Power What’s Next in GRC with MetricStream’s Brazos Software Release
- Compliance Management
- 19 August 21

Introduction
The demands and requirements of businesses to thrive in the new normal have changed drastically. Buzz words like agility, digitization, and resilience are no longer just business aspirations but have become necessary and fundamental for the readiness of organizations to address any risk event, including high-impact, low-frequency events such as COVID-19. With the latest Brazos release, we are delivering a myriad of innovations to support organizations in their journey to achieve their business goals and power through the current unsettled operational environment.
Brazos builds upon the previous Arno release and includes key innovations in areas including regulatory compliance, cyber risk quantification, and vendor risk management. The objective is to make the processes simpler, smarter, and more streamlined.
Simplifying Regulatory Complexity
Given the complex web of regulations, along with the escalating number of regulatory change alerts that organizations are bombarded with every day, it has become imperative to simplify the compliance function to make it more efficient and systematic. On these lines, the Brazos release brings new capabilities to our regulatory compliance products, including:
- Fully packaged, real-time curated regulatory intelligence from 1,000 supervisory bodies and 2,500 collections of regulatory/legislative materials facilitating efficient management of regulation overload.
- Certification and sub-certification processes enabling the creation of accountability chains.
- Contextual intelligence on policies allowing compliance teams to easily identify the policy section related to regulations, risks, and controls.
- Artificial Intelligence (AI)-powered action plan recommendations based on semantically similar compliance issues reported in the past for quick and easy resolution.
- Multiple enhancements to the Mobile App that simplify searching policies, tracking regulatory changes, and managing compliance assessments and regulatory engagement activities.
Quantifying the Impact of Cyber Risks
Cyber risk quantification, or quantifying cyber risks in monetary terms, is critical for cybersecurity professionals today to effectively communicate the cyber risk exposure to the top management and board. By understanding the potential impact of cyber risks in dollar values, decision-makers are better positioned to prioritize IT cyber risk spending, resource allocation, and establishment of optimal controls.
Brazos brings advanced cyber risk quantification capabilities to IT and Cyber Risk Management, enabling cybersecurity teams to leverage the industry standard FAIR methodology to quantify their cyber risks in monetary value. In addition, advanced Monte Carlo simulation capabilities help upgrade the assessment teams’ guesstimates into accurate predictive values of the cyber risk exposure.
Powering Next-Gen Vendor Risk Management with AI
Managing risks associated with the extended enterprise quickly and efficiently is crucial for ensuring continued business operations. Supplier networks of organizations today are comprised of hundreds and thousands of third, fourth, and subsequent parties. A manual approach to review third- and fourth-party documentation, including reports, certificates, and evidence, to spot any discrepancies is time-taking and prone to error.
We are addressing this challenge by bringing the benefits of artificial intelligence (AI) and automation to Third-Party Management with the latest release. MetricStream’s AI engine automatically scans through the documents submitted by the third parties, validates the content, highlights any anomalies, and automatically recommends risks scores based on the number and type of anomalies found. This real-time intelligence equips risk teams to accelerate analysis and mitigation of third-party risks.
With Brazos, we are setting a new standard by implementing AI into multiple GRC products, empowering risk, compliance, security, and audit professionals to better perform their roles and responsibilities. The release also provides a simplified user experience and enhances agility for faster time to value with:
- High configurability capabilities across the MetricStream Platform.
- Enhanced frontline capabilities to anonymously report compliance cases.
- Improved mobile capabilities for regulatory compliance, IT compliance, and audit.
- Content Integration Service that leverages REST APIs to import content from external sources.
- Better collaboration and improved cross-referencing in audit workpapers within Microsoft Word.
We are constantly striving to make your GRC journey exciting, enriching, and fun. The latest software release is guided by our key tenet of helping organizations accelerate sustainable growth with risk-aware decisions. The new features and functionalities extend the capabilities of MetricStream Platform and products and will enable you to meet the evolving business needs in this digitized world.
To know more about Brazos Release features, click here.
Organizations Look to Adopt Integrated IT GRC Solutions to Ward Off Cyberattacks, Survey Finds
- IT Risk & Cyber Risk
- 29 July 21

Introduction
Cyber risk has undoubtedly moved up the priority list and taken the center stage in boardroom discussions with the rapid pace of digital transformation of organizations and amplified data-dependency and interconnectedness. The COVID-19 pandemic and the resulting remote working environment have only aggravated the challenges for security teams as the entire workforce moved home—beyond the reach of the office firewall. In these unprecedented times, ensuring robust cyber defense infrastructure to protect critical assets is of paramount importance.
We recently conducted a survey to take a pulse of the current state of IT and cyber risk management programs at organizations. Here are the key takeaways from the survey:
- Most survey respondents (45%) identified a lack of visibility on cyber risks across the enterprise as the major challenge faced by their organization.
- A majority of organizations (83%) still depend on basic office productivity software, knowledge management software, and point solutions for their cyber risk management requirements. The implementation of an integrated IT GRC solution is at a low level across industries.
- Only 28% of the respondents said that their organization's cyber risk and compliance program is fully aligned with the broader enterprise risk and compliance management programs.
- Most respondents (45%) said that they changed their plans and approaches to cyber risk and compliance management and reprioritized their activities to contend with the pandemic-driven new operational landscape, while 33% of the participants said they deployed new tools and systems to enhance their efficiency.
- 41% of the respondents said that they are going to implement specific solutions in FY 2021 to ensure compliance with regulatory requirements and standards.
- 30% of the respondents said that they are interested in implementing a centralized cyber risk and compliance solution.
It is encouraging to see that switching to digitized and centralized GRC solutions is among the top priorities of organizations this year. These solutions can help improve risk visibility and foresight, facilitate continuous monitoring of IT and cyber controls, and streamline overall cyber risk and compliance management. Innovative features, such as support for mobility, real-time reporting, advanced risk analytics, regulatory notifications, and more, further assist executive management and board in quick and efficient decision-making.
“The ultimate goal isn’t to avoid cyber risk but rather transforming it into strategic advantage—because things can and will inevitably go wrong at some point. But if organizations build their cyber resilience—the ability to not just prevent cyberattacks but also minimizing the impact of security incidents and ensuring continued business operations in the aftermath of attacks—that’s when they can truly thrive and create business value,” an excerpt from the report reads.
Cyber Risk to Dominate Risk Strategies
Our flagship event, GRC Summit, was held recently and brought together the best in the industry to share risk management strategies and best practices, and how to build better governed, more risk-aware, compliant, and resilient enterprises that thrive on risk.
Unsurprisingly, cyber risk has emerged as one of the top risks faced by organizations today, and risk leaders believe that it will continue to dominate the risk strategies going forward. To that end, security experts discussed some of the key considerations for ensuring a robust cybersecurity program:
- Aligning cyber strategy with business goals and objectives.
- Positioning CISO and security leaders at the right level so that they can better focus on their core responsibilities.
- Ensuring that CISOs and the security team provide frequent updates on the cybersecurity posture to the board so that there is no communication gap.
- Quantifying cyber risks for prioritizing risks and controls and determining how much to spend on each control.
- Increasing transparency into employee communications so that they have clarity not only on corporate policies but also how a crisis is being managed
The best-prepared organizations in the world today are those that use risk as their competitive advantage. Quantifying cyber risks in a manner that makes sense to the executive board and helps them make sound cybersecurity investment decisions is critical for organizations to thrive in today’s digital world. The Cyber Risk Quantification capability of MetricStream IT and Cyber Risk Management can make it considerably easier for organizations to quantify cyber risks in monetary terms, which can then be easily communicated to the top management and board.
To download the report, click here. To watch the summit, click here.
Making the Right Investments by Quantifying your Risks
- IT Risk & Cyber Risk
- 22 July 21

Introduction
Organizations today need to optimize their risk rather than focusing on avoiding the risk – to know which risk should be accepted to enable business success and create value.
When it comes to cyber risks, one of the biggest challenges security professionals face is communicating the associated financial impact to the decision-makers. Assigning a dollar value to cyber risks will better equip the executive management and board to prioritize the risks, drive a stronger alignment between business priorities and cyber investments, and ultimately, make risk-aware decisions.
At MetricStream GRC Summit June 2021 Edition, Gavin Grounds from Verizon joined us for an exciting discussion on how organizations can thrive on risk to get a competitive edge.
In this blog, we have highlighted the interesting points from the discussion on how quantification can help in making the right security investment decisions.
What are some of the key challenges?
Regardless of whether it is a large organization or a small, one of the common challenges across all organizations in the area of cybersecurity is prioritization, Gavin said.
Organizations today face thousands of risks and a key challenge is to ascertain which of those is the biggest priority. Likewise, they might have hundreds of controls and they need to define the importance of these controls and determine how much to spend on each control. Every dollar they spend on these controls should be justified with the benefits/advantages realized. Because they have a finite budget, they need to use it in the most optimal manner.
How to start with Cyber Risk Quantification?
The primary objective for the CISO is to drive overall risk down and drive better-informed business decisions. And, cyber risk quantification can greatly simplify the process by quantifying risks in monetary value. As an example, suppose you got a business opportunity of $100M with $1M cyber risk, you can easily see the overall value of $99M and make your decision to go ahead or not. But if you represent your cyber risk in a way like 3 are critical, 5 are high, and 3 are mid risks, in that case, it's difficult to calculate the overall business value of that business opportunity and you might miss the first-mover opportunity on that business.
Prasad Sabbineni, EVP, Product at MetricStream, added that CRQ is the natural extension of the quantitative assessment (high, mid, and low-risk heatmaps) that organizations have been doing as all these factors serve as input to the model to calculate the dollar value of the associated risk. When asked about how organizations can start with CRQ, Prasad suggested that organizations can start small – select key risk areas and apply this quantitative technique to see the results. Once they understand the results and their value, they can gradually expand to other risk areas.
How MetricStream helped one of the largest telecom companies in their decision making
With MetricStream Cyber Risk Quantification (CRQ), a U.S. telco giant was able to make their cybersecurity decisions 50% faster by quantifying the dollar Impact of cyber risks.
MetricStream helped the company harmonize its risk management techniques and methods by driving towards a common risk score across cyber, operational risk, and resilience teams. This score is based on consistent factors and is grounded in a business context.
This combined risk score helps cyber teams accurately weigh the cost-benefit of either a single risk mitigation strategy or a combination of them. It also helps them increase the agility and speed of remediation efforts. MetricStream also provides a top-down and bottom-up 360-degree view of cyber risk.
Top-down views take risk assessment information from the business in terms of dollars—for example, how much it costs to keep an order processing system up and running. Meanwhile, bottom-up views provide data on the costs of mitigating vulnerabilities.
Conclusion
CRQ is important for every organization irrespective of the size and industry. With the interconnected fast-paced digital economy, organizations are exposed to many new risks. Prioritization and communication of risk will help in better decision-making and provide a competitive advantage in the market.
Cyber Resilience in 2021
- IT Risk & Cyber Risk
- 09 July 21

Introduction
Resilience is the ability to adapt to change and respond quickly and effectively. Cyber resilience is more than just preparing—it is ensuring that your business will still thrive in an attack. Too many organizations only concern themselves with ensuring that they have a SIEM (Security information and event management) and or SOC (Security operations center) in place. This is of course very important, but it will not ensure reliance in the event of an attack.
[Read More: Resilience Management as The New Paradigm for Cybersecurity]
Resiliency requires so much more. Risk assessments should include how vulnerable the business itself is there is a breach or ransomware attack. What confidential information could impact the business if it were to be breached? Some examples include blueprints for a new product design that is going to be launched or plans to purchase another organization.
In addition to a SIEM and SOC, the business units should also be trained on recognizing irregularities that could signal that the integrity of data has been affected. They also need to know how to report it so that the event can be investigated.
Each business unit needs a cyber response plan to allow for resiliency. There have been many organizations that were not able to respond effectively to a ransomware incident. A business unit cyber response plan is different than the business continuity response plan. It includes action steps of each business unit will follow when they are affected by a cyberattack.
The organization also needs a great cybersecurity incident response program, which includes policy and program documentation as well as playbooks for insider threat activities, regulator audits, lapses on data governance, and cyberattacks that are applicable to their domain.
[Read More: Four Key Areas to Achieve Cyber Resilience]
ISO 22316 Security and Resiliency Management and ISO/IEC 27035 Incident Response are two of the recommended standards to consider implementing as part of an organization’s cyber resiliency preparation. ISO/ IEC IT Corporate Governance is a good guideline for senior management and the board to implement in order to avoid hefty fines for poor governance. MetricStream enables organizations to align with established standards, empowering with pre-packaged content for necessary frameworks, making the solution up and running on Day 1.
Business continuity management and information/cybersecurity have to be more aligned in identifying risks. The business units understand what information they have in a database that is more likely to be sought in a cyberattack. Business continuity departments should include questions in their risk assessment surveys and interviews pertaining to what information does each business unit has that is PII or PHI or organizational confidential and work with disaster recovery teams to document which databases it resides.
While a business continuity plan may list an application as tier 1, in an incident where a database has been attacked, the cybersecurity teams may not release it in recovery when the business units need it. Cyber teams may need to do forensics or if they deem that there is malware the backups may need to be checked before they can be used. For instance, in the case of an attack was made months ago, even if just identified, all of the backups from the time of the attack may also be affected.
In summary, a good cyber governance program is needed coupled with a good cyber resilience program.
[Read More: CYBER RESILIENCE BEST PRACTICES: Connecting the Dots beyond Cybersecurity]
Kaseya Ransomware Attack: Is Your Organization Prepared for Third-Party Cyber Risk?
- IT Risk & Cyber Risk
- 07 July 21

Introduction
Yet another cybersecurity incident has highlighted the vulnerabilities of the extended enterprise. Just ahead of the Fourth of July weekend, up to 1,500 businesses worldwide fell victim to a ransomware attack centered on U.S. information technology firm Kaseya.
Understanding the Kaseya Ransomware Attack
What happened:
Kaseya is a provider of IT and security management solutions for managed service providers (MSPs) and small to medium-sized businesses (SMBs). In a statement dated July 05, the company said that its VSA product was compromised in a sophisticated cyberattack, allowing the hackers to cripple the end customers with a massive ransomware attack.
Who is responsible:
As per reports, hackers from a cyber adversary group, REvil—the threat actors who were purportedly also behind the ransomware attack on JBS last month, were able to compromise one of Kaseya’s tools. They have reportedly demanded $70 million to restore the data.
The impact:
In a press release, Kaseya said, “While impacting approximately 50 of Kaseya’s customers, this attack was never a threat nor had any impact to critical infrastructure...Of the approximately 800,000 to 1,000,000 local and small businesses that are managed by Kaseya’s customers, only about 800 to 1,500 have been compromised.”
In a statement, the U.S. Cybersecurity and Infrastructure Agency (CISA) said that it was taking action to “understand and address the recent supply-chain ransomware attack against Kaseya VSA”, adding that it “encourages organizations to review the Kaseya advisory and immediately follow their guidance to shutdown VSA servers.”
The UK's National Cyber Security Centre also issued a statement saying that they are “working to fully understand this incident and mitigate potential risks to the UK.”
The Growing Third-Party Cyber Risk
Security breaches via third parties are growing at an alarming rate both in terms of volume and sophistication. The major underlying reasons are the growing reliance on third parties for mission-critical goods and services and the amplified digital interconnectedness of organizations, further spurred by the COVID-19 pandemic.
The SolarWinds hack, the security breaches at Microsoft and Accellion, and now Kaseya, underscore the increasingly precarious digital environment businesses operate in today and how a security incident at one organization can quickly travel and paralyze several other connected businesses. According to the 2021 Ponemon Institute report, more than half of the survey respondents said that their organization has experienced a data breach caused by third parties.
Technology-Driven Approach to Third-Party Risk Management (TPRM)
Organizations today need to be proactive regarding the management of their third-party relationships and extended enterprise. Here are few key considerations for an effective TPRM program:
- Establishing a common nomenclature for onboarding, assessing, monitoring, and off-boarding third parties and centralized repository of all related information
- Ensuring clear and comprehensive documentation with well-defined clauses that provide clarity to third parties on what they need to do, including how to handle sensitive data after the contract has terminated.
- Implementing an effective third-party onboarding process which will help ascertain if the third parties are financially stable, secure, regulatory compliant, and more.
- Categorizing the third-party vendors based on the extent of their access to critical assets and impact on an organization’s margins and profitability
- Ensuring efficient fourth-party risk management to ensure visibility into the portfolio of the fourth and subsequent parties, identify the critical ones, and perform due diligence and raise red flags on an ongoing basis
A technology-based TPRM solution, embedded with these capabilities, can considerably simplify, structure, and streamline managing the entire third-party lifecycle—from their onboarding to contract termination. This approach will help organizations enhance their visibility into the risks posed by the third and subsequent parties and accelerate responses to risk events.
MetricStream helps organizations effectively manage third-party risks with its Third-Party Risk Management product. Its key capabilities, including Continuous Third-Party Monitoring, Periodic Third-Party Due Diligence, Intuitive Dashboards, and Reports, empowers organizations to protect their business from existing and potential threats from third parties, as well as strengthen resilience, contain costs, and optimize business performance. To request a demo, click here.
Read More: Boosting Third-Party Risk Management in a Time of Uncertainty (eBook)
Learnings from the Colonial Pipeline Ransomware Attack
- IT Risk & Cyber Risk
- 17 May 21

Introduction
On May 8, a deadly ransomware attack on Colonial Pipeline had reportedly halted its operations. The company’s pipeline which runs 5,500 miles along the east coast of the United States, supplies 45% of the oil and gas to that region. According to media reports on Friday, the company paid a 75 bitcoin ransom—worth around $5 million, to restore service faster. The company was able to resume operations by Wednesday night
Ransomware attacks are on the rise. According to an annual report on global cybersecurity, there were a total of 304 million ransomware attacks worldwide in 2020. This was a 62 percent increase from a year prior, and the second-highest figure since 2014 with the highest on the record being 638 million attacks in 2016.
Understanding the Colonial Pipeline Attack:
What happened:
Colonial Pipeline a critical supply engine for 45% of the oil and gas for the east coast, was hit with a ransomware attack. As per a Bloomberg report, the hackers began their attack on Thursday (6th May) stealing about 100 GBs of data.
Who was responsible:
The impact:
A Department of Transportation agency posted a regional emergency declaration for 18 states and Washington, DC, "in response to the unanticipated shutdown of the Colonial Pipeline system due to network issues that affect the supply of gasoline, diesel, jet fuel, and other refined petroleum products throughout the Affected States." The shortage has caused an increase in the average price of gas in the US, which rose from six cents, to $2.96 per gallon, according to AAA.
How Colonial responded:
In a statement, Colonial said it "proactively took certain systems offline to contain the threat, which has temporarily halted all pipeline operations and affected some of our IT systems."
On Tuesday, Colonial said it had worked with shippers to deliver about 41 million gallons to delivery points along its pipeline. The company also said it had taken delivery of about 84 million gallons from refineries as it readies to reopen its pipeline
FBI Recommendations to deal with ransomware attacks:
The FBI has released and proposed ways to protect businesses from ransomware attacks.
- Immediately secure backup data or systems by taking them offline.
- Contact law enforcement immediately.
- Collect and secure partial portions of the ransomed data that might exist.
- Change all online account passwords and network passwords after removing the system from the network.
- Delete registry values and files to stop the program from loading.
Learnings from the Colonial Pipeline hack:
With increased pressure to improve operating efficiency, energy and utility companies are adopting automation and operational technologies (OT) which means “merging” of systems within critical infrastructure networks. Pipelines, electricity grids, and water supply are now equipped and controlled by electronic network equipment that ultimately has a connection to the internet creating a whole new attack surface.
There is a need for a proactive cyber risk management approach to face these new-age cyber-attacks. Energy and utility firms:
- Need a proactive and integrated approach to IT and cyber risk management
- Should continuously monitor their attack surface for any vulnerabilities
- Must have a comprehensive business continuity and disaster recovery plan
- Need a quantitative approach to measure and prioritize cyber risks
- Should monitor extended enterprise ecosystem (third and fourth parties) for cyber risks
- Should work on achieving complete visibility of IT and cyber risks and removing silos
- Be IT and cyber compliance ready all the time to make sure they are not missing on cyber hygiene and win the confidence of auditors and management
Conclusion:
To cater to these new kinds of cyber-attacks, energy and utility firms should proactively monitor their attack surface for any kind of vulnerabilities and have a robust business continuity and disaster recovery plan in place to build cyber resilience.
MetricStream has helped Fortune 500 oil and gas companies and energy utility providers to build operational and cyber resilience, increasing operational efficiency. Please reach out to us if you'd like to schedule a demo or learn more about how we can help secure your critical infrastructure OT environment and help you build cyber resilience.
Improving Third-Party Cyber Risk Management with MetricStream and BitSight
- IT Risk & Cyber Risk
- 12 May 21

Introduction
With the growing reliance of organizations on an interconnected network of third parties, they are becoming increasingly vulnerable to a plethora of risks. A 2020 Ponemon survey found that a typical enterprise has an average of 5,800 third parties, and the number is expected to grow by 15 percent this year. As the third-party network of an organization expands, so does the number of potential points of failure.
Companies often have to share sensitive information with third-party vendors for business-critical goods and services. And, if the latter suffers any data breach, it could have a deleterious effect on the organization. Recent incidents, such as security breaches at Microsoft and Accellion, and SolarWinds hack, are unfortunate reminders of how third-party risks can make multiple organizations susceptible to illicit actors and impede their operations. Moreover, in this digital era and hyper-connected business environment, a security lapse at even a small-sized enterprise can have far reaching and disastrous consequences.
As such, implementing an effective third-party risk management (TPRM) program has become critical for today’s extended enterprise. The objective is to identify and mitigate the business, operational and cyber risks associated with the third parties, fourth, and subsequent parties, including security breaches, supply chain disruptions, unethical actions, poor performance, financial impact, and more.
TPRM Key Considerations
There are certain must-haves when it comes to a robust TPRM framework:
- Comprehensive visibility into supply chain hierarchy and mapping of the third parties to products, services, business units, fourth and subsequent parties
- Segregating third parties into critical and non-critical categories depending on their access to critical organizational assets and impact on margins and profitability
- Well-defined and comprehensive vendor contracts that details roles and responsibilities of third parties even after the contract terminates
- Performing third-party due diligence and risk assessment to determine if they are financially stable and ensure that they are operating in secure and compliant manner
- Continuous monitoring of third-party risks to determine changes in risk levels, identify new risks, and ascertain how secure third parties are
- Extend TPRM framework to fourth, fifth and subsequent parties
Implementing a centralized and technology based TPRM solution, which streamlines and digitizes these processes, has become vital for organizations to mitigate third-party risks in an efficient manner. MetricStream Third-Party Risk Management provides organizations with an integrated, real-time view of the extended enterprise and helps automate various associated processes including collating information, onboarding, continuous monitoring, risk, compliance and control assessments, and risk mitigation.
The MetricStream Arno release enhances BitSight integration, enabling proactive identification and mitigation of cybersecurity risks in the extended enterprise. When setting up the due diligence task, organizations can now define one of the stages as information security risk assessment using BitSight content. The task to review the content will be triggered as part of the due diligence workflow – the information security score and rating from BitSight can be reviewed and risk mitigation steps can be documented.
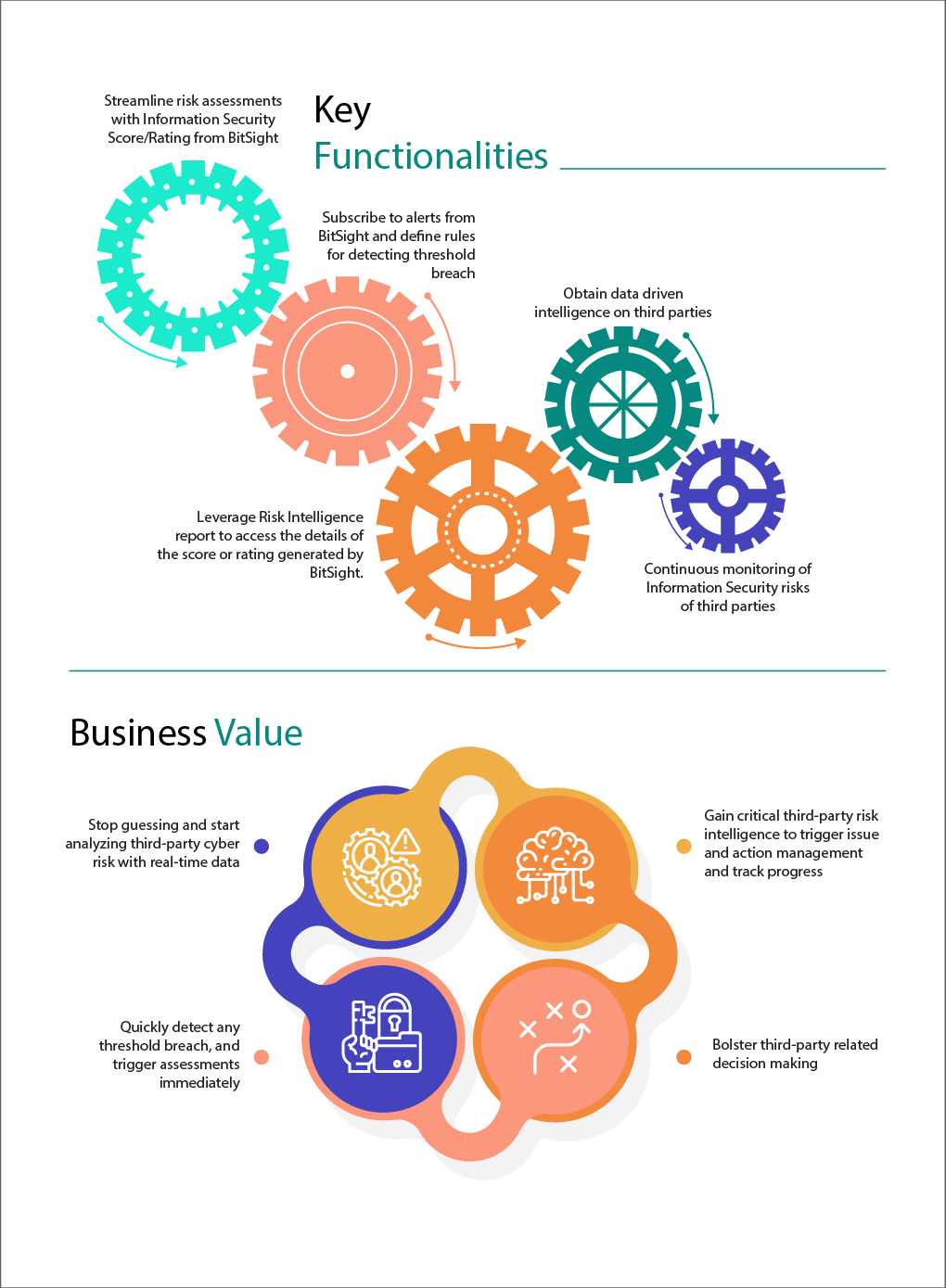
Furthermore, organizations can also leverage BitSight infosec ratings to continuously monitor third-party risks. They can also subscribe to regular or periodic alerts from BitSight for chosen third parties and define rules to automate review task assignment—when a change occurs in the BitSight score, it will automatically send notifications so that the user can review the changes and take further action.
To know more about BitSight content integration, register for the live webinar here.
Are Companies Not Paying Enough Attention to Cybersecurity? - Through the GRC Lens, April 2021
- IT Risk & Cyber Risk
- 11 May 21

Introduction
It feels like we’ve suddenly entered a rabbit hole of cyberattacks. Starting from the SolarWinds attack to Facebook’s old leak resurfacing, to the LinkedIn hack, and more, 2021 has so far been immensely challenging for cybersecurity officials, leaving only one thing on their priority list – cyber resilience – broadening protection, detection, and response measures to future-proof their cyberattack mitigation strategies.
_____________________________________________________________________
The data breach crisis escalated last year as more records were compromised in just 12 months than in the previous 15 years combined reported Canalys in a special report ‘Now and Next for the cybersecurity industry’, adding that cybersecurity must be front and center of digital plans, otherwise there will be a mass extinction of organizations, which will threaten the post-COVID-19 economic recovery.
However, not just the last year, 2021 has also brought with it a fresh set of unfortunate news. Beaming’s analysis of commercial internet traffic found that UK businesses encountered 172,079 cyberattacks each, on average, between January and March 2021, the equivalent of 1,912 per day, reported Information Age.
And although, there seems to be an increase in number of attacks, a new report from Audit Analytics, “Trends in Cybersecurity Breach Disclosures,” revealed that cyber breach disclosures fell in 2020 for the first time in five years. “It would not be surprising to learn of additional attacks that occurred throughout 2020 that remain undisclosed,” Audit Analytics said.
Post this report, Booking.com was fined €475,000 after failing to report a serious data breach that happened in 2018. The Dutch Data Protection Authority imposed the fine, after calling the incident a “serious violation” of the EU’s data protection regulation. AP vice president Monique Verdier said in a statement: “This is a serious violation. A data breach can unfortunately happen anywhere, even if you have taken good precautions…But to prevent damage to your customers and the recurrence of such a data breach, you have to report this in time.”
According to Compliance Week, “The costliest cyber-security breaches aren’t necessarily those that result in the largest loss of records as much as the type of data stolen.” But it does seem like negligence and non-compliance have a number that keeps going up. The world’s top brands across sectors might lose between $93 billion and $223 billion because of a data breach, a first-of-its-kind study by Interbrand and Infosys, called ‘Invisible Tech, Real Impact’, has found. Following the report, Macquarie was slapped with a $500m capital buffer after ‘multiple breaches’ by the Australian Prudential Regulation Authority.
More recently, Gartner released its Emerging Risks Monitor Report which identified cybersecurity control failures as the top emerging risk in 1Q21 in a global poll of 165 senior executives across function and geography. Cybersecurity control failures also ranked third overall in “risk velocity,” an additional metric that Gartner tracks in the Emerging Risks Monitor Report.
Current research estimates that this year alone, businesses will spend $106 Billion on cybersecurity, and that is a direct result of a 300% increase in cybercrimes that have been reported to the FBI since COVID-19 started, said Suzy Greenberg, Vice President of Intel Product Assurance and Security for Intel, in conversation with Forbes.
The Need of the Hour
Security and risk management leaders must address these eight top trends: Cybersecurity Mesh, Identity-First Security, Security Support for Remote Work, Cyber-Savvy Board of Directors, Security Vendor Consolidation, Privacy-Enhancing Computation, Breach and Attack Simulation, and Managing Machine Identities, to enable rapid reinvention in their organization, said Gartner, Inc, adding that by 2025, 40% of boards of directors will have a dedicated cybersecurity committee overseen by a qualified board member, up from less than 10% today.
While talking to Strategic Risk Europe about the art of the con, cyber security strategist Eddie Doyle said, “Threat actors are always going to be out there, so creating technologies to stop them is necessary…We’re already starting to see the future, which is all about blockchain and artificial intelligence…but today, what we can do is make sure that every employee is identified within our system, and that the remote access control is unique to each and every person. You need massive granularity on a system so you can see where users go, what they’re doing, and what things they’re trying to touch and not trying to touch.”
The World Economic Forum (WEF) recently published a report in collaboration with the National Association of Corporate Directors (NACD) and the Internet Security Alliance (ISA), and PwC. The report listed six consensus principles for cybersecurity board governance:
- Cybersecurity is a strategic business enabler
- Understand the economic drivers and impact of cyber risk
- Align cyber risk management with business needs
- Ensure organizational design supports cybersecurity
- Incorporate cybersecurity expertise into board governance
- Encourage systemic resilience and collaboration
Gaurav Kapoor, Co-Founder and Chief Operating Officer at MetricStream, called for a collaborative effort between organizations and regulators to ensure operational resilience in these unprecedented times. “Due to remote working and rapid digitization, the year 2019 and 2020 witnessed the highest number of cybersecurity breaches, financial frauds and third-party risks,” Gaurav said. “It is now critical for companies especially banks and financial services institutions, and regulators to work together to create the conditions where companies take advantages of business growth opportunities and accelerate digital transformation while remaining operationally resilient throughout.”