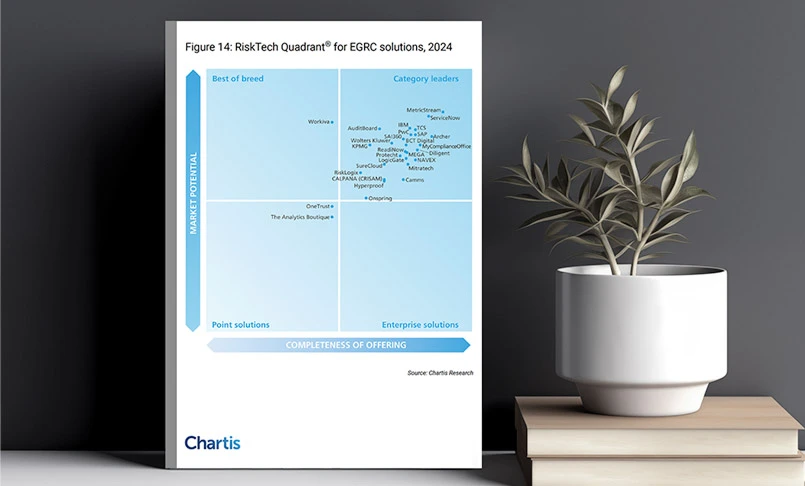
Healthcare Risk and Compliance: 5 Key Challenges to Address in 2024
- GRC
- 18 July 24

Introduction
Healthcare is one of the most strictly regulated sectors in the world. This is understandable and necessary considering that the sector deals with factors as crucial and sensitive as health and life itself. As a result, this sector has witnessed increasing regulatory complexity with different regulatory bodies focusing on various aspects of the industry. The healthcare business is also rapidly evolving and expanding with many providers offering ancillary services such as health insurance and insuretech. This makes the sector susceptible to various new and emerging risks. Healthcare providers also work with third parties who handle sensitive patient information, making it vital for them to effectively manage third-party risks. As regulatory complexity increases amidst a fraught risk landscape, ensuring compliance can be challenging.
In April 2024, records of 13.4 million patients were left exposed thanks to nine incidents of unauthorized access or disclosure of protected health information. 44 hacking incidents in the same month affected 1,919,637 records. The consequences of such breaches through penalties and impact on reputation and image are significant. This blog explores the top five risk and compliance challenges for the healthcare sector and how to address them.
1. Regulatory Compliance
The healthcare sector is governed by regulations and frameworks such as Health Insurance Portability and Accountability Act (HIPAA), the HITECH Act that complements HIPAA by increasing the penalties for data breaches, the 21st Century Cures Act, General Data Protection Regulation (GDPR), PCI DSS, California Consumer Privacy Act (CCPA), Health Information Trust Alliance Common Security Framework (HITRUST CSF), Information Blocking Rule (2021) and Interoperability and Patient Access Final Rule (2021). Most of these focus on patient data privacy, data security, access to information, and cyber security.
Each of these is constantly being updated to keep pace with a rapidly changing risk landscape. For example, this year HIPAA saw some significant updates to its patient privacy provisions and outlined stricter cyber security requirements. It gives patients greater control over their data and mandated risk assessments, incident response plans, data encryption requirements, and updated breach notification requirements. Keeping pace with these updates, assessing their impact on various processes and functions, and adapting internal controls and policies is a significant challenge.
Furthermore, there are federal, state, and local regulations and rules that apply to healthcare providers. Each state has specific reporting requirements regarding public health emergencies, infectious disease outbreaks, and specifying how long medical records can be retained. Some states may even have their own laws regarding patient data. For example, California has laws pertaining to data breach notifications that have to be complied with in addition to HIPAA. Healthcare providers must report relevant situations to their state or local agencies in the prescribed format in addition to complying with federal regulations.
Additionally, healthcare providers must be accredited by industry organizations such as The Joint Commission (TJC) that evaluates organizations on parameters such as patient care safety and healthcare management, Accreditation Association for Ambulatory Health Care (AAAHC), and Urgent Care Association (UCA). This shows that the provider meets quality and safety benchmarks set by the governing bodies. Meeting accreditation requirements, and complying with standards set by each of these bodies is a complex and challenging task.
2. Enterprise Risk and Incident Management
Healthcare providers have to efficiently manage risks unique to the sector, in compliance with the relevant regulations. In addition to compliance risks, healthcare providers have to be prepared to deal with risks related to patient care and safety as any lapses can have severe legal and financial impacts in addition to damaging reputation and trust. They must be cognizant of risks pertaining to medical instruments and devices in the form of potential malfunctions that impact patient care. There are also risks pertaining to insurance claims, frauds, phantom billing, and upcoding. They have to conduct risk assessments periodically to identify and mitigate potential compliance issues and threats. They also must have comprehensive incident management processes in place to report and respond to crises quickly and effectively. Risks ranging from business operations, third parties, cybersecurity, ESG, and health hazards must be managed effectively along with appropriate business continuity plans. The healthcare industry must move from compliance check-in-the-box activity to proactive risk management to thrive in the complex risk landscape.
3. Data Privacy and Cyber Security
Patient healthcare data and records are sensitive and subject to strict security, privacy, and protection laws. Healthcare providers have to ensure that their technology systems meet HIPAA standards, which may prove to be a daunting exercise, particularly for smaller organizations.
Regulations like the 21st Century Cures Act emphasize the need for seamless and secure data sharing. And so, organizations must ensure their electronic health record systems are updated, secured, compliant with regulatory standards, and capable of securely executing data exchanges. It is equally important to ensure that different healthcare systems are interoperable while maintaining data security and privacy. Organizations must also ensure that their technology systems are updated and compliant with the latest security and regulatory standards to protect patient information and ensure foolproof compliance.
Adding to the challenge is the fact that the threat landscape is continually evolving with bad actors increasingly leveraging advanced technology to launch sophisticated attacks. Protecting health care data under these conditions can be a Herculean task. In February 2024 alone there were 24 data breaches, the biggest of which was the breach at Medical Management Resource Group that compromised 2.35 million records. Hacking and ransomware continue to plague the sector and only four breaches affecting 10,000 or more records in February were not hacking incidents. Data encryption is important to protect healthcare records. But ensuring encryption both in transit and at rest to prevent unauthorised access is a challenge.
The rapid evolution of Artificial Intelligence technologies has the potential to transform healthcare. From early detection, faster diagnoses, and better treatment to improved monitoring, decision-making, research, and training, AI is already being leveraged to drive better healthcare outcomes. But, AI comes with a significant risk of data breaches. AI platforms process huge volumes of sensitive data and any vulnerabilities can be exploited by bad actors. Healthcare providers leveraging AI must be cognizant of the security risks associated with it and implement stringent data protection strategies.
4. Third-Party Risk Management
Healthcare organizations rely on numerous external vendors ranging from cloud service providers to billing companies, medical device manufacturers and suppliers, and more. Many of these have access to sensitive healthcare data and are subject to the standards set by HIPAA. This is also a vulnerability that can be targeted by hackers. Additionally, healthcare providers must monitor third parties for operational and ethical risks as well as such unavailability or disruptions to medical services, AML, bribery, and other malpractices. Third-party organizations are subject to data protection and privacy regulations such as GDPR and PCI DSS. Healthcare providers must monitor their partners’ compliance with all relevant regulations, as well as their overall risk management and mitigation strategies.
Managing third-party risk must be a crucial part of a healthcare organization’s risk management strategy. They must conduct regular due diligence with vendor risk assessments and security assessments. Compliance with all relevant regulations and standards, and risk evaluation must be a contractual obligation for all third-party vendors working with healthcare organizations. In fact, the HITECH ACT extends HIPAA’s regulations to vendors and includes penalties for vendors for non-compliance. Healthcare organizations must regularly monitor their partners and conduct comprehensive and periodic audits to ensure ongoing compliance. Establishing BAAs with vendors to ensure compliance with a wide range of regulations is advisable, but managing third-party risks adds to the significant compliance challenges of healthcare organizations.
5. Continuous Monitoring and Reporting
Healthcare providers are operating within a regulatory landscape that is continuously evolving and they must ensure error-free compliance. They have to monitor the regulatory landscape on an ongoing basis to keep pace with emerging regulations and have the capability to adapt and map new regulations and updates to existing practices and controls. Continuous and automated monitoring of risks and controls is crucial for enabling real-time risk assessments, quick decision making, and faster, more effective mitigation efforts. They must have rationalized internal controls to mitigate risks and ensure compliance. They must have automated processes to onboard new third parties and carry out due diligence to ensure there are no gaps in compliance. They must also conduct regular digitized audits and continuous monitoring of compliance processes to ensure there are no gaps. Maintaining compliance reports, logs of security events and communicating with regulatory authorities is another key task for organizations.
Power-Up Your GRC Program with MetricStream
MetricStream’s Healthcare solution is purpose-built to help organizations in this highly regulated industry adopt and implement a streamlined, automated, and integrated approach to GRC. Healthcare providers can leverage advanced capabilities for managing regulatory compliance, enterprise risks, including cyber and third-party risk, and internal audit, to improve their overall risk and compliance posture and drive better-informed decision-making.
With MetricStream, your organizations can effectively:
- Improve risk visibility with faster response to perceived risks, automate capture and management of regulatory changes
- Streamline and digitalize GRC activities across the three lines of defense
- Enhance cyber resilience with 360-degree visibility into cyber risks, threats, vulnerabilities, risk exposures, and compliance violations
- Simplify and improve third-party risk management with automated processes for onboarding, real-time monitoring and control assessments
- Prioritize internal audits with risk-based audits and automate audit reporting
Interested to find out more? Request a demo now.
Apple Bank Enhances and Streamlines Cyber Risk Management Program with MetricStream
- IT Risk & Cyber Risk
- 10 July 24

Introduction
At the 2023 GRC Summit, MetricStream’s annual flagship event, Jonathan Ruf, First Vice President - Head of Cyber and Information Risk, Apple Bank, discussed how the organization leveled up its cyber risk management program with MetricStream. Apple Bank is the largest state-chartered savings bank in New York.
Here are the key takeaways from Jonathan’s session at the summit.
Getting Started
Jonathan: We started the Journey with MetricStream about four years ago, and the use case was more so around the operational risk. It wasn't necessarily a decision that we were going to use it in cyber and information security. But we realized that there were a lot of synergies, so we took this on.
So, at the beginning, we relied on a GRC process. But what does that really mean if you don't have a framework or a tool? Great value was given, but we needed something to scale, and early on, the selection was made that MetricStream was going to be the tool for Apple Bank. It fit our needs, and it had a roadmap that definitely appealed to us.
Challenges
Jonathan: As we began this journey, my cyber and information risk management team found a lot of opportunities for improvement.
What did we have? Manual processes, spreadsheets all over the place, disparate data sources. There was no central inventory of applications, or even a well-populated CMDB. It was very difficult to understand what was available and what was being done ad hoc.
We had control validations. For each of the risk assessments, the controls needed to be validated, and they were stored in file shares -- again, decentralized.
Issues and exceptions were PDF documents. You can't report on them.
And the assessments. If you aren't centrally managing your assessments, then how are you reporting them? At the end of the day, it’s about reporting, it’s about system integration, and it's about moving to the next level to reduce the manual efforts and to increase the automation of your security monitoring tools for the organization.
The Journey So Far
Jonathan: We standardized and automated the process for initiating the risk assessment of application services and infrastructure services.
Let’s look at the risk assessment lifecycle. We're also going to see in this lifecycle how we have integrated systems through APIs.
A GRC isn't an inventory. It's not where you should be holding your assets or your infrastructure components, it's not a CMDB, it's none of those things. You need a source of truth for everything. So, your vendors, your applications, your CMDB, those are in-source systems. But we want to ingest this information. Ingesting this information is difficult because it was manual, and manual processes are prone to errors. But now, we have the ability to pull directly from our inventory sources and schedule assessments.
Considering we're a bank, we are highly regulated. We're also a New York State Bank, so we're even more scrutinized with DFS. We have the GLBA and we have DFS risk assessments that need to be done on in-scope applications on an annual basis. But this information is stored in our application inventory, not in our GRC. So, what we need to do is we need a push-pull mechanism we can schedule those assessments based on the date the last assessment was completed, and it will automatically send out those notifications -- never touching the integrity of the source system data within a GRC.
So, why are we not using this information to validate these controls? We have it. Let's use it. I had just one source here, which was Qualys. So, I could say, okay, an infrastructure comes in and it could scan it for vulnerabilities. That's pretty simple.
But we also want to look at -- Is it integrated with SSO? Does it have MFA? Is data encrypted? Is the database connection pool secure? We can bring all of this information in through our APIs, and this is all living in MetricStream. So, we got our source systems and we got our security monitoring tools feeding assessment. It's reducing the burden on the lines of business and providing a more accurate and realistic depiction of risk to the organization.
We just finished with a wonderful, smooth upgrade from Arno to Danube. Now, in every release moving forward, we'll have a low-code/no-code API framework. That's a game changer because if you don't put that in place, creating one-off integrations is going to be a nightmare. Now, you have a low-code/no-code methodology to integrate these systems.
Business Value Realized
Jonathan: We have made such tremendous progress in our cyber risk management portfolio. It just really is truly inspirational and light years from where we first started.
MetricStream solution currently supports 500+ employees. This extends all the way to our 86 branches, to our multiple headquarters. It provides us with qualitative and quantitative cyber risk information. This is stuff that we can really use, and that drives decisions because ultimately, at the end of the day, we want to provide enriched information to our C-level and our board.
Business Value and Realized Benefits
- Supports 500+ employees – centralized and streamlined risk assessment, issue tracking for critical processes and IT assets
- Provides qualitative and quantitative cyber and information risk assessment results, centralized risk register, detailed metrics, and KRIs for senior management and board committees
- Facilitates continuous control monitoring of 100+ processes
- Significant increase in risk visibility through centralized and streamlined reporting
- Reduced time taken to manage and close issues and action plans
- Reduced the risk of compliance violations, penalties, and reputational damage with timely insights on compliance readiness at each organizational level
- Prescriptive control recommendations for issue management
You can watch the complete session here:
Also Read:
Cloud Security Risks in 2024: What You Need to Know to Stay Safe
- IT Risk & Cyber Risk
- 02 May 24

Introduction
As technology rapidly develops, the cloud has become synonymous with convenience, scalability, and cost-effectiveness in data management and operations for businesses worldwide. However, this evolution comes with its own set of vulnerabilities – cloud security risks.
Cloud security risks are potential vulnerabilities or weaknesses in the cloud infrastructure that could be exploited by cyber attackers, leading to unauthorized access, data breaches, service disruptions, and compliance violations. The challenges are exacerbated by an organization’s reliance on multiple, diverse, and complex cloud environments.
The management and assessment of these cloud security risks often require collaboration among various teams, including security operations, risk management, DevOps, and IT teams. They need to continuously monitor the cloud infrastructure, assess associated risks, implement mitigation measures, and report the data and insights to the CISO.
Before diving deeper, it's crucial to differentiate between risks, threats, and challenges in the context of cloud security.
- A risk is the potential for a threat to exploit a vulnerability, adversely impacting the organization.
- A threat is anything that can exploit a vulnerability, intentionally or accidentally, and obtain, damage, or destroy an asset.
- A challenge encompasses the difficulties in securing the cloud environment, ranging from technical issues to regulatory compliance and skill gaps.
Understanding these definitions lays a clear groundwork for appreciating the complex landscape of cloud security and its implications for businesses leveraging cloud technology. This blog delves into the top cloud security risks, threats, and challenges that risk and security teams need to closely monitor.
Top 5 Cloud Security Risks
Here are the top five cloud security risks faced by organizations today:
- Misconfiguration and Inadequate Change Control
One of the most pervasive cloud security risks is misconfiguration. As cloud environments become more complex and intertwined, the chances of leaving a virtual door open increase. Misconfigurations can occur at any level – from storage buckets set to public without intention to unsecured API endpoints, or improper security group settings. These missteps provide easy entry points for attackers.
Organizations often underestimate the importance of continuous vigilance and expertise required to maintain cloud configurations properly. Without adequate change control mechanisms and regular configuration audits, accidental exposure of sensitive data or resources becomes a looming risk. - Insecure Interfaces and APIs
APIs and interfaces are the linchpins of cloud services, offering the means for users to interact with cloud services and for services to communicate among themselves. However, these are also prime targets for attackers due to their accessibility. Insecure APIs can lead to unauthorized access, data leakage, and service manipulation.
Ensuring API security necessitates rigorous access controls, encryption in transit and at rest, and regular audits to identify and rectify vulnerabilities. - Account Hijacking
Cloud services often centralize access to resources under specific user accounts or identity credentials. If an attacker successfully hijacks these credentials, they can access sensitive data, disrupt services, and leverage the cloud resources for malicious purposes, such as launching further attacks.
Furthermore, account hijacking can lead to identity theft, financial fraud, and reputational damage for the affected organization. The ramifications of account hijacking extend beyond the immediate breach, as attackers may exploit compromised accounts for prolonged periods, causing persistent harm to the organization's operations and integrity. - Insider Threats
The human element remains one of the most unpredictable variables in cloud security. Insider threats can range from negligent employees unintentionally exposing data to malicious insiders intentionally sabotaging systems or stealing information.
Given the access privileges necessary for certain roles, insiders can cause significant damage or data loss. The inherent trust placed in employees with elevated access privileges makes them potent vectors for insider threats, as they possess the capability to inflict significant damage or loss of data within the cloud environment. - Data Breaches and Data Loss
Data breaches and data loss represent critical cloud security risks that can have severe consequences for organizations. Whether due to malicious attacks, accidental exposure, or insider threats, the compromise of sensitive data can lead to significant financial losses, reputational damage, and regulatory penalties.
Data breaches occur when unauthorized parties gain access to sensitive information stored in the cloud, resulting in theft, manipulation, or exposure. On the other hand, data loss refers to the unintentional destruction or unavailability of data, often due to system failures, human error, or natural disasters.
5 Recent Cloud Security Threats
Here’s a look at five recent cloud security threats that organizations across industries have been exposed to:
- Zero-Day Exploits
Zero-day exploits refer to vulnerabilities in software or hardware that are unknown to the vendor and, therefore, have no patch or fix available. These vulnerabilities pose a significant threat to cloud security as attackers can exploit them to launch targeted attacks without detection. Since there is no prior knowledge of these vulnerabilities, organizations are often caught off guard, leaving their cloud environments vulnerable to exploitation.
Zero-day exploits enable cybercriminals to bypass traditional security measures, gaining unauthorized access to sensitive data or compromising cloud infrastructure. - Cyberattacks
Cyberattacks encompass a broad range of malicious activities perpetrated by threat actors with the intent to compromise cloud security and disrupt business operations. These attacks can take various forms, including malware infections, phishing campaigns, ransomware attacks, distributed denial-of-service (DDoS) attacks, and man-in-the-middle (MitM) attacks.
Cybercriminals target cloud environments due to their rich troves of data and interconnected infrastructure, making them lucrative targets for exploitation.
Depending on the nature and sophistication of the attack, cyberattacks can result in data breaches, financial losses, reputational damage, and regulatory fines. - Inadequate Identity and Access Management (IAM)
Effective Identity and Access Management (IAM) is the cornerstone of robust cloud security. However, inadequate IAM policies pose a significant threat, leading to unauthorized access and potential insider threats.
As organizations expand and embrace hybrid work environments, managing who has access to what becomes exponentially complex. This complexity is further exacerbated by the sheer volume of users, devices, and third-party vendors requiring access to cloud resources.
Inadequate IAM can result in excessive permissions, where users have more access rights than necessary, significantly increasing the risk of data exposure or loss should those credentials be compromised. - Advanced Persistent Threats (APTs)
APTs represent a sophisticated, high-level threat wherein an attacker gains unauthorized access to a network and remains undetected for an extended period. The cloud environment, with its vast resources and data, is an attractive target for APT groups. These adversaries use advanced techniques to bypass traditional security measures, leveraging the cloud to infiltrate networks and exfiltrate sensitive information stealthily.
APTs can cause significant financial and reputational damage to organizations.
The complexity and frequency of these attacks are expected to increase, emphasizing the need for advanced threat detection and response strategies in the cloud ecosystem. - Data Security Non-Compliance
Data security non-compliance refers to the failure of organizations to adhere to regulatory requirements, industry standards, or internal policies governing the protection of sensitive data in the cloud.
Non-compliance can result from inadequate security controls, improper data handling practices, or a lack of awareness regarding data protection obligations. Failure to comply with data security regulations such as GDPR, HIPAA, or PCI DSS can have severe consequences, including legal penalties, financial sanctions, and reputational damage.
Moreover, data breaches resulting from non-compliance can erode customer trust and confidence in the organization's ability to safeguard their personal information.
Top 5 Challenges in Cloud Security
Organizations face a number of challenges in their effort to strengthen the security of their cloud environment. Here are the top five challenges:
- Lack of Cloud Security and Skills
One of the biggest challenges that organizations face in cloud security is the lack of knowledge and skills required to implement and maintain robust security measures. In most cases, companies do not have dedicated security teams for cloud infrastructure, which leads to a lack of awareness of potential risks and security vulnerabilities. Furthermore, companies often struggle to find qualified personnel to fill security roles due to the ongoing shortage of skilled cybersecurity professionals. - Shadow IT
Shadow IT refers to the use of unauthorized applications and services by employees without the knowledge or approval of the IT department. This practice is becoming increasingly common, and it poses significant risks to cloud security. Shadow IT often circumvents security controls and creates security vulnerabilities. Companies often have limited visibility and control over these applications, which can result in a lack of control over sensitive data. - Identity and Access Management
Organizations must implement access controls to regulate the flow of information within and outside the organization. Unfortunately, access management can be challenging to implement in a cloud environment where users and applications can access resources from multiple locations. Misconfiguration, weak passwords, and authentication failures are common vulnerabilities that cyber attackers leverage to compromise systems. - Managing a Rapidly Evolving Attack Surface
The dynamic nature of cloud environments, characterized by frequent updates, deployments, and configuration changes, creates new opportunities for cyber attackers. Traditional security measures designed for static on-premises environments may prove inadequate in the face of these dynamic threats. Also, the increasing adoption of DevOps practices and continuous integration/continuous deployment (CI/CD) pipelines further amplifies the challenge by accelerating the pace of change. - Multi-Cloud Security
The adoption of multi-cloud environments, where organizations utilize services from multiple cloud providers, introduces unique security challenges. Managing security across diverse cloud platforms requires a comprehensive understanding of each provider's security offerings, compliance requirements, and integration capabilities. Moreover, interoperability issues, data migration challenges, and differences in governance models between cloud providers can complicate security management efforts.
Tips to Strengthen Cloud Security
Here are the key measures that organizations need to implement to strengthen their cloud security posture:
- Adopt Data Encryption Practices: Encrypt your data at rest and in transit. Utilizing strong encryption algorithms helps safeguard your data from eavesdropping and unauthorized access, ensuring that even in the event of a data breach, the information remains unintelligible to the attackers.
- Regularly Monitor and Audit Cloud Environments: Continuous monitoring of your cloud environment can alert you to unauthorized activities and potential vulnerabilities. Implementing automated security solutions can help in the early detection of anomalies and enable prompt response to mitigate risks.
- Adopt a Zero-Trust Security Model: Operate under the assumption that threats can originate from anywhere, and nothing should be trusted implicitly. A zero-trust approach necessitates strict identity verification for every person and device attempting to access resources in the cloud, providing a more granular level of security control.
- Embrace a Culture of Security Awareness: Human error remains one of the weakest links in cloud security. Educating your workforce about phishing schemes, safe online practices, and the importance of using strong passwords can drastically reduce the risk of security breaches.
The future of cloud security is uncertain but exciting. As companies continue shifting more data and services to the cloud, threats are evolving rapidly. However, by staying up to date with trends, learning from past errors, and making security a significant priority, organizations can thrive in the cloud. The payoff is peace of mind knowing your data is fortified behind impenetrable defenses.
MetricStream helps organizations across industries manage IT and cyber risks and compliance processes in a holistic, proactive, and integrated manner. To learn how MetricStream can help you implement industry best practices for Cyber governance, risk management, and compliance (CyberGRC), request a personalized demo today.
Update on the SEC’s New Cybersecurity Rules: Insights and Outlook
- IT Risk & Cyber Risk
- 04 April 24

Introduction
It’s been several months since the U.S. Securities and Exchange Commission (SEC) approved the final rules governing cybersecurity disclosures on July 26, 2023. For risk management, strategy, and governance disclosure requirements, companies are required to provide the disclosures beginning with annual reports for fiscal years ending on or after December 15, 2023, while compliance with incident disclosure requirements commenced from December 18, 2023.
So what’s been happening since the new rules were introduced? We bring you a high-level summary of what’s been going on to date, including:
- The recent form 8-K filings and 10-K disclosures
- Defining materiality according to the new rules
- Balancing competing risks during disclosures
Form 8-K filings: Few Companies Have Filed till Date
Six companies have filed incident disclosure requirements so far, with three of these companies additionally amending their initial Form 8-K filings to offer further insights into subsequent events. Companies that have filed include footwear maker VF Corp, insurer First American, and tech giants Microsoft and Hewlett Packard Enterprise (HPE).
An interesting observation is that both Microsoft and HPE indicated they were filing the disclosures voluntarily since they weren’t aware of a material impact from the attacks. Microsoft submitted an 8-K filing on January 19, 2024, to the SEC, disclosing that Nobelium, a Russian hacking group, had gained access to its top executives' email accounts, specifically targeting those in its cybersecurity and legal departments. According to Microsoft’s notice, the Russian hackers used permissions attached to a hacked account to access corporate email accounts, “including members of our senior leadership team and employees in our cybersecurity, legal, and other functions.”
The above 8-K filings reiterate the importance of building a strong foundation of cyber resilience where an effective response plan is matched with a detailed cyber governance, risk, and compliance (cyber GRC) program. This will enable efficient and agile response as mandated by the new rules.
How are Organizations Dealing with the Materiality Definition?
The SEC's final cybersecurity rules require filing an 8-K only when materiality is determined, rather than upon incident detection. However, such determinations must be made promptly "after discovery of the incident," without unreasonable delay. This implies that organizations must assess materiality based on both current and anticipated future impacts. Moreover, the rules specify that determinations cannot wait for future impacts to manifest.
While defining the materiality of a risk event, the analysis should take into account qualitative and quantitative factors in assessing materiality.
In a recent webinar I hosted, Brian Fricke, CISSP, CISM, CISO, and City National Bank Florida, dove into what “material” means. He listed a few examples of quantitative and qualitative factors that companies should consider when assessing the materiality of a cyber incident.
Examples of quantitative factors to consider when assessing the materiality of a cyber incident
- Impact on financial condition or results of operations
- Expenses for incident response and remediation
- Costs of potential regulatory or legal proceedings as a result of the incident
- Impact on the company’s assets
Examples of qualitative factors to consider when assessing the materiality of a cyber incident
- Harm to a company’s reputation, customer or vendor relationships, or competitiveness resulting from the incident (termination or material breach of a material contract)
- Impact on a company’s previously announced business plans or trends
- Nature and scope of the attack and unauthorized access to or misappropriation of information
- Duration of the incident and company response time
- The company’s ability to restore affected systems and data
- The company’s ability to resume normal operations after an incident
- Third-party risk (performance, breaches, reputation, etc.)
Watch the webinar for more insights on how to manage cyber risk in a mature, effective way: Navigating the Future of IT Risk and Compliance
Form 10-K Disclosures: Companies Need to Balance Competing Risks
Starting from fiscal years ending on or after December 15, 2023, public companies will need to comply with updated cybersecurity disclosure regulations in their Annual Reports on Form 10-K. Meeting these requirements pose a challenge for companies as they must strike a balance between disclosing enough information to comply with regulations and safeguarding against potential risks. Over-disclosure could expose the company to threats from malicious entities seeking to exploit vulnerabilities or defensive strategies.
However, it remains crucial for companies to provide accurate disclosures that align with the SEC cybersecurity rules, particularly given the ongoing enforcement proceedings involving SolarWinds Corp by the SEC. The SolarWinds enforcement case marks a significant development in two aspects. Firstly, the SEC alleges intentional deception in cybersecurity disclosures by a company, departing from previous cases where negligence was cited. Secondly, it represents the first instance where the SEC has pursued individual enforcement action against a corporate officer in a cybersecurity disclosure matter.
Both Clorox and Johnson Controls, having recently experienced ransomware attacks, have submitted filings to the SEC detailing the costs incurred from operational disruptions and financial losses stemming from cyber-related incidents. Although it remains uncertain whether these filings directly comply with this rule, particularly considering the timing of the attacks, they underscore the growing tendency towards more frequent and comprehensive disclosures. More importantly, it reflects an increasing acknowledgment of cybersecurity incidents as material risks capable of impacting both financial performance and operational continuity.
Achieve Compliance with MetricStream CyberGRC
With an increase in cyber risk and regulatory efforts globally, not just the U.S., it becomes imperative for organizations across diverse sectors and industries to build cyber resilience that can not only ensure compliance but optimize cybersecurity processes and improve efficiencies.
MetricStream’s CyberGRC solution can help you streamline your cyber risk management program and achieve compliance with the SEC’s new cybersecurity rules. Read our blog for a comprehensive mapping of how we can help you achieve compliance with the various aspects mandated by the SEC Rules, including:
- Establishing consistent procedures for incident documenting, analyzing, and remediating till closure
- Maintaining a single source of truth for incident lifecycle for quick and efficient reporting
- Assessing and managing IT and cyber risks in a standardized manner using industry frameworks, such as ISO 27001 and NIST
- Generating comprehensive reports providing in-depth visibility into the overall security posture and insights into risks, compliance, and performance of third-party vendors
- Implementing an integrated GRC solution to obtain real-time status monitoring and comprehensive reports, providing in-depth visibility into overall risk management systems and processes
Interested to know more? Request a personalized demo.
Download eBook: Overview of SEC Cyber Disclosure Rules 2023
Read blog: Achieve Compliance with SEC’s New Cybersecurity Rules
View Infographic: SEC’s New Cybersecurity Rules 2023: Top FAQs Answered
Healthcare Cyber Resilience: Key Measures for Mitigating Cyber Risks in 2024
- IT Risk & Cyber Risk
- 21 February 24

Introduction
Here’s a headline that demands attention! 116 million individuals in the United States were impacted by large health data breaches in 2023. What’s more! According to records from the Office for Civil Rights as of December 21, 2023, the data reported to the Department of Health and Human Services shows that the number has more than doubled when compared to 2022.
The motivation for the relentless targeting of this sector is clear – healthcare institutions are treasure troves of valuable personal and sensitive data, making them lucrative targets for attacks and ransomware. However, while being substantial, the consequences of a cyberattack on healthcare go beyond financial losses; it directly impacts patient safety and security, potentially turning it into a matter of life and death. Tampered patient history, delayed life-saving tests, diverted ambulances, and compromised medical procedures are just a few examples of the real-world consequences that patients may face.
As the digital frontiers expand in 2024, with artificial intelligence (AI) becoming more integral in diagnostics, patient data management, and medical tools, healthcare organizations will need to bolster their cyber risk and resilience strategies.
Rapid Digitization, Surging Data Value, and More—Healthcare Faces Distinct Cyber Risk Challenges
Despite increased focus and investment in cybersecurity, healthcare organizations continue to grapple with persistent challenges unique to their industry. Securing patient information remains a formidable task. In 2023 alone, more than 133 million patient healthcare records in the United States were either exposed or impermissibly disclosed. Additionally, vulnerabilities in connected medical devices, reliance on outdated IT systems, and the need to manage compliance with evolving regulations contribute to the complex cybersecurity landscape.
The expansion of the attack surface through digitization, connected third-party systems, and cloud adoption has further intensified cyber risks. 73% of healthcare companies store data in the cloud, of which 43% is patient or protected health information. Amidst these challenges, human error (such as clicking on a phishing email), responsible for 85% of data breaches, persists due to resource limitations and a lack of cybersecurity training for healthcare professionals.
Agile, Continuous, and Connected—Mitigating Cyber Risk in 2024 Requires a New Approach!
As healthcare systems become increasingly interconnected, the traditional siloed management of cyber risks and reliance on time-consuming manual processes are no longer effective. These outdated methods hinder the swift detection and response necessary in the face of emerging threats. In today's context, where a single phishing email can compromise millions of patient records and disrupt entire systems, the need for agility and prompt mitigation of cyber risks is more crucial than ever. Embracing an agile, continuous, and connected strategy is paramount to fortifying healthcare organizations' resilience against the rapidly evolving cyber threat landscape.
Your cyber risk management strategy in 2024 should include:
- Automating control testing with continuous control monitoring (CCM) to ensure that all controls – physical, technical, operational, and administrative – embedded across medical devices, systems, data, and networks are regularly tested.
- Cyber risk quantification to forecast monetary impact, which will aid in investment decisions, insurance calculations, and communicating criticality to non-technical stakeholders.
- Integration of third-party risk management into your cyber risk management strategy, instead of viewing it in a silo, to ensure proper due diligence, regular monitoring, and security assessments to understand your third party’s data security practices, level of compliance, certifications (e.g., HITRUST, ISO 27001), and business recovery plans.
- Harmonizing controls across multiple frameworks and standards to ensure that there are no gaps with cybersecurity frameworks like HIPAA, HITRUST, NIST CSF, and ISO 27001, and to enhance overall security posture.
- Establishing a risk-aware culture by involving everyone in cyber risk management, simplifying security policies, providing intuitive tools for reporting incidents, and conducting regular training and awareness programs.
Download an infographic on this topic to explore more: Cyber Risks in Healthcare: How to Prepare
MetricStream: Your Partner to Manage Cyber Risk and Build Cyber Resilience
In the face of these multifaceted challenges, healthcare organizations must reassess their cyber risk management practices. As the sector strives to minimize the risk of data breaches and cyberattacks, addressing complexities and building resilience becomes paramount. The journey toward effective cyber risk management requires a strategic approach, continuous innovation, and a commitment to safeguarding patient well-being.
With MetricStream CyberGRC, your organization can:
- Gain a unified view of cyber risks, compliance, policies, and issues
- Automate cyber risk and compliance management
- Accurately quantify cyber risk exposure in monetary terms
- Efficiently monitor and remediate threats and vulnerabilities
- Streamline third-party risk management from onboarding to offboarding
- Harmonize controls across multiple standards and frameworks
- Enable continuous control monitoring for improved compliance and security
- Simplify cyber policy creation, attestation, roll-out, and monitoring
Our latest eBook explores these questions and provides comprehensive insights to guide healthcare organizations toward a more secure future.
For a more detailed perspective on this topic, download our eBook:
Building Business Value for and with Your IT GRC Program
- IT Risk & Cyber Risk
- 07 February 24

Introduction
IT Governance, Risk, and Compliance (GRC) management is becoming increasingly integrated across a wide and expanding set of use cases, including IT risk management, IT compliance, policy management, threat and vulnerability management, IT third-party vendor risk management, and more. The core promise of an IT GRC program that integrates needs across all stakeholders is the efficient management of risk against business objectives and better business performance amid an evolving threat landscape, technological and business developments, and regulatory changes; all of which can lead organizations to thrive on risk.
While many organizations have seen benefits from their IT GRC investments, it is critical to build a case for the business value of IT GRC, in order to a) understand the true impact of the GRC program against investments made into it and b) gain enterprise-wide commitment supporting the implementation of a high-value, sustainable IT GRC program. It all comes down to one point – leveraging risk information efficiently to achieve business outcomes.
Experience shows us that those organizations that manage IT GRC as an integrated program involving people, processes, and technologies are more successful in delivering value to their organizations, compared to those that simply focus on deploying technology or processes without accounting for the larger picture. Not only does an effective, integrated IT GRC program strengthen IT risk, governance, and compliance management, but it also aligns these processes with the larger enterprise governance framework.
Understanding IT GRC Business Value
Business value is the measure of a program’s qualitative and quantitative benefits, as well as other intangible expected benefits, such as improved decision-making through better analytics. Together, these values provide a complete picture of how business performance can improve over the long run through a portfolio of initiatives.
The business value can be realized at two levels through an integrated IT GRC program:
- Integrated IT GRC across the organization – Benefits include risk-based decision-making translating to efficient risk management, higher efficiencies in operations, and improved governance and decision-making
- IT GRC within a domain – Benefits include the implementation of upgraded process and technology improvements in domains such as IT risk management, IT compliance management, policy management, threat and vulnerability management, and third-party management, which enable the domain to move away from inefficient and error-prone manual, offline methods.
It’s important to remember that any business value derived from an IT GRC program, is ongoing and continuously improving – it accrues over the years with substantial returns stacking up as the adoption of the IT GRC program grows, and as processes are continuously improved. Only when benefits are realized can the initial value proposition of the IT GRC program be achieved, but also perhaps exceeded. As these benefits become “business as usual,” new initiatives and continuous improvements will drive constant upward revisions to the overall value equation.
Benefits of an Automated and Integrated IT GRC
Let’s understand this with the help of an example.
Consider an organization’s IT risk management team of 12 people that is not able to complete risk assessments at the required depth due to the lack of time and resources. Management reporting is difficult and incomplete with only a few metrics and, occasionally, with errors that take time to be hunted down and resolved.
Let’s assume that 400 risk assessments need to be performed in the organization; of which only 200 are currently being completed with a team of 12. It can be implied that the organization can achieve the goal of performing 400 risk assessments if it increases its team size by 100%, from 12 to 24.
Further, assuming the average time to complete an assessment is 10 days, 400 assessments will be completed in 4,000 days. But, assuming 200 working days per year, the total number of team annual days is 2,400 (for a 12-member team) for 200 assessments and 4,800 (for a 24-member team) for 400 assessments.
Also, from the budget standpoint, assuming the average time to complete an assessment is 10 days and the fully loaded cost is $400 per day, the total cost of 200 assessments with a 12-member team will be $400*10*200*12 = $96,00,000.
Considering the organization can increase the team size to 24, the total cost of 400 assessments would be $400*10*400*24 = $3,84,00,000.
This, however, is not realistic. An organization will not have infinite human and financial resources to continue scaling up the team and assessments to meet the growing demand, especially if it is using manual methods, spreadsheets, and emails to perform the risk assessments. What is needed is to lower the average cost per assessment and improve the efficiency of the current team by automating the process.
Improved Efficiency with IT GRC
Implementing an integrated IT GRC solution, such as MetricStream CyberGRC, can help achieve this goal. Based on MetricStream’s customer feedback and business value calculator, an organization can achieve a 66% reduction in the time taken to complete risk assessment. This is mainly attributable to:
- Use of automation to consolidate and continuously update regulations/frameworks to ensure compliance requirements are always accurate and up to date
- Use of automation in use cases such as continuous compliance, incident management, threat/vulnerability identification, and escalation, to improve the time taken per task/event
- Consolidation of threats, vulnerabilities, and controls across all risk vectors to be able to receive a wholesome picture of outstanding risks
- Effectively connecting the dots between risk, compliance, policy, and third-party risk management, where incidents/issues arising in any one stream, can be viewed as a whole, the impact assessed collaboratively, and the availability of analytics which translates to better decision-making
In the above example, where the average time to complete an assessment is 10 days and the fully loaded cost is $400 per day, the organization can
- Reduce the time to complete an assessment to 3.4 days (a 70% reduction)
- Complete 400 assessments in 1,360 days and with $400*3.4*400*12 = $65,28,000, i.e., at 90% reduced cost without the need to increase the number of team members
In this example, factors such as travel expenses, errors and remediation efforts, financial losses due to fines/failures, etc. have not been taken into account. So, realistically, the cost would be much more than calculated here.
Of course, there will be costs associated with an IT GRC solution as well, such as consulting fees, people costs, technology implementation costs, and ongoing direct costs for cloud services. If the deployment is internal, the team can consider additional hardware and infrastructure costs, as well as support and maintenance costs.
But the payoff is significant. By building an integrated IT GRC program with supporting frameworks, processes, governance, information architecture, and working groups, organizations can achieve better business performance as we can see above.
IT GRC implementation is a journey that can span several months with multiple tracks/initiatives and stakeholders. It’s important to regularly review the implementation plan/roadmap and maintain a living document that demonstrates the benefits that have been realized as each initiative is launched and fully adopted.
How MetricStream CyberGRC Can Help
MetricStream CyberGRC helps organizations implement and elevate their IT GRC program with automated and autonomous capabilities, integrated approach, and advanced risk quantification and analytics. It offers several benefits:
- Significant time and cost savings and reduction in errors
- More bandwidth for the team, enabling them to focus on other high-priority areas
- 360-degree view of risk and compliance posture, risk relationships, and impact
- Effective reporting and communication of key metrics with stakeholders, regulators, and customers
- Ability to scale as per evolving business requirements
Interested in learning more? Request a personalised demo now!
Empower Your Board with Cyber Risk Metrics That Matter
- IT Risk & Cyber Risk
- 22 January 24

Introduction
The roles and responsibilities of the board of directors (boards) in ensuring the security of their organizations is expanding – both due to the increasing perilousness of the cyber risk and threat landscape and as the result of new regulatory requirements.
Boards today are interested not only in the business side of it, for example, knowing the return on investment in cyber risk management activities, but also in the technology side of it – the IT infrastructure comprising of on-premises and cloud-based assets, networks, applications, and resources, the third-party ecosystem, the cyber defense and resilience mechanism including the control environment and security measures in place, and more.
The onus to effectively communicate the security and risk-related information to the board and the C-suite in a timely and lucid manner primarily falls on the CISO. Although there is a blossoming trend of appointing Business Information Security Officers (BISOs), the key responsibilities still lie firmly with the CISO. Since boards majorly consist of non-technical executives, it is essential that this risk information is conveyed in easy-to-understand, business-oriented language, which may enable them to first, understand the true potential of risks and their impact, and second, to be able to make strategic decisions that can keep the organization protected while managing budget and resource constraints.
Lack of effective communication not only leads to insufficient or inappropriate action, but may also lead to conflicts and reputational issues and exposes the organization to higher risks. It is imperative for CISOs to choose the relevant and essential metrics to report on, which can aid in fulfilling the above requirements.
What Cyber Risk and Compliance Metrics Should be Reported to the Board?
Cyber risk and IT compliance metrics are essential not only to gauge the effectiveness of an organization’s cyber governance, risk, and compliance (Cyber GRC) strategy and program, but also to manage and effectively communicate risks to the board. They are also critical indicators of overall status, unresolved issues, and potential risk events that can adversely impact organizations.
The CISO and security team measure and track a plethora of such metrics – risk appetite and tolerance, security incidents, configurations, mean time to detect, control maturity, business continuity planning and impact analysis, employee awareness, frequency of training programs, and many more. When reporting these to the board, the CISO should be clear about the objectives behind the reporting. Since the board is responsible for implementing strategies that drive business value, they must receive and review the cyber metrics in a manner that helps them in this process.
Which brings us to the question – what information should the board be made aware of?
The most common and obvious answer is, of course, understanding the security and compliance posture. However, there are several other aspects too.
First, there is no one-size-fits-all metrics reporting template. Understanding the information sensitivity, domain, sector, size, culture, and resources of the organization should be the foundation of all such metrics reporting. As an example, the nature of data being handled, the regions being operated in, the regulations in those regions, and so on will affect the kind of metrics being reported to the board.
Further, the metrics will depend on the ecosystem of the organization. For example, if a company were to scale its operations by engaging a network of third parties, then metrics concerning such third-party activity and their SLAs must also find prominence in any reports to the board.
In another scenario, say, if a company were downsizing and facing budget cuts, the decision-makers would want to know the best way to do so without impacting the overall security posture. This would require looking at metrics such as IT team headcount, productivity, use of AI technology, IT vendors, spending on cyber projects, etc.
Another aspect to consider is the purpose of the report. There are regular review processes that help to determine the cybersecurity strategy, budget, and program. This involves metrics such as the number of security incidents in a year, the total number of critical assets, top risks, threats, and vulnerabilities, the number of access control violations, control maturity practice score, the number of critical and non-critical third parties, mean time to respond to security incidents, total third-party spend, compliance status, number of open issues, and many more. Then there are particular use-case reports such as detailing an incident or planning for a corporate acquisition/merger or entering a new line of business. In these cases, different types of reports with specific metrics need to be reported on and this should be in addition to (and not instead of) the regular reports.
How to Report – Too Many Metrics Are Not Good!
Keeping it simple always works best. Not all board members will have the technical expertise to understand the relevance or criticality of every metric that is being reported. It is therefore crucial to report the metrics in terms that anyone can interpret and understand. For example, in addition to presenting them with the risk assessment matrix, color-coded for depicting high, medium, and low risk, communicate the risk exposure in monetary or dollar terms using risk quantification.
Another best practice is to segregate the metrics into different categories, such as
- Security – detected intrusion attempts, number and severity of security incidents, time to resolve, vulnerabilities assessment results, control effectiveness, etc.
- Financial – risk appetite and tolerance, risk exposure, cost of security incidents, cybersecurity insurance, cost vs budget, etc.
- Compliance – relevant regulations, frameworks, and standards, compliance status, control effectiveness (control testing results), new regulatory requirements and obligations, volume and type of data in possession,
- Third Parties – critical and non-critical third parties, third-party scoring/rating, third-party cyber risks, compliance with SLAs, third-party incident response, etc.
- Cyber Resilience – business continuity planning, tabletop exercises, impact analysis, response and recovery, etc.
- Employee Awareness – policy adherence, training, workshops, etc.
One of the best ways to communicate technical information to non-technical people is to use analogies. As an extremely simplified example, instead of trying to highlight the benefits of ECC encryption over RSA, one can simply portray it as ECC having a 12-lever lock versus RSA, which has a 6-lever lock. The use of real-world examples can go a long way in ensuring board understanding and makes the most fact-based decisions.
Regulatory Mandates on the Board’s Role
Regulations around cybersecurity and cyber risk management are increasing quickly. In recent months, we saw the adoption of the SEC’s cybersecurity rules in the US, following the introduction of the Digital Operational Resilience Act (DORA) in the EU, to be fully adopted by 2025.
The SEC’s rules require annual reporting on the board’s oversight of cybersecurity risks, the management’s role and expertise in assessing and managing material cybersecurity risks, as well as how the board/subcommittee is informed about cyber risks. The rules, set to come into force in December 2023, are applicable to publicly-listed organizations.
For a deeper dive, read our recent blog, Achieve Compliance with SEC’s New Cybersecurity Rules.
EU’s DORA was enforced on January 16, 2023 and financial sector organizations will be required to be compliant by January 17, 2025. The act mandates the “management body” of financial entities to define, approve, oversee, and be responsible for the implementation of all arrangements related to the information and communication technology (ICT) risk management framework.
To learn more about this new regulation, download our eBook, Demystifying DORA - Understanding and Preparing for the EU’s Digital Operational Resilience Act.
The Way Forward
Given the fast pace at which the cyber risk landscape is evolving, the board’s role and interest in cyber risk management will only grow. For CISOs and security teams, this will require presenting a clear, simple, and accurate picture of the Cyber GRC program. Additionally, it requires effective collaboration and regular communication between the board and the CISO to make the reporting process meaningful, streamlined, and aligned with business goals and objectives. This requires time and effort from both sides, and the best time to start is now.
To learn how MetricStream can help with cyber metrics reporting to the board, contact us today!
Navigating 2024: Top Cyber Risk Trends That Must Be on Your Radar
- IT Risk & Cyber Risk
- 06 December 23

Introduction
It has become trite to say that cyber risks are evolving at a fast pace or that it has become a top area of concern for organizations. Businesses today are required to navigate not just the digital era but the era of cognitive intelligence and generative AI (GenAI). While these technological advancements are helping organizations significantly improve their cyber risk management and gain process efficiencies, the easy access to these tools has made them a favorite among bad actors and cyber adversaries who can use them as easily to plan and launch sophisticated attacks with far-reaching consequences.
The best cyber risk management strategy is to ensure that innovation and security measures go hand in hand. But in practice, it is not so. In an IBM survey, while 94% of CEOs said that it is important to secure AI solutions before their implementation, 69% said that innovation takes precedence over cybersecurity for GenAI.
While AI is on everyone’s mind as we step into 2024, what are the other cyber risks that organizations need to prepare for? Before we get to that, here’s a quick recap of the major happenings from 2023 for all things cyber.
The Cyber Governance, Risk, and Compliance (Cyber GRC) Whirlwind in 2023
One of the most important cyber developments in 2023 was undoubtedly the adoption of the Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure Rules for public companies by the U.S. Securities and Exchange Commission (SEC). Though there are a lot of unanswered questions and “grey” areas regarding determining the “materiality” of a cyber incident or terms like “without unreasonable delay”, it is a landmark regulation nevertheless and a step in the right direction.
For deeper insights into the new rules, you can read my previous blog “Achieve Compliance with SEC’s New Cybersecurity Rules” or leave a comment below to let us know your thoughts.
With AI implementation gathering steam across sectors, the National Institute of Standards and Technology (NIST) released the AI Risk Management Framework in January 2023. The framework is intended to “improve the ability to incorporate trustworthiness considerations into the design, development, use, and evaluation of AI products, services, and systems.”
We also saw the Digital Operational Resilience Act (DORA) being enacted in the European Union on 16 January 2023. EU-based financial sector organizations will be required to demonstrate DORA compliance from 17 January 2025. Aimed at enhancing the digital operational resilience of financial sector entities, DORA covers key areas including ICT risk management, ICT-related incident management and reporting, digital operational resilience testing, the management of ICT third-party risk, and cyber threat information sharing.
Our eBook “Demystifying DORA: Understanding and Preparing for the EU’s Digital Operational Resilience Act” discusses various aspects and requirements of DORA in detail.
Throughout the year organizations around the world also faced a growing number of cyber attacks and data breaches. Some of the major ones include the hack of MOVEit which affected over 1000 organizations and the personal data of at least 60 million individuals, the distributed denial of service (DDoS) attacks on a number of banks across Italy, ransomware attack on entertainment company MGM Resorts which led to operational disruptions, uncovering of a 38 terabyte data leak at Microsoft that happened in 2020, data breach at the Indian Council of Medical Research (ICMR) which exposed the personal data of 815 million Indian residents, and many more.
What to Expect in 2024?
It goes without saying that the cyber risks will increase in number, sophistication, and severity. Here are some of the top Cyber GRC trends for 2024:
- Heightened Business and Regulatory Focus on AI
The overall trend of AI and GenAI innovation is expected to continue and gain more momentum in 2024 with competition becoming fiercer and regulators worldwide rolling out AI-focused regulations and frameworks in an attempt to ensure that innovation is supported by effective security and governance measures. - Automated and Continuous Approach to Cyber GRC
Specifically in the field of Cyber GRC, more and more organizations are expected to embrace automation for risk and compliance management processes and AI-powered predictive analytics to navigate the rapidly intensifying cyber risk and regulatory landscape. This includes capabilities to perform autonomous risk assessments and value-based quantification, continuous control testing with immediate remediations, automated compliance, and more. - Continued Focus on Third-Party Cyber Risks
Third-party cyber risk management will also be a core focus area of CISOs and security teams with growing digital dependencies of organizations on SaaS solution providers, cloud service providers, and technology providers, among other third parties in the ecosystem. 2023 saw continued trend of exploiting third parties to gain access to target organizations. Proactively identifying the potentially vulnerable areas, points of failure, and blind spots throughout the third-party risk management life cycle has become more important than ever as can also be evidenced by the introduction of strict regulations to govern their activities. - Increased Cybersecurity Investments
Given the growing frequency, scale, and sophistication of cyber attacks, organizations will be significantly ramping up their cybersecurity and risk management investments. Gartner estimates global spending on security and risk management to reach $215 billion in 2024, making it a 14.3% increase from 2023.
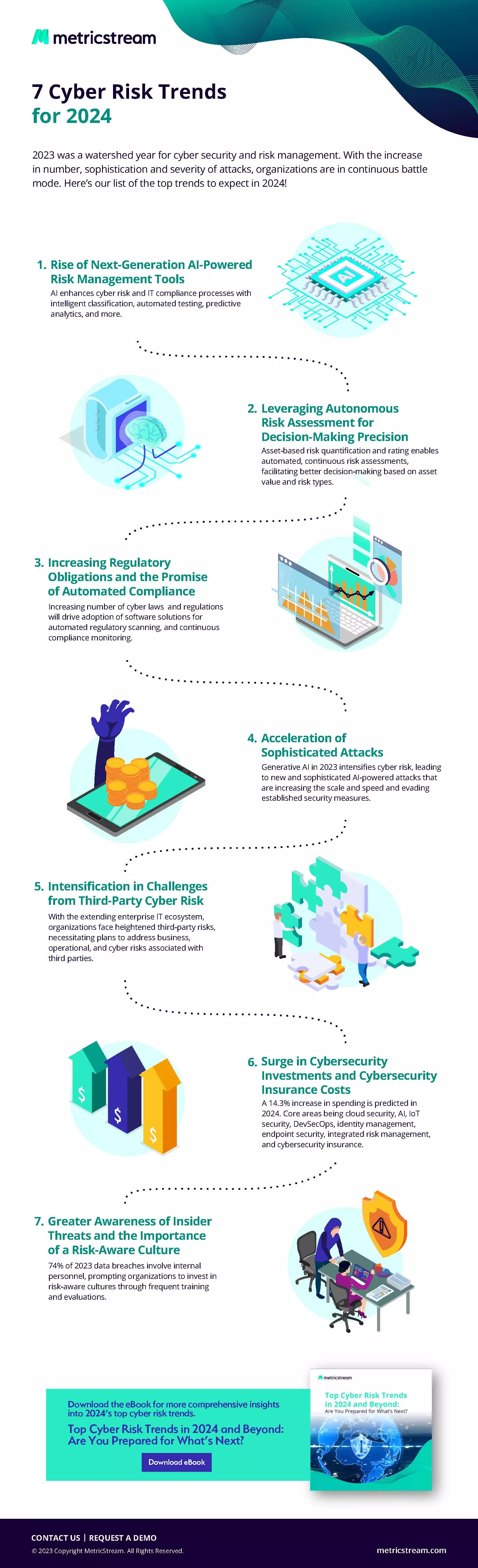
With this background and while the future can be uncertain, we’ve compiled our thoughts on the top 7 cyber risk trends that organizations need to be aware of and prepare for in 2024. Check out our infographic on the top 7 cyber risk trends, which discusses these trends, what to expect, and how to prepare in more detail.
Download now: Top Cyber Risk Trends in 2024 and Beyond
Getting the Cyber Defenses Up
We at MetricStream are hard at work to help organizations stay one step ahead of cyber risks. 2023, in particular, has been a milestone year as we rolled out a number of solutions and capabilities to help organizations drive an effective Cyber GRC strategy. These include:
- AiSPIRE, the industry’s first AI-powered, knowledge-centric GRC, which continuously senses and identifies risk, audit, and control deficiencies, duplicate risks and controls, patterns of over and under-testing of controls, and enables proactive planning and prioritization of risk assessments, control testing, issue, and action planning.
- Autonomous Control Testing which automates control testing across IT compliance controls and reduces risk by assessing controls across the entire population.
- Integration with AWS Audit Manager which simplifies and consolidates IT compliance management through automated control testing and evidence collection of all firm-wide controls, including on-premises and multi-cloud environments.
To explore MetricStream’s cyber risk and IT compliance management capabilities and to prepare for the trends of 2024, request a personalized CyberGRC demo today!