Introduction
It’s a whole new world for managing cyber risk – and the stakes are higher than ever.
According to the Cost of Data Breach Report 2021 by the Ponemon Institute, the average cost of a data breach was $4.24 million in 2021, up from $3.86 million in 2019. Even more surprising, the average breach cost was $1.07 million higher where remote working was a factor. The 2022 report records the highest global cost increase to $4.35 4.35 million, which is a 12.7% increase from the previous year.
As digitization has escalated, cyber adversaries have become increasingly sophisticated and organized to exploit vulnerabilities and carry out damaging attacks.
What’s more, the challenges have gotten significantly worse over the past two years as the pandemic brought a tectonic shift in how businesses operate. The sudden shift to remote work beyond office firewalls and enterprise security mechanisms expanded the attack surface of organizations and made them more vulnerable to breaches.
Industry 4.0 and Cybersecurity
To quickly adapt to the new normal, organizations rushed to adopt industry 4.0 technologies, such as cloud computing, artificial intelligence, and automated bots. While these technologies help to automate various processes and make them more intuitive, cyber adversaries are also leveraging them to accomplish their own objectives such as AI-enabled phishing emails, botnet attacks, etc.
The digital-first approach will only amplify going forward and the traditional approach of I managing cyber risks – identifying, assessing, monitoring, and responding to potential threats to IT infrastructure – is foundational, but no longer enough.
Today, adopting a risk-based approach to IT and cyber risk management is a business imperative. That means not just identifying and assessing cyber risks but also prioritizing cyber risks, ensuring continuous controls monitoring, and aligning cybersecurity strategy to the overarching enterprise risk management framework.
Building 5 Critical Capabilities for the Future
So, what are the critical capabilities that organizations need to build cyber resilience and become future-ready? Here are 5 key considerations and recommendations.
Automation As cyber attacks become increasingly sophisticated, organizations must continuously augment their cyber risk management programs by adopting advanced technologies and automating wherever possible.
CISOs and security teams must ensure that the deployed software is not only effective but also simplifies cyber threat identification and mitigation.
For instance, manually sifting through past issues to find similar/relevant ones is highly time-consuming and prone to errors.
Implementing an AI-based system can not only accelerate the process but also make it more intuitive by enabling security executives to search for past issues based on intent.
Cyber Risk Quantification In Gartner’s 2021 Board of Directors Survey, 88% of boards said that they now see cybersecurity as a business risk, not just a technology one. It’s at the top of board agendas – and directors are looking to CISOs and CIOs for updates and answers.
That means communicating cyber risk in business terms that make it easy to understand and prioritize risks. Cyber risk metrics, such as detected vulnerabilities and patch response times, intrusion attempts, security incident rates, severity levels, response time, etc., help in risk reporting, but they tend to focus on technical aspects.
Quantifying risk in monetary terms enables CISOs and security teams to better communicate cyber risks and the cybersecurity posture to leadership in business terms all can understand – dollars and cents.
Assigning a dollar value to the risks also helps prioritize and make well-informed cybersecurity investment decisions.
By quantifying the monetary impact of a risk event, you can confidently answer questions like “How much should we invest in cybersecurity?”, “What will be the return on investment?”, and “Do we have enough cyber insurance coverage?”
Power What’s Next by Measuring Cyber Security Risk: A Deep-Dive Guide into Risk Quantification
Creating a Culture of Cybersecurity Awareness Creating a culture of cybersecurity awareness must be a key part of the overall corporate culture and strategy. Particularly in this post-COVID era where business functions and units are undergoing rapid digital transformation, organizations must clearly define security-related roles, responsibilities, and accountability as well as conduct training and workshops to enable cyber risk-aware behavior.
Implementing a strong cyber risk management program is critical here, as metrics and outcomes are clear and can be clearly communicated.
Managing Third and Fourth-Party Risk Recent incidents have highlighted how third-party cyber risks have largely been a blind spot for organizations.
With the growing reliance on third parties and the amplified digital interconnectedness, the exposure of organizations to third-party cyber risks has increased exponentially.
A security incident at one organization can quickly travel and paralyze several other connected organizations.
A cyber risk program is incomplete without a proactive approach to monitoring cyber risks across your extended enterprise – third, fourth, and subsequent parties.
Continuous Monitoring Cyber risk management is a continuous, iterative business process. Organizations must continuously monitor related functions and processes – risk assessments, reporting mechanisms, remediation and mitigation measures, exception management, controls, etc. – to proactively identify gaps or loopholes that might exist and ensure the efficacy of the cyber defense mechanisms.
Continuous control monitoring in particular can provide a competitive edge by constantly scanning security controls – from frameworks like NIST CSF, ISO and more – for effectiveness. Unlike traditional manual testing, continuous control runs autonomously, collecting evidence of control effectiveness so you can stay compliant and identify potential risks.
How MetricStream Can Help
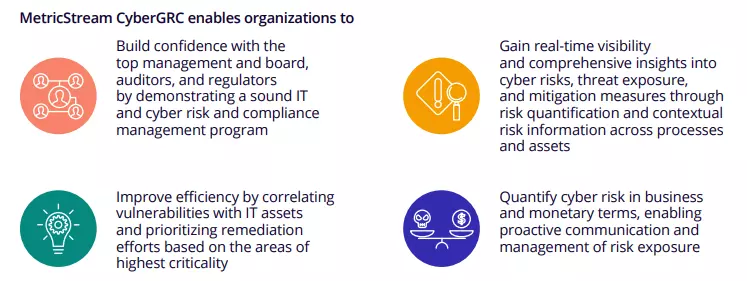
MetricStream enables organizations to streamline cyber governance, risk, and compliance (GRC) management processes with an integrated approach.
With MetricStream CyberGRC, organizations can rapidly implement an IT and cyber risk and compliance framework that is aligned with established security standards and industry best practices. They can leverage pre-packaged content such as ISO 27001, NIST CSF, and NIST SP800-53, to get their IT Compliance program up and running quickly. Furthermore, Advanced Cyber Risk Quantification capabilities enable organizations to accurately determine the monetary impact of cyber risks like data breaches, identity theft, infrastructure downtime, etc. with support from the FAIR® model to better prioritize cyber investments.
Strengthen your cyber risk management and build your cyber program with these five recommendations, along with advanced capabilities and actionable insights. For a personalized consultation or a demo of MetricStream, please contact us contact info@metricstream.com.
It’s a whole new world for managing cyber risk – and the stakes are higher than ever.
According to the Cost of Data Breach Report 2021 by the Ponemon Institute, the average cost of a data breach was $4.24 million in 2021, up from $3.86 million in 2019. Even more surprising, the average breach cost was $1.07 million higher where remote working was a factor. The 2022 report records the highest global cost increase to $4.35 4.35 million, which is a 12.7% increase from the previous year.
As digitization has escalated, cyber adversaries have become increasingly sophisticated and organized to exploit vulnerabilities and carry out damaging attacks.
What’s more, the challenges have gotten significantly worse over the past two years as the pandemic brought a tectonic shift in how businesses operate. The sudden shift to remote work beyond office firewalls and enterprise security mechanisms expanded the attack surface of organizations and made them more vulnerable to breaches.
To quickly adapt to the new normal, organizations rushed to adopt industry 4.0 technologies, such as cloud computing, artificial intelligence, and automated bots. While these technologies help to automate various processes and make them more intuitive, cyber adversaries are also leveraging them to accomplish their own objectives such as AI-enabled phishing emails, botnet attacks, etc.
The digital-first approach will only amplify going forward and the traditional approach of I managing cyber risks – identifying, assessing, monitoring, and responding to potential threats to IT infrastructure – is foundational, but no longer enough.
Today, adopting a risk-based approach to IT and cyber risk management is a business imperative. That means not just identifying and assessing cyber risks but also prioritizing cyber risks, ensuring continuous controls monitoring, and aligning cybersecurity strategy to the overarching enterprise risk management framework.
So, what are the critical capabilities that organizations need to build cyber resilience and become future-ready? Here are 5 key considerations and recommendations.
Automation As cyber attacks become increasingly sophisticated, organizations must continuously augment their cyber risk management programs by adopting advanced technologies and automating wherever possible.
CISOs and security teams must ensure that the deployed software is not only effective but also simplifies cyber threat identification and mitigation.
For instance, manually sifting through past issues to find similar/relevant ones is highly time-consuming and prone to errors.
Implementing an AI-based system can not only accelerate the process but also make it more intuitive by enabling security executives to search for past issues based on intent.
Cyber Risk Quantification In Gartner’s 2021 Board of Directors Survey, 88% of boards said that they now see cybersecurity as a business risk, not just a technology one. It’s at the top of board agendas – and directors are looking to CISOs and CIOs for updates and answers.
That means communicating cyber risk in business terms that make it easy to understand and prioritize risks. Cyber risk metrics, such as detected vulnerabilities and patch response times, intrusion attempts, security incident rates, severity levels, response time, etc., help in risk reporting, but they tend to focus on technical aspects.
Quantifying risk in monetary terms enables CISOs and security teams to better communicate cyber risks and the cybersecurity posture to leadership in business terms all can understand – dollars and cents.
Assigning a dollar value to the risks also helps prioritize and make well-informed cybersecurity investment decisions.
By quantifying the monetary impact of a risk event, you can confidently answer questions like “How much should we invest in cybersecurity?”, “What will be the return on investment?”, and “Do we have enough cyber insurance coverage?”
Power What’s Next by Measuring Cyber Security Risk: A Deep-Dive Guide into Risk Quantification
Creating a Culture of Cybersecurity Awareness Creating a culture of cybersecurity awareness must be a key part of the overall corporate culture and strategy. Particularly in this post-COVID era where business functions and units are undergoing rapid digital transformation, organizations must clearly define security-related roles, responsibilities, and accountability as well as conduct training and workshops to enable cyber risk-aware behavior.
Implementing a strong cyber risk management program is critical here, as metrics and outcomes are clear and can be clearly communicated.
Managing Third and Fourth-Party Risk Recent incidents have highlighted how third-party cyber risks have largely been a blind spot for organizations.
With the growing reliance on third parties and the amplified digital interconnectedness, the exposure of organizations to third-party cyber risks has increased exponentially.
A security incident at one organization can quickly travel and paralyze several other connected organizations.
A cyber risk program is incomplete without a proactive approach to monitoring cyber risks across your extended enterprise – third, fourth, and subsequent parties.
Continuous Monitoring Cyber risk management is a continuous, iterative business process. Organizations must continuously monitor related functions and processes – risk assessments, reporting mechanisms, remediation and mitigation measures, exception management, controls, etc. – to proactively identify gaps or loopholes that might exist and ensure the efficacy of the cyber defense mechanisms.
Continuous control monitoring in particular can provide a competitive edge by constantly scanning security controls – from frameworks like NIST CSF, ISO and more – for effectiveness. Unlike traditional manual testing, continuous control runs autonomously, collecting evidence of control effectiveness so you can stay compliant and identify potential risks.
MetricStream enables organizations to streamline cyber governance, risk, and compliance (GRC) management processes with an integrated approach.
With MetricStream CyberGRC, organizations can rapidly implement an IT and cyber risk and compliance framework that is aligned with established security standards and industry best practices. They can leverage pre-packaged content such as ISO 27001, NIST CSF, and NIST SP800-53, to get their IT Compliance program up and running quickly. Furthermore, Advanced Cyber Risk Quantification capabilities enable organizations to accurately determine the monetary impact of cyber risks like data breaches, identity theft, infrastructure downtime, etc. with support from the FAIR® model to better prioritize cyber investments.

Strengthen your cyber risk management and build your cyber program with these five recommendations, along with advanced capabilities and actionable insights. For a personalized consultation or a demo of MetricStream, please contact us contact info@metricstream.com.








