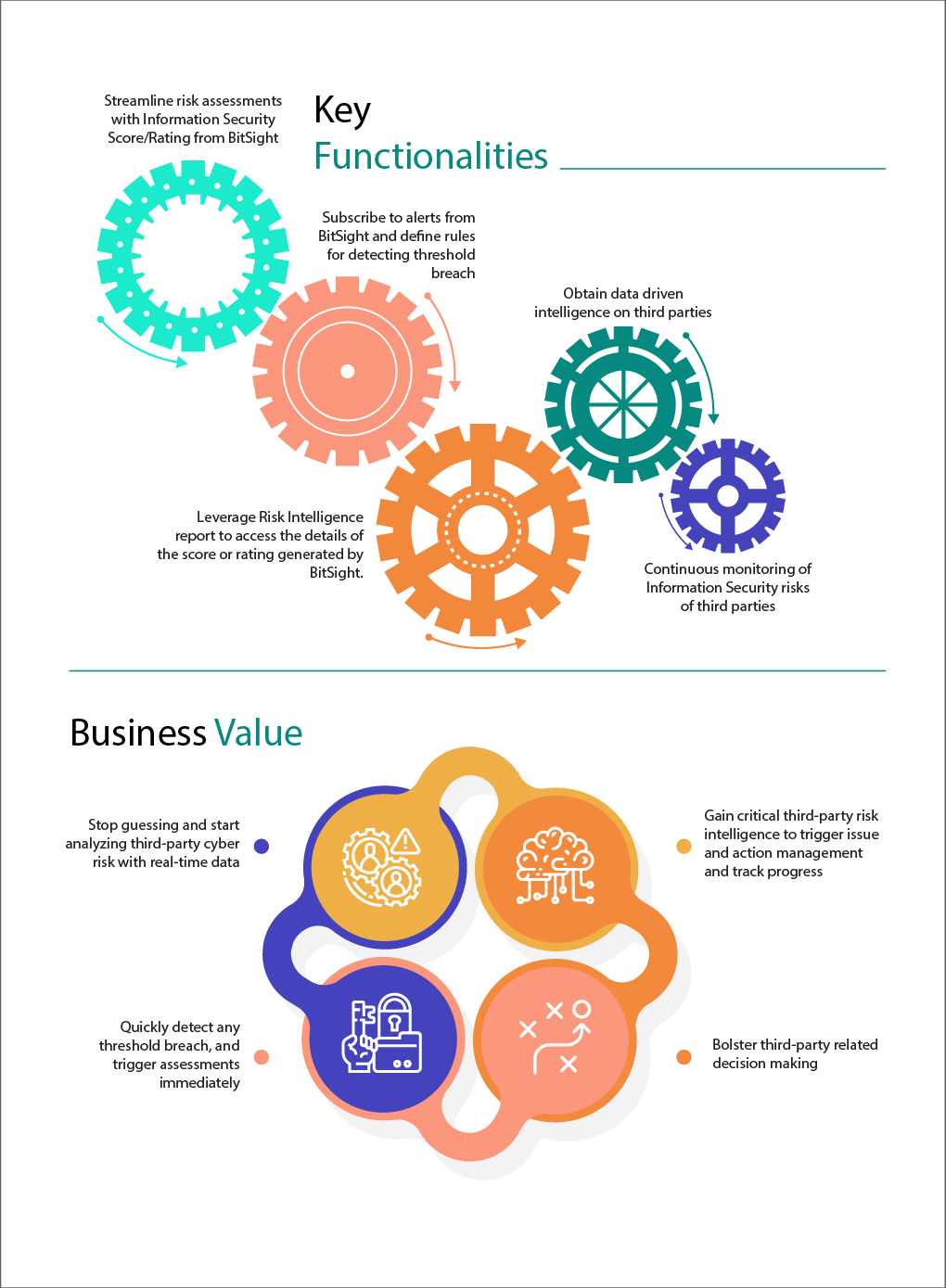
Furthermore, organizations can also leverage BitSight infosec ratings to continuously monitor third-party risks. They can also subscribe to regular or periodic alerts from BitSight for chosen third parties and define rules to automate review task assignment—when a change occurs in the BitSight score, it will automatically send notifications so that the user can review the changes and take further action.
To know more about BitSight content integration, register for the live webinar here.
Thrive on Risk and Build Resilience with an Agile and Integrated Risk Management Program
- Risk Management
- 04 May 21

Introduction
As the uncertain business environment continues to linger in the wake of the COVID-19 pandemic, organizations must boost their preparedness for the unknown unknowns to ensure uninterrupted business operations.
Work has moved home due to the pandemic but has not slowed down. To understand the state of risk management and how risk professionals are approaching this critical business function in the new normal, MetricStream conducted a survey of chief risk officers (CROs) and risk managers spanning multiple geographies and industries. The survey results have been compiled in The State of Risk Management Survey Report 2021. Here are some of the key takeaways from the survey:
- 48.91% of respondents identified cybersecurity as the top risk faced by organizations.
- 58.70% of respondents said that aligning risk priorities with business strategy is a key challenge faced by organizations when it comes to enterprise and operational risk management.
- 61.96% of respondents said that determining the effectiveness of cybersecurity risk management is a top priority for risk professionals in the post-pandemic world.
- All the companies that have deployed an integrated risk management (IRM) solution use it primarily to create a centralized risk repository. Other uses for which companies leverage IRM solution include aggregating risks based on various parameters and dimensions, automating workflows for risk control self-assessment (RCSA), providing risk insights, and tracking and monitoring key metrics.
- Organizations are willing to dedicate resources to upskill risk managers on emerging risks and cutting-edge technologies.
Agile, Integrated, Responsive…
Risk management is no longer seen as an annual or half-yearly “tick-box” exercise. The crisis has particularly highlighted the importance of competent risk managers and an effective enterprise risk management (ERM) strategy for business continuity and resilience.
To keep up with the evolving operational environment and risk landscape, it’s imperative that the top management and leadership are aware of the organization’s risk profile, tolerance, and appetite to make informed business decisions. A data-driven, technology-based IRM program can better equip risk teams to provide risk intelligence to the senior management in real-time, thereby improving an organization’s agility and responsiveness.
The survey, in fact, affirmed that IRM is key for ensuring operational resilience as more than half of the organizations (52.63%) that had already deployed an IRM solution did not alter their risk programs, approaches, or activities due to the pandemic. That said, a significant number of organizations still depend on basic office productivity software for risk management activities, which hampers their risk identification, reporting, assessment, and mitigation capabilities.
In these unprecedented times, companies can position themselves as trailblazers and gain a competitive edge by their ability to thrive on risk. It is important to note here that implementing a technology solution alone to meet risk management needs is not enough. For an IRM program to be successful, organizations must transition to a matured framework—one that strikes the right balance between people, processes, and technology. This approach is not a silver bullet but can greatly enhance an organization’s resilience to risk events.
“Beyond financial risks and cyber risks, we now must pay very critical attention to HR and operational resilience of our organizations as well. Unfortunately, this is going to be part of the new normal for years to come as we have to be ready to deal with the pandemics—the current one and perhaps other incarnations of these kinds of pandemics into the future. We have to learn how to deal with crisis and emergency events and other wartime scenarios that are the ‘Unknown Unknowns’ that the GRC industry must learn to tackle,” said Gunjan Sinha, Executive Chairman, MetricStream.
MetricStream offers a suite of products and solutions that enable organizations to enhance and streamline risk management activities and processes. The MetricStream Integrated Risk Solution empowers organizations to manage both existing and emerging risks across geopolitical, digital, strategic, third-party, cybersecurity, and compliance areas. In addition, some key enhancements have also been made to the MetricStream Platform with the Arno release to enable better business configurability, improve mobile capabilities and enhance user experience.
To download the complete report, click here. To request a demo, click here.
The Art and Science of Risk Aggregation: Harvesting Different Metrics Across Multiple Dimensions
- Risk Management
- 20 April 21

Introduction
What is Risk Aggregation
Risk aggregation is a process used by organizations of all sizes to get a complete view of the total risk exposure across various processes, business lines, and risk types using multiple risk data aggregation methods. Risk aggregation is vital for informed decision-making.
The credit and financial crises have proved that looking at risk management through the rearview mirror is dangerous. Since then, organizations – especially banks and financial services institutions – have recommended adopting a forward-looking approach to risk management. Organizations of all sizes now want to assess and aggregate risks across various processes, business lines, and risk types using multiple methods.
The process of identifying the impact of various risks on a business requires the ability to aggregate risks both vertically and horizontally. A robust aggregation mechanism enables risk officers not only to understand the total risk exposure, but to also make risk-aware decisions and define risk treatment plans that are in line with their organization’s risk appetite definitions.
Why Should You Aggregate Risks?
Managing risks across a large enterprise can be a challenge. The process of identifying the impact of multiple risks on an organization requires the ability to aggregate risks at multiple levels. The basic goal of risk aggregation is to collect several risks in order to arrive at a total risk exposure for all or a part of an organization. Risk aggregation allows grouping of similar risks from different perspectives to provide a complete picture of risk across the enterprise.
Basel Committee on Banking Supervision (BCBS) points out the need for risk aggregation in banking and financial services sectors as below:
“Naturally, the organization of risk management functions varies across firms. In some firms, risk management is a highly centralized function where the dedicated risk management function exercises substantial authority. In other firms, particularly in the insurance sector, local business units with a limited risk profile retain substantially greater autonomy over significant risk management decisions. Moreover, even in some firms with a bias toward centralized risk-management decision-making, the key decisions are made by a senior management committee, rather than by the risk management function itself. The organizational infrastructure of risk management decision-making varies considerably across firms, and it is difficult to conclude that any single approach is becoming dominant.”
Additionally, companies follow different organizational structures to support their nature of business. Some organizations might group risks as per organizational structure while others might group them by legal entities, geographical structure, processes, products or risk categories. Risks can be present at multiple levels within an organization. Risk owners at each level would want to easily identify their exposure as against the total exposure at enterprise level. There could be common risks between two functions or locations. Stakeholders at each level would want to view aggregated level of risk exposure for specific risks or risk types, for example, External Fraud, Attrition etc. This can be useful for monitoring changes in risk profile over time. Risk owners at various levels would want to look at top risks at their levels and take necessary actions to mitigate them. They would also want to easily identify if any risk or a group of risks are approaching risk appetite limits or have already breached those limits. To facilitate all these, organizations have to adopt risk aggregation methodologies that suits their risk management approach and business strategy.
Risk aggregation at multiple levels and also at enterprise level helps risk leaders understand the root cause of risks and take meaningful, remedial actions. Slicing and dicing of risk data by aggregating at different levels enables risk owners and organizations to make risk-based decisions and take advantage of market movements and conditions.
Key Challenges While Aggregating Risks:
Data Collection:
Collection, quality, and applicability of data are a major challenge while rating and scoring risks. In the absence of a tool, data may be residing in multiple scattered locations. Collating this data is not only time consuming, but also affects the outcome if not collated properly.
Managing different criticality threshold limits:
Risks are at different threshold limits based on their criticality. For example, a risk rated very high by a business unit may not have the same threshold limit assigned by another business unit or at an enterprise level, making it a medium or low risk. Considering this, there may be multiple thresholds e.g. financial, reputational etc. across an intersection of different hierarchies making the challenge further complicated. Hence, using the simple average method to aggregate risk may not give an accurate picture of risk exposure.
Combination of qualitative and quantitative data:
A majority of the information is qualitative making it difficult to come to an exact risk score.
MetricStream’s Risk Aggregation Functionality To Solve These Challenges
MetricStream provides capabilities to manage an organization’s entire risk management requirement from risk identification to risk assessment, control evaluation, risk treatment, and risk and control continuous evaluation and reporting.
Given below are some of the core capabilities for risk assessment and aggregation:
- Access advanced tools for planning, scheduling, and performing risk assessments at all levels to collect all relevant information about each risk, and once the assessments are complete, route the results for review and approval.
- Perform assessments easily with a simple and intuitive user interface.
- Enable both top-down and bottom-up approaches to risk assessments.
- Easily configure rules to calculate risk scores. Define multiple parameters to collect information such as likelihood, impact, severity, velocity etc.
- Manage simple assessments by rating a risk, or advanced assessments using multiple factors and advanced risk scoring to meet variations in the risk assessment methodology across business units, regions, and products.
- Add or delete risks and controls while performing an assessment.
- Assess the overall control environment based on multiple factors.
- Define the logic for computing inherent and residual risk scores and analyze them through heat maps.
- Aggregate the scores based on averages, worst-case scenarios (maximum), or best-case scenarios (minimum).
- Aggregate risk scores using weighted average method where weights can be given to multiple dimensions including organization, objective, product, process, assessable item or risk hierarchy for improved and accurate risk visibility.
- Easily configurable workflows that supports users to take necessary actions against risks that require immediate effect or preventive actions or are minor concerns. Review and respond accordingly.
- Enable continuous monitoring with real-time update of risk scores and underlying workflows.
As risk continues to permeate through all levels of an organization, being able to gain a holistic view of risks will help build resilience and profitability. Risk aggregation could be a key pivot on which better risk-aware decisions can be made across the lines of the business, propelling organizations towards accelerated performance, thriving on risk.
Managing Risk from the Frontline in an Uncertain World
- Risk Management
- 20 April 21

Introduction
The COVID-19 pandemic has highlighted how ill-prepared and ill-equipped businesses around the world really were to tackle a crisis of such magnitude. So, while digitization and automation have emerged as the major focus areas for organizations to be able to quickly adapt to the new normal, so has an agile, integrated, and technology-driven approach to risk management. In KPMG’s COVID-19 risk assessment survey of key managerial personnel, a majority of respondents (75%) said that they feel the need for the adoption of technology-based solutions to monitor key risks and their mitigation.
The pandemic has also brought conversations on frontline engagement to the forefront. Being closely engaged in daily business activities, it is the frontline that is more likely to identify emerging risks and vulnerabilities. As such, there is a growing call among risk and compliance leaders to make the frontline more agile and entrusting them with more risk management responsibilities—moving beyond the existing risk identification and management role in day-to-day activities to control ownership and accountability.
Frontline Taking the Lead Role
Delegating more risk management responsibilities to the frontline, making them risk-aware, and empowering them with proper training and tools has become critical for organizations to efficiently navigate today’s complex business risk environment. Companies are also increasingly engaging with the frontline in the designing phase of the risk management framework itself. Factoring in the frontline’s valuable insights on end-user perspectives, latent and emerging market trends, and more will enable organizations to ensure the relevancy and effectiveness of their risk and compliance programs.
In addition to owning and managing risk management decisions on a daily basis, the frontline today is also tasked with ensuring the effectiveness of controls. Risk and Control Self-Assessment (RCSA) is an important tool that the frontline can use to assess the operational risks associated with their activities and the efficacy of controls that address those risks. This way, RCSAs empower the frontline to make confident, informed decisions.
Bolstering the capabilities and responsibilities of the frontline, in turn, enhances the risk monitoring capabilities and oversight of the second line. A collaborative and synchronized effort of the three lines, in a way that is aligned with business strategy and goals, will help improve risk visibility and forecasting capabilities and make an organization nimbler and more responsive.
Organizations can leverage MetricStream Observation Management which simplifies capturing risk intelligence from the frontlines. The product helps bring GRC to the frontline with engaging platforms, widgets, browser plugins, conversational interfaces, chatbots, and intuitive web forms.
With the MetricStream Arno Release, the product now enables frontline users to capture risk and compliance observations, which can then be triaged and categorized as case and incident, loss event, or issue. AI-powered recommendations can be leveraged for categorizing the observations thereby increasing the efficiency and effectiveness of the triage team. Once triaged, the management and monitoring of actions to address them can be automated.
The Third-Party Risk Perspective on Microsoft Hack
- Risk Management
- 19 March 21

Introduction
Earlier this month, tech titan Microsoft reported a state-sponsored cyber breach which is said to have impacted thousands of businesses around the globe.
In a blog post, the Microsoft Threat Intelligence Center (MSTIC) attributed this breach with high confidence to HAFNIUM, a group assessed to be state-sponsored and operating out of China. The group was able to exploit vulnerabilities in the on-premises Exchange Server which enabled access to email accounts and allowed installation of additional malware to facilitate long-term access to victim environments.
In this hyper-connected business environment where we depend on multiple organizations to run our business smoothly, the cyberattack surface is continuously expanding and not limited to your infrastructure only. It is imperative that organizations continuously monitor the relevancy and effectiveness of their cyber risk management programs as well as of their partners with whom they are sharing sensitive information to identify and address any vulnerable areas or loopholes. The situation is further exacerbated by the growing interconnectivity of organizations resulting from the accelerated pace of digitalization. As such, organizations are left with an extremely short window of time to react to any emerging or existing risk event.
An organization is only as strong as its weakest link. With the proliferation of an organization’s third-party network, the number of potential points of failure also grows. To successfully manage the vast network of suppliers, ensuring visibility into supply chain hierarchy and the mapping of the third parties to products, services, fourth and subsequent parties, and business units becomes critical.
The Growing Problem of Third-Party Breaches
Third Party breaches has been on the rise for quite some time. There has been more than 25 breaches because of third parties in just 3 months of 2021 including the big names like Facebook, Instagram, LinkedIn, Supply chain for Audi, BMW, Mercedes, Porsche, Saab, Volkswagen and Volvo across North America, Microsoft, Singapore Airlines, Qualys, Airbus, Air Caraïbes, ArcelorMittal, BT, PWC Russia, etc.
The most recent Microsoft hack has underscored how third-party risks can make multiple organizations susceptible to illicit actors.
In this incident, thousands of organizations worldwide using Microsoft Exchange Server—a mail and calendar server and collaboration solution—were impacted. While the Windows-maker said that it quickly deployed an update for the Hafnium exploits, it is estimated that the breach affected at least 30,000 organizations across the U.S., including small businesses, towns, cities, and local governments, and 60,000 computer systems in Germany. The full scale of the impact is expected to become clearer in the forthcoming weeks.
What makes this hack graver is the fact that organizations using the Exchange Server could not have prevented it as this was a zero-day exploit. The European Banking Authority (EBA) took its email systems offline following the incident. In a subsequent update on the matter, it said that the scope of the event was limited and that the confidentiality of the EBA systems and data has not been compromised. Meanwhile, U.S. Cybersecurity & Infrastructure Security Agency (CISA) has issued an emergency directive ordering all federal civilian departments and agencies running vulnerable Microsoft Exchange servers to either update the software or disconnect the products from their networks.
That said, organizations must not let their guard down when dealing with third-party risks. To thrive in today’s digital era, they need to implement a well-defined third-party risk management program that provides an integrated, real-time view of the extended enterprise. A robust, technology-driven program will help organizations automate the entire third-party risk management lifecycle, thereby improving visibility into the risks posed by the third and subsequent parties and accelerate responses to risk events. Also, organization should focus on having a robust business continuity program in place to help them running critical business function in case of these disasters.
MetricStream helps organizations effectively manage third-party risks with its Third-Party Risk Management product. With Continuous Third-Party Monitoring, Periodic Third-Party Due Diligence, Intuitive Dashboards and Reports, the product empowers organizations to protect their business from existing and potential threats from third parties, as well as strengthen resilience, contain costs, and optimize business performance.
To learn more about third-party risk management read MetricStream’s eBook, Boosting Third-Party Risk Management in a Time of Uncertainty, which delves into how third-party risks can expose organizations to a wider spectrum of risks if left unchecked. It also provides quick tips on how to review third-party risk management operating models and identify gaps or opportunities for improvement.
Improving Business Performance with Integrated Risk Management
- Risk Management
- 02 February 21

Introduction
Today, business leaders and risk managers are required to navigate an increasingly complex risk landscape that is evolving at a rapid pace. Economic, environmental, geopolitical, technological, and other factors and their growing interdependencies are resulting in an ever-changing and expanding risk environment, making risk management extremely challenging.
The current volatile operating environment has questioned the very validity of the longstanding siloed approach to risk management. The situation has been further exacerbated by the COVID-19 pandemic which has amplified digital dependency and interconnectivity of people, processes, and organizations, thereby multiplying the points of intersections of different risks. Furthermore, siloed risk approach results in risk data being scattered across an organization, which acts as a major impediment to an organization’s decision-making capabilities.
To succeed in these uncertain times, organizations need to adopt an integrated approach to risk management, which will help create a single source of truth of all risk-related issues and data across different business units and functions. The integrated risk management (IRM) approach will considerably enhance an organization’s risk visibility and provide a better understanding of risk relationships and their cascading effects. In addition, by enabling prompt risk identification, organizations will be better equipped to reduce risk response time and take appropriate risk mitigation and remediation action.
It is encouraging to see that organizations are gradually embracing this forward-looking approach. The OCEG 2020 GRC Maturity Survey revealed that a number of businesses around the world are starting to integrate and standardize their governance, risk, and compliance (GRC) processes and technology.
Integrated Risk Program of the Future
A future-ready integrated risk program builds upon the existing risk management infrastructure and reconfigures it to make it more agile, unified, structured, and coordinated. This approach provides C-suite executives and board of directors with real-time actionable risk insights for improved decision-making and business performance. It puts in place a comprehensive integrative layer that provides deep visibility into an organization’s risk profile and risk relationships, along with an integrated issue and action management strategy that enables risk mitigation in real-time.
With the growing labyrinth of risks, companies are increasingly looking to tap technology-driven IRM tools that can significantly streamline and simplify risk management that is tied with business objectives and goals. These solutions, which leverage artificial intelligence (AI), robotic process automation (RPA), and such advanced and innovative technologies, seamlessly integrate with the larger IT infrastructure, dramatically improving an organization’s risk identification and mitigation capabilities, risk preparedness, and overall operational resilience and efficiency.
By 2021, Gartner expects more than 50% of large organizations to use an integrated risk management solution and projects the IRM solutions market to grow to $8 billion.
MetricStream offers a range of products and solutions that aim to enhance and streamline risk management activities and processes. The MetricStream Integrated Risk Solution enables organizations to manage both current and emerging risks across geopolitical, digital, strategic, third-party, cybersecurity, and compliance areas. It cuts across organizational silos by standardizing risk and control taxonomies and enabling stakeholders to effectively coordinate and unify risk management activities across all business functions.
Conclusion
Adopting a mature, technology-driven IRM approach is increasingly being viewed as a core competency for organizations to achieve their business goals. Once implemented, organizations should proactively conduct routine assessments to ensure the program’s effectiveness. In the long run, this will help an organization to better understand its risk posture, improve its risk appetite, and make well-informed decisions.
An effective IRM program needs to be complemented with a “risk-aware” culture across an enterprise along with well-defined roles, responsibilities, and accountability for employees. Educating employees on emerging risks and upcoming trends in the market, industry, and economy will help broaden the outlook of the workforce and boost their risk identification capabilities.
For diving deeper into IRM you can read MetricStream’s eBook, The Future of Integrated Risk Management, which details the best practices for a future-ready IRM program, provides quick tips for preparing an organization to adopt IRM, and delves into the organizational challenges involved in managing unknown-unknown risks, as well as the strategic direction of the financial services industry as it prepares for these risks and their domino effect.
Lessons Learned from the FireEye Breach
- GRC
- 21 December 20

Introduction
The recent FireEye breach is perhaps the most significant cybersecurity headline of 2020, with one of the leading advanced threat detection vendors falling victim to an apparent state-sponsored attack. As new details of the breach unfold, the nexus between cybersecurity and risk management become increasingly evident, forming the basis of several lessons learned.
Third Party IT Vendors – Your Weakest Link in Security
Over the last 10 years, IT departments have gained undeniable advantages and realized significant business benefits by utilizing third-party IT solutions. Rather than building costly on-premise IT infrastructure and services, agile businesses have reliably turned to third-party vendors, such as Amazon AWS, Salesforce, Microsoft and others to effectively and efficiently host, manage and provide mission-critical business and IT services.
Following in this practice, FireEye reportedly used the third-party network performance, management and monitoring software from SolarWinds, which appears to be the crux of the breach. However, the fact that the breach potentially stemmed from SolarWinds is irrelevant. The fundamental issue here is that supply chain and third-party IT solutions present real risks to enterprise security architectures.
Lesson Learned – Implement Third-Party Risk Management Solutions
The proverbial ship has sailed when it comes to outsourcing IT services, and despite recent attacks, businesses have much to gain (e.g. cost savings, agility, flexibility, productivity, etc.) by using outsourced and cloud-based services. Knowing this, the prudent course of action is to implement a solution that reduces risk associated with third-party vendors.
One such solution is the MetricStream Third-Party Risk Management offering, which protects businesses from existing and potential third-party threats. Built on the MetricStream M7 Integrated Risk Platform, MetricStream’s Third-Party Risk Management product provides an integrated, real-time view of the extended enterprise. It strengthens resilience, contains costs and optimizes business performance by automating the end-to-end processes for information gathering, onboarding, real-time monitoring, risk, compliance and control assessments and risk mitigation.
Policy – Without Policy Security is Toothless
In the cybersecurity world, policy and policy management is often overlooked and undervalued. However, without policy, enforcement of enterprise security programs is futile and inefficient. We see this every day in society. We have laws to protect citizens, but without the police (policy enforcement), we would live in a lawless society.
Every breach is an opportunity to learn, strengthen security and become more resilient. Policy factors into this, and should be included as part of a post-breach review. In fact, most breaches are not nearly as sophisticated as the FireEye breach, but are instead the result of employees not following security policies. For example, a spear-phishing campaign often succeeds because an employee clicked on a link embedded in a suspicious external email, even though corporate policy states not to do so.
Lesson Learned – Review Policy Management to Strengthen Security
MetricStream Policy and Document Management built on the M7 Integrated Risk Platform, streamlines and simplifies the creation and communication of organizational policies, while providing a centralized policy portal to store and access the latest policies. It delivers a contextual view to policies by mapping policies to regulations, risks and controls, thereby strengthening compliance while highlighting potential risks. Policy and Document Management raises awareness throughout an organization and brings policies to everyone, including first line employees, who are often the targets of cyberattacks.
Communications – Transparency is Critical to Recovery
One observation noted from the FireEye attack is the speed and transparency of their communications. Kudos to those involved, as often a breach is solely managed by Legal and/or IT. Whenever a substantive breach occurs, businesses face damage to their brand, sales efforts, customer success and partner base.
Not only do breaches potentially trigger lawsuits, but for many corporations, a material breach can also trigger SEC Regulation FD (Fair Disclosure) consequences. Cybersecurity incidents are often listed as part of corporate governance documentation relating to Regulation FD.
For those not in Legal or Corporate Communications, Regulation FD basically states that a corporation must prevent the selective disclosure of material, non-public information that could be used in the decision-making process of buying or selling a security. Depending on the severity of a cybersecurity incident, Regulation FD may apply.
Lesson Learned – Incident Response Must be Documented
As FireEye has shown, clear, quick and transparent communications is the way to best manage brand-challenging situations. Learning from their experience and response, every organization should have a PSIRT (Product Security Incident Response Team) policy in place BEFORE a breach or serious incident occurs. Response teams are usually comprised of different members within the enterprise, including representatives from Corporate Communications, Legal, IT/Security and the C-Suite. With MetricStream Policy and Document Management, creation of a PSIRT policy and process is simple and intuitive – a must have for any organization.
In conclusion, the FireEye breach will continue to dominate headlines as more information is revealed about the attackers, their processes, tools and techniques. As well, we hope to gain insights from what has transpired to find new and better ways to strengthen security and improve resilience. Clearly, more lessons are to be learned.












