INTRODUCTION
The countdown to the EU’s Digital Operational Resilience Act (DORA) has begun – and with it, the potential to strengthen the EU financial sector’s resilience against cyber attacks and other digital risks. DORA will harmonize the EU’s existing patchwork of cyber risk and digital resilience regulations, standards, and frameworks by providing a master regulation to govern the security of information and communications technology (ICT) and resilience of the financial sector.
With the frequency of cyber risks and threats increasing, digital operational resilience is now a top priority across financial institutions. A 2022 VMware survey found that 63% of financial institutions from around the world have experienced a rise in destructive cyber attacks on their organizations. Ransomware is particularly rampant with 74% of security leaders reporting one or more ransomware attacks in the past year, and 63% of those victims who were targeted ended up paying the ransom.
The dependency on third and fourth-party risks has significantly amplified for the sector – as much as 98% of financial institutions outsource (at least some) critical IT activities, according to a 2020 research report. This potentially means that a breach anywhere along a third-party network can have a detrimental impact on the overall sector due to the interconnectedness of the financial sector.
So, it’s no surprise that DORA specifically introduces regulatory oversight of critical third-party providers (CTPPs) such as cloud platforms and data analytics services. Financial institutions will be expected to have robust third-party monitoring and incident reporting processes in place. They will also need to expand their digital risk management efforts, deepen penetration testing, and conduct regular business impact analyses based on severe disruption scenarios.
While some organizations may regard DORA as another regulatory hindrance, others will see it for what it is – an opportunity to re-examine their cybersecurity and digital risk management programs. This eBook is intended to help risk, security, and compliance professionals in the EU understand various aspects and requirements of DORA, be better positioned to prevent, withstand, and recover quickly from operational disruptions, and strengthen cyber resilience.
DORA – A Quick Guide
What is DORA?
DORA or the Digital Operational Resilience Act is a new regulation introduced by the European Union, which is aimed at strengthening ICT and digital risk management and promoting digital operational resilience in the EU’s financial sector.
Whom Does It Apply To?
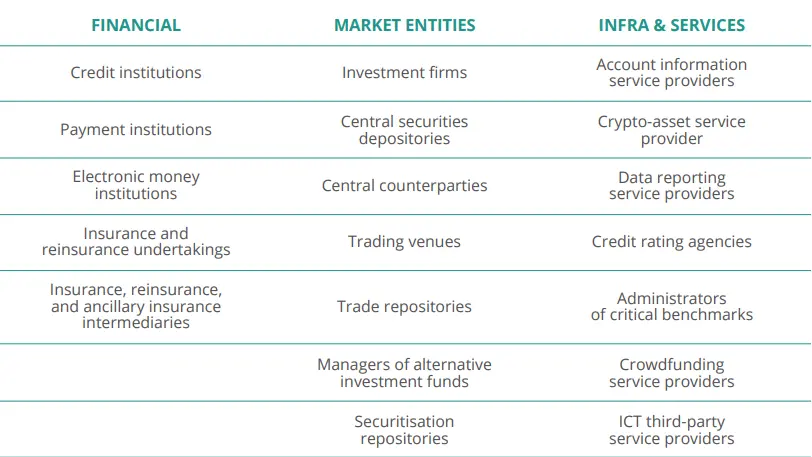
The entire EU financial services industry, including third-party service providers
Why is It Important?
Digitalization opens up both opportunities and risks. To make the most of these opportunities, financial firms need to effectively understand and manage digital risks, especially during times of stress.
What are Its Key Pillars?
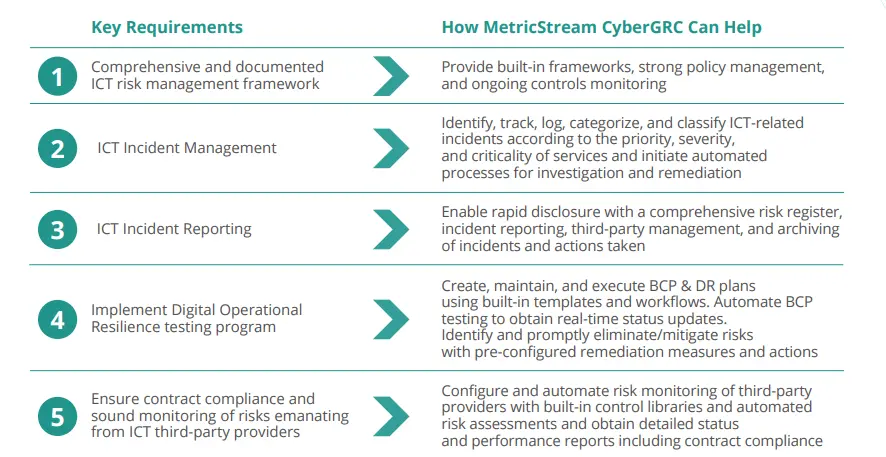
ICT Risk Management Framework
All entities must implement a comprehensive and documented framework to manage the following:
- Strategies, policies, procedures, ICT protocols, and tools
- Digital operational resilience strategy
- ICT business continuity policy
- Response and recovery plans
- Crisis communication process
ICT Incident Management, Classification, and Reporting
This process must include:
- Robust incident tracking systems
- Mechanism to discover and report new incidents quickly
- Ability to preconfigure remediation plans and execute them
- Ability to generate instant reports
- Continuous monitoring capabilities
Digital Operational Resilience Testing
Applicable entities will be required to implement a digital operational resilience testing program that:
- Follows a risk-based approach
- Ensures independent testing
- Includes vulnerability assessments and network security assessments, gap analyses, physical security reviews, source code reviews, scenario-based tests, etc.
Third-Party Provider Risk Management
This process must include:
- Due diligence of third parties as per prescribed standards
- A register of information in relation to all contractual arrangements
- Conformance with contracting standards
- Continuous monitoring of risks
Information Sharing
Applicable entities will be required to implement a system to exchange information relating to threats, indicators of compromise, tactics, techniques, procedures, cyber security alerts, and configuration tools, while protecting the sensitive nature of such information.
When is It Coming?
The European Parliament adopted DORA on 28 November 2022. The Act was enforced on 16 January 2023, and is expected to become applicable with regulated entities required to be compliant by 17 January 2025.
Currently, the European Supervisory Authorities are in the process of collecting and working on public comments and feedback on the four draft regulatory technical standards (RTS) and one set of draft implementing technical standards (ITS). These technical standards aim to ensure a consistent and harmonised legal framework in the areas of ICT risk management, major ICT-related incident reporting and ICT third-party risk management.
Gearing Up For DORA: 5 Steps to Compliance
Rather than scrambling at the last minute to meet the DORA requirements, entities falling under the regulations could benefit from a head-start on the compliance journey. It is important to remember that DORA is only one of many operational resilience regulations around the world. The UK is already hinting at a DORA-equivalent rule to improve the resilience of outsourcing to technology providers in the financial sector. The faster organizations get started on a digital resilience framework, the better prepared they will be to manage the myriad of risks and regulations ahead.
Here are five key steps for financial firms to improve digital resilience and DORA compliance:
- Map out the current state of compliance
- Take stock of your current risk management and compliance measures. Benchmark them against DORA requirements to identify compliance gaps
- Document all critical or important functions (CIFs). Map their assets and dependencies
- Mobilize the investment, resources, and executive buy-in needed for compliance
- Be proactive about risk management
- Identify your cyber risks, operational risks, and digital risks – including risk drivers
- Assess risk probability and impact to determine which risks need to be addressed on priority
- Design and conduct top-down and bottom-up risk assessments at regular intervals with clear lines of risk responsibility and accountability
- Implement controls based on industry-standard frameworks with well-defined test plans and assessments
- Periodically test the security and resilience of critical IT applications. Proactively address any vulnerabilities that are identified
- Clearly articulate risk thresholds for ICT disruptions supported by key risk and performance indicators with automated alerts and continuous monitoring of risk metrics
- Identify and document issues from IT risk assessments to easily initiate an investigation which if required can easily uncover root cause analysis and support speedy remediation
- Set up and maintain consistent procedures for ICT incident identification, triaging, investigation, tracking, reporting, and closure
- Build a unified view of risk
- Establish a consistent taxonomy across the enterprise for digital risks, incidents, and threats
- Map your digital and ICT risks to the corresponding assets, threats, vulnerabilities, business objectives, controls, processes, third parties, and compliance requirements. A clear understanding of these relationships across these data elements will make compliance easier
- Consolidate all risk and control data in a single source of truth for easy monitoring
- Monitor the threat landscape, zero-day advisories, and threat bulletins from industry sources
- Import data from vulnerability scanners and generate a combined risk rating for each asset
- Keep ICT vendor risks in check
- Identify critical third-party ICT service providers. Centrally document all vendor-related information such as services provided, associated business units, certifications, and risk ratings
- Streamline vendor information gathering, due diligence, onboarding, monitoring, and risk assessments. Trigger periodic vendor risk assessments
- Deepen visibility into vendor cyber risks with authoritative intelligence from trusted sources (e.g., Dow Jones, D&B, BitSight, Security Scorecard)
- Capture and track vendor business continuity plans
- Develop an effective business continuity program
- Trigger business impact analysis (BIA) surveys of ICT. Prioritize key assets and processes for recovery
- Perform qualitative and quantitative assessments of business continuity risks
- Create incident response and business continuity plans with clear recovery and response tasks, including crisis communication plans, and timelines. Regularly test these plans to check their effectiveness
How MetricStream Can Help with DORA Compliance
 To learn about how MetricStream CyberGRC can help with DORA compliance, request a personalized demo today
To learn about how MetricStream CyberGRC can help with DORA compliance, request a personalized demo today
The countdown to the EU’s Digital Operational Resilience Act (DORA) has begun – and with it, the potential to strengthen the EU financial sector’s resilience against cyber attacks and other digital risks. DORA will harmonize the EU’s existing patchwork of cyber risk and digital resilience regulations, standards, and frameworks by providing a master regulation to govern the security of information and communications technology (ICT) and resilience of the financial sector.
With the frequency of cyber risks and threats increasing, digital operational resilience is now a top priority across financial institutions. A 2022 VMware survey found that 63% of financial institutions from around the world have experienced a rise in destructive cyber attacks on their organizations. Ransomware is particularly rampant with 74% of security leaders reporting one or more ransomware attacks in the past year, and 63% of those victims who were targeted ended up paying the ransom.
The dependency on third and fourth-party risks has significantly amplified for the sector – as much as 98% of financial institutions outsource (at least some) critical IT activities, according to a 2020 research report. This potentially means that a breach anywhere along a third-party network can have a detrimental impact on the overall sector due to the interconnectedness of the financial sector.
So, it’s no surprise that DORA specifically introduces regulatory oversight of critical third-party providers (CTPPs) such as cloud platforms and data analytics services. Financial institutions will be expected to have robust third-party monitoring and incident reporting processes in place. They will also need to expand their digital risk management efforts, deepen penetration testing, and conduct regular business impact analyses based on severe disruption scenarios.
While some organizations may regard DORA as another regulatory hindrance, others will see it for what it is – an opportunity to re-examine their cybersecurity and digital risk management programs. This eBook is intended to help risk, security, and compliance professionals in the EU understand various aspects and requirements of DORA, be better positioned to prevent, withstand, and recover quickly from operational disruptions, and strengthen cyber resilience.
What is DORA?
DORA or the Digital Operational Resilience Act is a new regulation introduced by the European Union, which is aimed at strengthening ICT and digital risk management and promoting digital operational resilience in the EU’s financial sector.
Whom Does It Apply To?
The entire EU financial services industry, including third-party service providers

Why is It Important?
Digitalization opens up both opportunities and risks. To make the most of these opportunities, financial firms need to effectively understand and manage digital risks, especially during times of stress.
What are Its Key Pillars?
ICT Risk Management Framework
All entities must implement a comprehensive and documented framework to manage the following:
- Strategies, policies, procedures, ICT protocols, and tools
- Digital operational resilience strategy
- ICT business continuity policy
- Response and recovery plans
- Crisis communication process
ICT Incident Management, Classification, and Reporting
This process must include:
- Robust incident tracking systems
- Mechanism to discover and report new incidents quickly
- Ability to preconfigure remediation plans and execute them
- Ability to generate instant reports
- Continuous monitoring capabilities
Digital Operational Resilience Testing
Applicable entities will be required to implement a digital operational resilience testing program that:
- Follows a risk-based approach
- Ensures independent testing
- Includes vulnerability assessments and network security assessments, gap analyses, physical security reviews, source code reviews, scenario-based tests, etc.
Third-Party Provider Risk Management
This process must include:
- Due diligence of third parties as per prescribed standards
- A register of information in relation to all contractual arrangements
- Conformance with contracting standards
- Continuous monitoring of risks
Information Sharing
Applicable entities will be required to implement a system to exchange information relating to threats, indicators of compromise, tactics, techniques, procedures, cyber security alerts, and configuration tools, while protecting the sensitive nature of such information.
When is It Coming?
The European Parliament adopted DORA on 28 November 2022. The Act was enforced on 16 January 2023, and is expected to become applicable with regulated entities required to be compliant by 17 January 2025.
Currently, the European Supervisory Authorities are in the process of collecting and working on public comments and feedback on the four draft regulatory technical standards (RTS) and one set of draft implementing technical standards (ITS). These technical standards aim to ensure a consistent and harmonised legal framework in the areas of ICT risk management, major ICT-related incident reporting and ICT third-party risk management.
Rather than scrambling at the last minute to meet the DORA requirements, entities falling under the regulations could benefit from a head-start on the compliance journey. It is important to remember that DORA is only one of many operational resilience regulations around the world. The UK is already hinting at a DORA-equivalent rule to improve the resilience of outsourcing to technology providers in the financial sector. The faster organizations get started on a digital resilience framework, the better prepared they will be to manage the myriad of risks and regulations ahead.
Here are five key steps for financial firms to improve digital resilience and DORA compliance:
- Map out the current state of compliance
- Take stock of your current risk management and compliance measures. Benchmark them against DORA requirements to identify compliance gaps
- Document all critical or important functions (CIFs). Map their assets and dependencies
- Mobilize the investment, resources, and executive buy-in needed for compliance
- Be proactive about risk management
- Identify your cyber risks, operational risks, and digital risks – including risk drivers
- Assess risk probability and impact to determine which risks need to be addressed on priority
- Design and conduct top-down and bottom-up risk assessments at regular intervals with clear lines of risk responsibility and accountability
- Implement controls based on industry-standard frameworks with well-defined test plans and assessments
- Periodically test the security and resilience of critical IT applications. Proactively address any vulnerabilities that are identified
- Clearly articulate risk thresholds for ICT disruptions supported by key risk and performance indicators with automated alerts and continuous monitoring of risk metrics
- Identify and document issues from IT risk assessments to easily initiate an investigation which if required can easily uncover root cause analysis and support speedy remediation
- Set up and maintain consistent procedures for ICT incident identification, triaging, investigation, tracking, reporting, and closure
- Build a unified view of risk
- Establish a consistent taxonomy across the enterprise for digital risks, incidents, and threats
- Map your digital and ICT risks to the corresponding assets, threats, vulnerabilities, business objectives, controls, processes, third parties, and compliance requirements. A clear understanding of these relationships across these data elements will make compliance easier
- Consolidate all risk and control data in a single source of truth for easy monitoring
- Monitor the threat landscape, zero-day advisories, and threat bulletins from industry sources
- Import data from vulnerability scanners and generate a combined risk rating for each asset
- Keep ICT vendor risks in check
- Identify critical third-party ICT service providers. Centrally document all vendor-related information such as services provided, associated business units, certifications, and risk ratings
- Streamline vendor information gathering, due diligence, onboarding, monitoring, and risk assessments. Trigger periodic vendor risk assessments
- Deepen visibility into vendor cyber risks with authoritative intelligence from trusted sources (e.g., Dow Jones, D&B, BitSight, Security Scorecard)
- Capture and track vendor business continuity plans
- Develop an effective business continuity program
- Trigger business impact analysis (BIA) surveys of ICT. Prioritize key assets and processes for recovery
- Perform qualitative and quantitative assessments of business continuity risks
- Create incident response and business continuity plans with clear recovery and response tasks, including crisis communication plans, and timelines. Regularly test these plans to check their effectiveness
 To learn about how MetricStream CyberGRC can help with DORA compliance, request a personalized demo today
To learn about how MetricStream CyberGRC can help with DORA compliance, request a personalized demo today








