Introduction
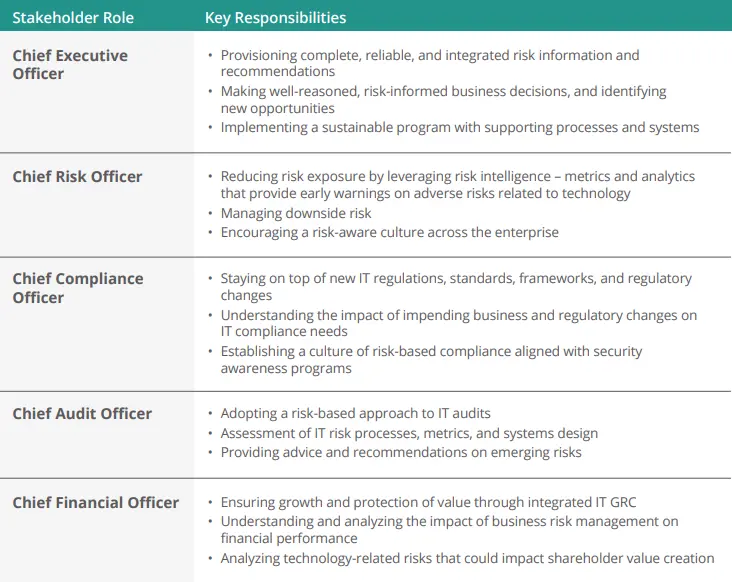
In today’s digital-first enterprises, CISOs, IT risk leaders, and even the Board of Directors, have key roles to play in safeguarding their organizations against fast-growing IT risks and threats, while ensuring compliance with IT regulations, standards, and policies.
As organizations increasingly adopt cloud-based IT ecosystems and mobility solutions, the risks to data security are greater than ever. All it takes is one loophole – an unpatched vulnerability, an unchecked API, a control gap, or an unresolved issue – to bring down the strongest organization. Sometimes, these risks may lie in a third-party vendor’s IT systems, implying that organizations must address their own IT risks and those of their vendors or partners and the extended ecosystem.
At the same time, organizations are under constant pressure to comply with cyber-focused regulatory requirements like the newly introduced SEC Cybersecurity Rules, as well as IT governance standards and frameworks such as the Payment Card Industry Data Security Standard (PCI DSS), COBIT, NIST Cyber Security Framework (CSF), and ISO 27001/2. Furthermore, recent regulatory efforts such as the EU’s Digital Operational Resilience Act (DORA) and Cyber Resilience Act are expected to set a precedent for similar efforts across industries and geographies.
Managing all these requirements the traditional way, using siloed systems and manual processes, is no longer effective or efficient, especially as IT risks, regulations, controls, and related data grow more complex and interconnected. Today’s forward-looking organizations are opting for a more integrated IT Governance, Risk, and Compliance management approach that enables them to bring together all their IT and Cyber GRC processes under one platform.
This eBook is intended to help CISOs, IT risk leaders, and anyone concerned with IT risk, security, and compliance management to understand the key elements of IT GRC, the best practices, the benefits they can expect from an integrated approach, and more. Most important, it will also delve into how they can harness the power of technology and automation to enable the integrated approach to GRC in their organization.
What is IT GRC?
IT GRC (IT Governance, Risk, and Compliance) is an operational and structural strategy that is an integrated and continuos approach to align IT activities with business goals while effectively managing risks and meeting industry regulations.
The combined IT GRC framework is a comprehensive tool to meet the complete range of IT and business objectives. However, it can be quite challenging to implement. Organizations are required to establish organization-wide cyber risk management strategies, conduct risk assessments, keep up with a plethora of compliance regulations, establish controls, and monitor GRC programs, all of which can be a tremendous drain on resources.
At the same time, risk and compliance management efforts must be documented and reported, both to the board and regulators. Quite often, documentation is carried out using emails, spreadsheets, and notepads, which are not only extremely cumbersome and prone to errors but also fail to provide a clear picture of the organization’s real-time risk and control status. Even when systems/applications are used, they are usually for a specific use case, which results in a fragmented approach requiring excessive manual effort and leaving room for error.
Given the variety of business processes, locations, and regulatory jurisdictions that companies operate under, a siloed GRC approach has proven to be extremely ineffective. That said, organizations also find it challenging to integrate IT GRC programs across departments and global operations. What then is the solution?
Before we get to that let’s look at the key elements of a comprehensive IT GRC program
Key Elements of an IT GRC Program
IT Risk Management
Organizations need an effective IT risk management program for the assessment, analysis, and monitoring of risks, threats, and vulnerabilities. The objective is to deliver timely, actionable information to help organizations proactively address IT risks in line with corporate objectives.
The risk management program itself is built with various elements such as a centralized library of risks and controls, risk assessments, key risk indicators, and response strategies, all of which must be tailored to suit the risk management requirements and business objectives of the organization. Once the key IT risks are identified and prioritized, organizations can leverage industry standard frameworks to define the appropriate controls. Risk scoring methodologies, what-if analysis, and cyber risk quantification capabilities can further equip risk and security teams to prioritize their response strategies for optimal risk/reward outcomes.
IT Compliance Management
In essence, organizations need an integrated approach to manage compliance with multiple IT regulations and frameworks/standards, regularly scan the regulatory horizon to capture relevant updates, and streamline compliance testing, documentation, evidence collection, control evaluation, and reporting.
A well-defined compliance assessment process aids in ensuring the effectiveness of controls implemented. Once compliance issues and deficiencies are identified and documented, organizations can investigate their root cause and take appropriate remediation measures. Compliance assessment results also enable IT audit groups to quickly and easily show external auditors that a specific compliance requirement is being met and that controls are in place.
IT Third-Party Vendor Risk Management
A robust IT Third-Party Risk Management program that governs the evaluation and selection of IT vendors, policies and contracts, risk assessments, due diligence, monitoring, and risk mitigation, is essential for today’s modern enterprise.
A program that helps establish a common reference point for managing, monitoring, and mitigating firm-wide IT vendor risks can help simplify the process. It should support workflows for vendor onboarding, risk profiling, and due diligence, as well as ongoing vendor risk assessments, monitoring, and oversight. It should also help maintain a central vendor information repository that efficiently logs and tracks all IT vendors and the associated assets, enabling organizations to better identify and understand their IT vendor risks and dependencies.
Traditionally, organizations conducted self-assessments, risk assessments, and audits for evaluating IT vendors. However, given the growing number of cyber incidents via third parties, organizations are also leveraging real-time insights from third-party risk intelligence providers on various risks including IT, cybersecurity, data privacy, reputation, financial, corruption, sustainability, and more.
IT Policy Management
Effective creation, maintenance, compliance, and communication of IT policies across the enterprise is critical for creating awareness about policy requirements and ensuring that safeguards are in place for robust IT governance. A comprehensive IT Policy Management program includes several steps – policy creation, review and approval, distribution, acceptance, implementation, and exception management.
It is important to map the IT policies to regulations and standards, risks, and controls to understand their relationship and impact. For example, understanding how a regulatory change would impact related policies, risks, and controls. Maintaining a centralized repository allows easy storage and management of all policy documents and establishes these linkages. It also ensures that a complete revision history is maintained.
Threat and Vulnerability Management
A proactive approach to identifying and addressing threats and vulnerabilities is essential for today’s digital-first organizations. To make the process efficient, organizations need to use various tools and establish systematic workflows between them for capturing and aggregating threat and vulnerability data in a unified system, which can then be assessed, prioritized, and remediated. It is important to also map the threat and vulnerability data to assets, areas of compliance, and related business processes to identify risk exposures from a business impact perspective.
IT Audit Management
Organizations need to conduct regular IT audits for effective visibility into program implementation and control effectiveness to ensure the program's goal is achieved. Proper measures should be implemented to enable the auditors to record qualitative or quantitative findings along with detailed observations and recommendations. As soon as auditing is completed, audit findings, observation reports, and auditor recommendations should be routed to the appropriate personnel for review and subsequent action.
Incident Management
With cyber incidents, such as breaches, ransomware attacks, phishing, distributed denial of service (DDoS) attacks, etc. on the rise, the need for a robust incident management program is paramount. Incident management consists of measures to identify, evaluate, and resolve critical incidents that can be detrimental to an organization.
A well-defined incident management program is also central to an organization’s cyber resilience strategy. In addition to recording, triaging, routing, investigating, tracking, and closure of incidents, organizations are also focused on measures to ensure quick recovery and continuity of critical business operations as per defined SLAs.
Toward that goal, creating an incident response playbook is crucial. Identifying key personnel for incident response, defining their roles and responsibilities, and outlining the corrective actions based on what-if analysis, can help strengthen organizational readiness and reduce the severity of impact.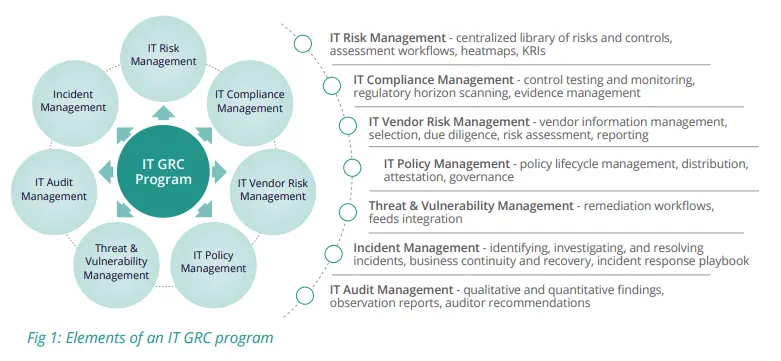
Top IT GRC Challenges
Embarking on the IT GRC journey typically starts with:
Some of the common challenges faced on this journey are:
Lack of Real-Time Visibility
Organizations are facing an increasing number of IT and cyber risks, supply chain attacks, and data breaches. Many organizations still rely on spreadsheets and email-based processes that are not only time-intensive and prone to errors, but also not connected to each other or continuous in their approach. This approach fails to provide real-time visibility into the fast-evolving, high-velocity IT risks, which hampers effective decision-making.
Duplication of Efforts
There are often significant overlaps between the various assessments, functions, and controls, among others. IT risk and compliance teams spend too much time sifting through these duplications instead of forward-looking activities. This results in time waste, high costs associated with meeting overlapping certification and reporting requirements, and employee fatigue due to repeated requests for similar information.
Lack of Understanding of Risk Relationships and Impact
Relying on the manual approach or point solutions for managing IT risk, compliance, audit, and other processes fails to provide insights into the interconnectedness of risks and their relationship with IT assets, controls, regulatory requirements, etc. The result is a highly disjointed view of the IT GRC posture, which is difficult to interpret and understand. The challenges are further exacerbated by the lack of a common IT GRC taxonomy, which makes data aggregation and normalization a daunting task.
Wrong Choice of IT GRC Solution
It is crucial to choose the “right” solution to ensure the success of the IT GRC program. Traditional software solutions may not be aligned with today’s dynamic enterprises that want real-time and comprehensive visibility, cross-team seamless collaboration, scalability, and automated and autonomous processes. For example, organizations today are seeking solutions that not only harmonize controls across multiple IT frameworks and standards but also provide insights into control gaps and weaknesses, patterns of over-testing and under-testing of controls, and more.
Lack of the Right Mindset and Culture
Certain types of organizations often don’t give importance to creating and encouraging the right culture required for an effective and successful IT GRC program. This could include perception of risk management practices (often referred to as a “burden”), training and awareness, “tone from the top”, and resistance to change, among many others. It is important to ensure employees understand their role in IT and cyber risk management and follow general IT security policies while security and system admin teams have to know with certainty which procedures to follow.
IT GRC Best Practices
When preparing to implement an IT GRC program, a key consideration is “time to value” – How long will it take for an organization to realize the benefits of the program, given the maturity of current processes and the effort required to make changes to people, processes, and technology?
Here are some key considerations to keep in mind to accelerate time to value while launching an IT GRC program:
Creating a Well-Defined Strategy
Developing a well-defined plan is the first and the most crucial step. It is important to carefully lay out the launch and execution plan so that the IT GRC program begins on a strong foundation and delivers early successes that help ensure continued support and commitment to the program.
Defining Vision and Objectives
CISOs and IT risk leaders, along with stakeholders from teams such as Risk, Compliance, and Operations, start the process by understanding the current state and maturity level and determining the desired state. While it is desirable to have everything covered in detail, this may not always be practical, and therefore, emphasis must be put on available resources and the critical business functions and objectives. This is essential for defining the program objectives, such as improving process efficiencies, enhancing risk visibility and preparedness, reducing risk exposure, ensuring and maintaining compliance, etc. A successful IT GRC program is one that is closely aligned with the strategic objectives of the organization.
Scoping IT GRC Processes
CISOs engage with various stakeholders to determine the scope of both the program and the personnel. Scoping the program involves identifying the IT GRC process areas (e.g., IT risk management, IT compliance, third parties) that will be impacted by the business operations. Scoping the personnel involves identifying the right stakeholders across risk, ethics and compliance, audit, legal, operations, IT, and security who will be involved in program execution.
Determining Priorities
Once the scope is decided, the next step is to set the program priorities. This will depend on a number of factors, such as the organizational risk profile, risk tolerance and appetite, maturity of existing processes, and readiness for organizational change, among others.
Again, while it would be ideal to cover every single risk, practical constraints dictate that CISOs and IT risk leaders need to engage in and lead conversations with various stakeholders to build out detailed priorities and goals for the IT GRC program, and to develop and drive a sustainable, cross-functional set of initiatives. Creating detailed risk registers of assets, processes, and personnel, rating risks on their severity, and then planning for each group is usually the best way to proceed. They must also gain consensus from the right set of stakeholders on what will be required to close the gap between current and desired future states.
Building the IT GRC Program Roadmap
Using the program priorities, CISOs and IT risk leaders develop a detailed roadmap that includes high-level estimates of effort, cost/benefit projections, and project timelines.
The roadmap may have multiple tracks spanning several months, and each of those tracks may yield different benefits. Every track will have its own project dependencies, goals and objectives, and critical milestones. Moreover, the roadmap itself may evolve over time, requiring prioritizing and deprioritizing and addition/removal of initiatives. Organizations should also factor in the need to onboard new stakeholders into governance and working groups with each new initiative.
Most important, CISOs and IT risk leaders should include evaluating software solutions in the roadmap and leave room for innovation. They should also build in enough time to ensure user adoption of the new solution and incorporate a review plan to ensure the solution delivers results as expected.Finding and Implementing the “Right” Technology Solution
Given the plethora of software solutions available in the market today, an organization needs to carefully evaluate and select the solution that is aligned with its IT GRC program goals and objectives. Analyst reports from independent research firms are a good starting point to shortlist potential software vendors.
CISOs and IT risk leaders need to ask the key questions to the vendors to arrive at a decision, such as:- Which IT regulations and industry standards are supported? How do these map to my needs?
- How can the solution help us reduce our risk exposure? Does it support cyber risk quantification?
- How can the solution help with regulatory and board reporting?
- How long will it take to get the solution up and running?
- How are onboarding, training, and support handled?
- What is the future roadmap of the solution to ensure it is aligned with the organization’s plans?
- Does the solution allow integration with external sources such as vulnerability scanners, threat intelligence providers, etc.?
Click here to learn more about choosing the right GRC solution.
Involving Key Personnel with Clear Roles and Responsibilities
Integrated IT GRC requires teamwork. Organizations need to identify key stakeholders for executing the IT GRC program across business functions, assign clear roles and responsibilities, and define accountabilities. It is important to establish the right governance model for the program with the required executive commitment to make it a success. Also, CISOs and IT risk leaders should regularly communicate the progress to stakeholders and enable continuous improvements as the IT GRC program evolves.

Continuous Reviewing and Monitoring
IT GRC program execution is a journey. Starting with the consolidation of efforts around priority initiatives such as IT risk management and regulatory compliance, it then grows to include new stakeholders and use cases. It requires regular monitoring, review, and recalibration to ensure various initiatives are on track. Leveraging industry best practices and learning from the experiences of peers help to continually improve the program and ensure success along the journey.
Successfully executing an IT GRC program takes hard work, focus, and teamwork. But the payoff can be significant. Implementing a comprehensive IT GRC program with an integrated framework, structured processes, effective governance, robust information architecture, and specialized working groups can help organizations achieve better business performance.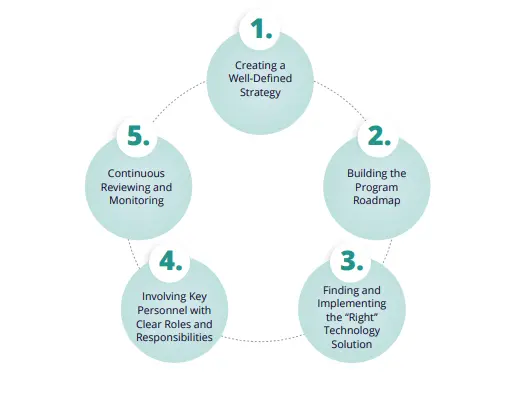
Benefits of an Integrated IT GRC Program
For most CISOs and IT risk leaders, the commitment to an integrated IT GRC program is based on the following main benefits:
Lower Risk
An integrated IT GRC program enables organizations to reduce risk exposure by providing visibility and contextual information on IT and cyber risks across all business units – as well as external risks around third parties.
Interconnectedness and Impact
The integrated approach helps to understand the interconnectedness of risks and their impact on assets, processes, and business functions; the impact of regulatory changes on policies, controls, processes, and so on. Understanding these interrelationships is important to get a 360-degree view of the IT GRC posture and make well-informed business decisions.
Higher Efficiency, Lower Costs
Organizations gain efficiencies and reduce costs by managing IT GRC as a program that leverages an integrated IT risk and control framework, collaborative approach, and overall consistent methodology.
Effective Governance and Reporting
An effective IT GRC program also helps deliver the right information to the right people at the right time. A common classification and reporting framework supports a clear understanding of the information and analytics required for the board, regulators, leadership, and external or internal stakeholders, helping them make decisions that improve business performance.
Elevate Your IT GRC Program with MetricStream CyberGRC
MetricStream enables organizations to overcome IT GRC challenges with its industry-leading CyberGRC solution. All aspects of IT governance, risk, and compliance can be coordinated across the enterprise using MetricStream’s single, centralized GRC platform. This integrative approach enables organizations to align IT GRC and corporate GRC management for best results. Powerful capabilities like cyber risk quantification, continuous control monitoring, AI-based issue management and action plan recommendation, and more, further simplify the process and ensure efficiency and effectiveness.
The solution uniquely combines software and regulatory content for effective and sustainable compliance through embedded best-practice templates, regulatory notifications, and industry alerts. Essentially, it provides end-to-end capabilities for streamlined, integrated, and automated IT GRC management.
With MetricStream CyberGRC, you can: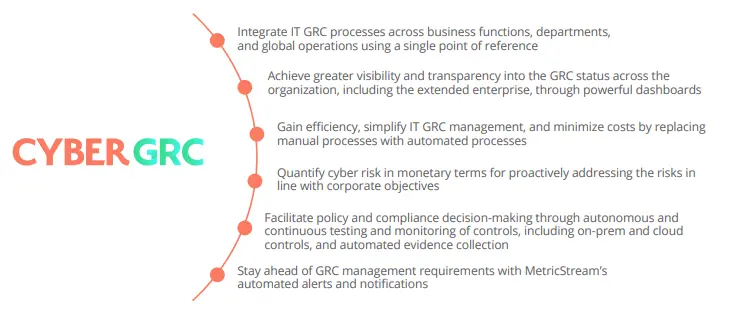
In today’s digital-first enterprises, CISOs, IT risk leaders, and even the Board of Directors, have key roles to play in safeguarding their organizations against fast-growing IT risks and threats, while ensuring compliance with IT regulations, standards, and policies.
As organizations increasingly adopt cloud-based IT ecosystems and mobility solutions, the risks to data security are greater than ever. All it takes is one loophole – an unpatched vulnerability, an unchecked API, a control gap, or an unresolved issue – to bring down the strongest organization. Sometimes, these risks may lie in a third-party vendor’s IT systems, implying that organizations must address their own IT risks and those of their vendors or partners and the extended ecosystem.
At the same time, organizations are under constant pressure to comply with cyber-focused regulatory requirements like the newly introduced SEC Cybersecurity Rules, as well as IT governance standards and frameworks such as the Payment Card Industry Data Security Standard (PCI DSS), COBIT, NIST Cyber Security Framework (CSF), and ISO 27001/2. Furthermore, recent regulatory efforts such as the EU’s Digital Operational Resilience Act (DORA) and Cyber Resilience Act are expected to set a precedent for similar efforts across industries and geographies.
Managing all these requirements the traditional way, using siloed systems and manual processes, is no longer effective or efficient, especially as IT risks, regulations, controls, and related data grow more complex and interconnected. Today’s forward-looking organizations are opting for a more integrated IT Governance, Risk, and Compliance management approach that enables them to bring together all their IT and Cyber GRC processes under one platform.
This eBook is intended to help CISOs, IT risk leaders, and anyone concerned with IT risk, security, and compliance management to understand the key elements of IT GRC, the best practices, the benefits they can expect from an integrated approach, and more. Most important, it will also delve into how they can harness the power of technology and automation to enable the integrated approach to GRC in their organization.
IT GRC (IT Governance, Risk, and Compliance) is an operational and structural strategy that is an integrated and continuos approach to align IT activities with business goals while effectively managing risks and meeting industry regulations.
The combined IT GRC framework is a comprehensive tool to meet the complete range of IT and business objectives. However, it can be quite challenging to implement. Organizations are required to establish organization-wide cyber risk management strategies, conduct risk assessments, keep up with a plethora of compliance regulations, establish controls, and monitor GRC programs, all of which can be a tremendous drain on resources.
At the same time, risk and compliance management efforts must be documented and reported, both to the board and regulators. Quite often, documentation is carried out using emails, spreadsheets, and notepads, which are not only extremely cumbersome and prone to errors but also fail to provide a clear picture of the organization’s real-time risk and control status. Even when systems/applications are used, they are usually for a specific use case, which results in a fragmented approach requiring excessive manual effort and leaving room for error.
Given the variety of business processes, locations, and regulatory jurisdictions that companies operate under, a siloed GRC approach has proven to be extremely ineffective. That said, organizations also find it challenging to integrate IT GRC programs across departments and global operations. What then is the solution?
Before we get to that let’s look at the key elements of a comprehensive IT GRC program
IT Risk Management
Organizations need an effective IT risk management program for the assessment, analysis, and monitoring of risks, threats, and vulnerabilities. The objective is to deliver timely, actionable information to help organizations proactively address IT risks in line with corporate objectives.
The risk management program itself is built with various elements such as a centralized library of risks and controls, risk assessments, key risk indicators, and response strategies, all of which must be tailored to suit the risk management requirements and business objectives of the organization. Once the key IT risks are identified and prioritized, organizations can leverage industry standard frameworks to define the appropriate controls. Risk scoring methodologies, what-if analysis, and cyber risk quantification capabilities can further equip risk and security teams to prioritize their response strategies for optimal risk/reward outcomes.
IT Compliance Management
In essence, organizations need an integrated approach to manage compliance with multiple IT regulations and frameworks/standards, regularly scan the regulatory horizon to capture relevant updates, and streamline compliance testing, documentation, evidence collection, control evaluation, and reporting.
A well-defined compliance assessment process aids in ensuring the effectiveness of controls implemented. Once compliance issues and deficiencies are identified and documented, organizations can investigate their root cause and take appropriate remediation measures. Compliance assessment results also enable IT audit groups to quickly and easily show external auditors that a specific compliance requirement is being met and that controls are in place.
IT Third-Party Vendor Risk Management
A robust IT Third-Party Risk Management program that governs the evaluation and selection of IT vendors, policies and contracts, risk assessments, due diligence, monitoring, and risk mitigation, is essential for today’s modern enterprise.
A program that helps establish a common reference point for managing, monitoring, and mitigating firm-wide IT vendor risks can help simplify the process. It should support workflows for vendor onboarding, risk profiling, and due diligence, as well as ongoing vendor risk assessments, monitoring, and oversight. It should also help maintain a central vendor information repository that efficiently logs and tracks all IT vendors and the associated assets, enabling organizations to better identify and understand their IT vendor risks and dependencies.
Traditionally, organizations conducted self-assessments, risk assessments, and audits for evaluating IT vendors. However, given the growing number of cyber incidents via third parties, organizations are also leveraging real-time insights from third-party risk intelligence providers on various risks including IT, cybersecurity, data privacy, reputation, financial, corruption, sustainability, and more.
IT Policy Management
Effective creation, maintenance, compliance, and communication of IT policies across the enterprise is critical for creating awareness about policy requirements and ensuring that safeguards are in place for robust IT governance. A comprehensive IT Policy Management program includes several steps – policy creation, review and approval, distribution, acceptance, implementation, and exception management.
It is important to map the IT policies to regulations and standards, risks, and controls to understand their relationship and impact. For example, understanding how a regulatory change would impact related policies, risks, and controls. Maintaining a centralized repository allows easy storage and management of all policy documents and establishes these linkages. It also ensures that a complete revision history is maintained.
Threat and Vulnerability Management
A proactive approach to identifying and addressing threats and vulnerabilities is essential for today’s digital-first organizations. To make the process efficient, organizations need to use various tools and establish systematic workflows between them for capturing and aggregating threat and vulnerability data in a unified system, which can then be assessed, prioritized, and remediated. It is important to also map the threat and vulnerability data to assets, areas of compliance, and related business processes to identify risk exposures from a business impact perspective.
IT Audit Management
Organizations need to conduct regular IT audits for effective visibility into program implementation and control effectiveness to ensure the program's goal is achieved. Proper measures should be implemented to enable the auditors to record qualitative or quantitative findings along with detailed observations and recommendations. As soon as auditing is completed, audit findings, observation reports, and auditor recommendations should be routed to the appropriate personnel for review and subsequent action.
Incident Management
With cyber incidents, such as breaches, ransomware attacks, phishing, distributed denial of service (DDoS) attacks, etc. on the rise, the need for a robust incident management program is paramount. Incident management consists of measures to identify, evaluate, and resolve critical incidents that can be detrimental to an organization.
A well-defined incident management program is also central to an organization’s cyber resilience strategy. In addition to recording, triaging, routing, investigating, tracking, and closure of incidents, organizations are also focused on measures to ensure quick recovery and continuity of critical business operations as per defined SLAs.
Toward that goal, creating an incident response playbook is crucial. Identifying key personnel for incident response, defining their roles and responsibilities, and outlining the corrective actions based on what-if analysis, can help strengthen organizational readiness and reduce the severity of impact.
Embarking on the IT GRC journey typically starts with:
Some of the common challenges faced on this journey are:
Lack of Real-Time Visibility
Organizations are facing an increasing number of IT and cyber risks, supply chain attacks, and data breaches. Many organizations still rely on spreadsheets and email-based processes that are not only time-intensive and prone to errors, but also not connected to each other or continuous in their approach. This approach fails to provide real-time visibility into the fast-evolving, high-velocity IT risks, which hampers effective decision-making.
Duplication of Efforts
There are often significant overlaps between the various assessments, functions, and controls, among others. IT risk and compliance teams spend too much time sifting through these duplications instead of forward-looking activities. This results in time waste, high costs associated with meeting overlapping certification and reporting requirements, and employee fatigue due to repeated requests for similar information.
Lack of Understanding of Risk Relationships and Impact
Relying on the manual approach or point solutions for managing IT risk, compliance, audit, and other processes fails to provide insights into the interconnectedness of risks and their relationship with IT assets, controls, regulatory requirements, etc. The result is a highly disjointed view of the IT GRC posture, which is difficult to interpret and understand. The challenges are further exacerbated by the lack of a common IT GRC taxonomy, which makes data aggregation and normalization a daunting task.
Wrong Choice of IT GRC Solution
It is crucial to choose the “right” solution to ensure the success of the IT GRC program. Traditional software solutions may not be aligned with today’s dynamic enterprises that want real-time and comprehensive visibility, cross-team seamless collaboration, scalability, and automated and autonomous processes. For example, organizations today are seeking solutions that not only harmonize controls across multiple IT frameworks and standards but also provide insights into control gaps and weaknesses, patterns of over-testing and under-testing of controls, and more.
Lack of the Right Mindset and Culture
Certain types of organizations often don’t give importance to creating and encouraging the right culture required for an effective and successful IT GRC program. This could include perception of risk management practices (often referred to as a “burden”), training and awareness, “tone from the top”, and resistance to change, among many others. It is important to ensure employees understand their role in IT and cyber risk management and follow general IT security policies while security and system admin teams have to know with certainty which procedures to follow.
When preparing to implement an IT GRC program, a key consideration is “time to value” – How long will it take for an organization to realize the benefits of the program, given the maturity of current processes and the effort required to make changes to people, processes, and technology?
Here are some key considerations to keep in mind to accelerate time to value while launching an IT GRC program:
Creating a Well-Defined Strategy
Developing a well-defined plan is the first and the most crucial step. It is important to carefully lay out the launch and execution plan so that the IT GRC program begins on a strong foundation and delivers early successes that help ensure continued support and commitment to the program.
Defining Vision and Objectives
CISOs and IT risk leaders, along with stakeholders from teams such as Risk, Compliance, and Operations, start the process by understanding the current state and maturity level and determining the desired state. While it is desirable to have everything covered in detail, this may not always be practical, and therefore, emphasis must be put on available resources and the critical business functions and objectives. This is essential for defining the program objectives, such as improving process efficiencies, enhancing risk visibility and preparedness, reducing risk exposure, ensuring and maintaining compliance, etc. A successful IT GRC program is one that is closely aligned with the strategic objectives of the organization.
Scoping IT GRC Processes
CISOs engage with various stakeholders to determine the scope of both the program and the personnel. Scoping the program involves identifying the IT GRC process areas (e.g., IT risk management, IT compliance, third parties) that will be impacted by the business operations. Scoping the personnel involves identifying the right stakeholders across risk, ethics and compliance, audit, legal, operations, IT, and security who will be involved in program execution.
Determining Priorities
Once the scope is decided, the next step is to set the program priorities. This will depend on a number of factors, such as the organizational risk profile, risk tolerance and appetite, maturity of existing processes, and readiness for organizational change, among others.
Again, while it would be ideal to cover every single risk, practical constraints dictate that CISOs and IT risk leaders need to engage in and lead conversations with various stakeholders to build out detailed priorities and goals for the IT GRC program, and to develop and drive a sustainable, cross-functional set of initiatives. Creating detailed risk registers of assets, processes, and personnel, rating risks on their severity, and then planning for each group is usually the best way to proceed. They must also gain consensus from the right set of stakeholders on what will be required to close the gap between current and desired future states.
Building the IT GRC Program Roadmap
Using the program priorities, CISOs and IT risk leaders develop a detailed roadmap that includes high-level estimates of effort, cost/benefit projections, and project timelines.
The roadmap may have multiple tracks spanning several months, and each of those tracks may yield different benefits. Every track will have its own project dependencies, goals and objectives, and critical milestones. Moreover, the roadmap itself may evolve over time, requiring prioritizing and deprioritizing and addition/removal of initiatives. Organizations should also factor in the need to onboard new stakeholders into governance and working groups with each new initiative.
Most important, CISOs and IT risk leaders should include evaluating software solutions in the roadmap and leave room for innovation. They should also build in enough time to ensure user adoption of the new solution and incorporate a review plan to ensure the solution delivers results as expected.Finding and Implementing the “Right” Technology Solution
Given the plethora of software solutions available in the market today, an organization needs to carefully evaluate and select the solution that is aligned with its IT GRC program goals and objectives. Analyst reports from independent research firms are a good starting point to shortlist potential software vendors.
CISOs and IT risk leaders need to ask the key questions to the vendors to arrive at a decision, such as:- Which IT regulations and industry standards are supported? How do these map to my needs?
- How can the solution help us reduce our risk exposure? Does it support cyber risk quantification?
- How can the solution help with regulatory and board reporting?
- How long will it take to get the solution up and running?
- How are onboarding, training, and support handled?
- What is the future roadmap of the solution to ensure it is aligned with the organization’s plans?
- Does the solution allow integration with external sources such as vulnerability scanners, threat intelligence providers, etc.?
Click here to learn more about choosing the right GRC solution.
Involving Key Personnel with Clear Roles and Responsibilities
Integrated IT GRC requires teamwork. Organizations need to identify key stakeholders for executing the IT GRC program across business functions, assign clear roles and responsibilities, and define accountabilities. It is important to establish the right governance model for the program with the required executive commitment to make it a success. Also, CISOs and IT risk leaders should regularly communicate the progress to stakeholders and enable continuous improvements as the IT GRC program evolves.


Continuous Reviewing and Monitoring
IT GRC program execution is a journey. Starting with the consolidation of efforts around priority initiatives such as IT risk management and regulatory compliance, it then grows to include new stakeholders and use cases. It requires regular monitoring, review, and recalibration to ensure various initiatives are on track. Leveraging industry best practices and learning from the experiences of peers help to continually improve the program and ensure success along the journey.
Successfully executing an IT GRC program takes hard work, focus, and teamwork. But the payoff can be significant. Implementing a comprehensive IT GRC program with an integrated framework, structured processes, effective governance, robust information architecture, and specialized working groups can help organizations achieve better business performance.
For most CISOs and IT risk leaders, the commitment to an integrated IT GRC program is based on the following main benefits:
Lower Risk
An integrated IT GRC program enables organizations to reduce risk exposure by providing visibility and contextual information on IT and cyber risks across all business units – as well as external risks around third parties.
Interconnectedness and Impact
The integrated approach helps to understand the interconnectedness of risks and their impact on assets, processes, and business functions; the impact of regulatory changes on policies, controls, processes, and so on. Understanding these interrelationships is important to get a 360-degree view of the IT GRC posture and make well-informed business decisions.
Higher Efficiency, Lower Costs
Organizations gain efficiencies and reduce costs by managing IT GRC as a program that leverages an integrated IT risk and control framework, collaborative approach, and overall consistent methodology.
Effective Governance and Reporting
An effective IT GRC program also helps deliver the right information to the right people at the right time. A common classification and reporting framework supports a clear understanding of the information and analytics required for the board, regulators, leadership, and external or internal stakeholders, helping them make decisions that improve business performance.
MetricStream enables organizations to overcome IT GRC challenges with its industry-leading CyberGRC solution. All aspects of IT governance, risk, and compliance can be coordinated across the enterprise using MetricStream’s single, centralized GRC platform. This integrative approach enables organizations to align IT GRC and corporate GRC management for best results. Powerful capabilities like cyber risk quantification, continuous control monitoring, AI-based issue management and action plan recommendation, and more, further simplify the process and ensure efficiency and effectiveness.
The solution uniquely combines software and regulatory content for effective and sustainable compliance through embedded best-practice templates, regulatory notifications, and industry alerts. Essentially, it provides end-to-end capabilities for streamlined, integrated, and automated IT GRC management.
With MetricStream CyberGRC, you can:








